What is Malware? Viruses, worms, trojans
What is Malware?
Malware is small malicious software, which means software can be used to compromise computer functions, steal data, bypass access control, or otherwise damage the host computer.
Malware is a comprehensive term that refers to various types of malicious programs.
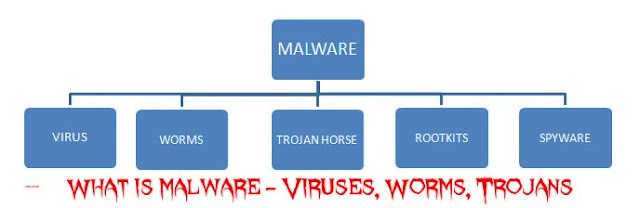
This post will define many of the most common types of Malware; worm, virus, trojan, rootkits, spyware, Trojan horses, ransomware and rootkit.
Types of malware
This means, what is the difference between Malware and virus, the question is that a virus is a type of Malware, so all viruses are malware (but not every piece of malware is a virus).
1. A worm is a standalone piece of malicious software that regenerates itself and spreads from computer to computer.
2. A virus is a piece of computer code that puts itself in the code of another standalone program, then forces that program to perform malicious actions and to spread itself.
3. A trojan is a program that can not reproduce itself, but the user masked what he wants and drives them to activate it so that it can damage and propagate
Malware can also be installed on a computer "manually" on a computer by using a privilege enhancement to gain physical access to the computer or to gain remote administrator access.
Trojan horse
A Trojan horse, commonly known as "Trojan", is a type of malware that allows users to download and install malware as a normal file or program in order to deceive users.
A Trojan can provide a malicious party remote access to infected computers.
Once the attacker has access to an infected computer, steal data (logging, financial data, bank money) for the attacker, installing more malware, modifying files, user activity It is possible to use monitoring (screen viewing, screenshot, etc.) in computers in the botnet, and anonymous internet activity by the attacker.
Spyware
Spyware is a type of malware that works without user knowledge by spying on user knowledge.
These detective capabilities may include activity monitoring, keystroke collection, data harvesting (account information, login, password), etc.
Spyware often also has additional connections, ranging from modifying the software or browser's security settings to interfere with the network connection Spyware exploits software vulnerabilities, bundles itself with legitimate software or spreads in a trojan
Rootkit
A Rootkit is a type of malicious software designed to remote access or control the computer without users or security programs. Once the Rootkit is installed, it is possible to remotely execute files for malicious party behind the rootkit, access information, steal, modify system configuration, change software install hidden malware or control the computer as part of a bonnet.
Rootkit prevention, detection, and removal can be difficult due to their stealth operation. Since the rootkit constantly hides its presence, therefore the general safety products are not effective in detecting and removing rootkits.
As a result, rootkit identification depends on manual methods such as monitoring computer behavior for irregular activity, signature scanning, and storage dump analysis.
Organizations and user software, apps and operating systems can regularly protect from rootkits by patches vulnerabilities, updating virus definitions, avoiding suspicious downloads and scanning static analyzes.
Ransomware
Ransomware is a form of malware that essentially keeps computer system captive when seeking a ransom. Access the computer to the computer with a purpose to force malware to encrypt files on the hard drive or to lock the system and display the messages to computer the user to pay the malware creator and access their computer.
Restricts. Ransomware typically spreads like a computer worms on a computer via a download computer or through another vulnerability in any network service.
adware
Adware is a type of Malware that automatically distributes ads. Common examples of adware include pop-up advertisements on websites and advertisements that are displayed by software. Often software and applications provide "free" versions that are bundled with adware.
Most adware is sponsored or written by advertisers and acts as revenue generating tools. Although some adware is fully designed to deliver ads but to bundle with spyware
How To Secure Computers With Viruses, Verms And Trojan Horse
1. Keep the operating system updated
The first step in protecting your computer from any maliciousness is to ensure that your operating system (OS) is up to date.
If you are running Microsoft Windows OS, then it is necessary. Second, you need to install anti-virus software on your system and you often download updates to make sure that your software has the latest fixes for new viruses, worms, and Trojan horses.
In addition, you want to make sure that your anti-virus program has the ability to scan the e-mails and files downloaded from the Internet, and you also need to run full disk scans from time to time.
This will help prevent malicious programs from accessing your computer.
2. Use a firewall
You should also install a firewall A firewall is a system that prevents unauthorized access and access to your computer. A firewall can be either hardware or software.
Hardware firewalls provide a strong degree of security from most forms of attack coming from the outside world and can be purchased in standalone product or broadband router.
Unfortunately, while battling viruses, worms, and trojans, a hardware firewall software may be less effective than a firewall, because it can ignore the embedded insects in potential e-mail and see it as regular network traffic.
It is important to remember that you are not getting rid of the problems of your computer virus on your own firewall, but when using regular operating system updates and a good anti-virus scanning software, this is something Additional security and security will Safe your computer or network.
Tags: what is malware,what is malware?,trojan,trojans,what are virus?,what is worm,what is virus,what is trojan horse,what is spyware,what are malwares,what is virus in hindi,what is trojan,what is trojan virus,what is trojan horse virus,trojan horse,malware,what is worms,what is adware,whats is malware spyware worm trojan,what,virus,what is virus and trojan,trojan virus,worms,what is trojan hourse


.png)














No comments:
Post a Comment