OWASP Tutorials - The OWASP Testing Framework
This section describes a specific
It can be seen as a reference framework, which includes techniques and functions that are suitable at various stages of the software development life cycle (SDLC).
Companies and project teams can use this model to develop their own testing framework and to scope for testing services from vendors.
This structure should not be seen as a precipitative but can be seen as a flexible approach that can be enhanced and molded to fit an organization's Development process and culture.
The purpose of this section is to help organizations to make a full strategic The testing process, and which is not intended for consultants or contractors The trial is engaged in more strategic, specific areas.
It is important to understand why an end-to-end test is made
The framework is important for assessing and improving software security.
In writing secure code, Howard and LeBlanc said that in releasing a security bulletin, Microsoft costs at least $ 100,000, and this is their cost. Clients are more than complying to collective security
Patches
He also said that the U.S. government's cybercrime web
Site (
Damage to criminal cases and organizations. Specific losses are more than $ 100,000 so far.
With such economics, it is little wonder why the software vendor
Completely display black box safety test, which can
Only to be performed on applications that have already been developed, to focus on testing in the initial chapters of the application Development, such as definition, design, and development.
Many safety practitioners still see safety testing in the radius
penetration Testing.
As discussed earlier, while the entrance test is played, it is usually unable to find the bug and depends heavily on the tester's skill.
It should be considered only as an implementation technique, or to raise awareness of production issues. To improve the security of applications, the security quality of the software should be improved.
This means testing the security in definition, design, development, deployment, and maintenance stages, and do not rely on the expensive strategy of waiting until the code is fully formed.
As discussed at the beginning of this document, there are many
Methods of development, such as the rational integrated process,
eXtreme and agile development, and traditional waterfall system.
The objective of this guide is neither to suggest any particular development method nor provide specific guidance to follow a particular method.
Instead, we are presenting a generic The development model and the reader must follow it according to their company's process.
There are the following activities in this test structure.
Should take place:
- Before development begins
- During definition and design
- During development
- During the deployment
- Maintenance and operation
Step 1: Before Development Begins
Define an SDLC
There should be an adequate SDLC before application development begins It has been defined that where protection lies in each stage.
Review policies and standards
Ensure that there are appropriate policies, standards, and documentation.
Documentation is very important because it gives guidelines and policies to development teams they can follow.
People can do the right thing only if they know what is the right thing.
If the application is to be developed in Java, then it is necessary that there There is a Java Secure coding standard.
If the application needs to use cryptography, then it is important that cryptography is standard.
No policy or standard can cover every stage of development The team will face.
By documenting general and predictable issues, There will be fewer decisions that need to be made during the development process.
Develop the Measurement and Metrics Criteria and Sure Detection ability
Before development begins, plan a measurement program. by
Requirements need to be defined, it provides visibility
Fault in both process and product
It is necessary to define Before the development begins, the metrics may need to be done in the form of Modify the process to capture data.
Step 2: During Definition and Design
Review of Security Requirements
Defines safety requirements, how an application works from a security perspective.
It is necessary that there are safety requirements Tested. The test, in this case, means that testing the assumptions Requirements and testing have been made to see if there are an interval Definitions of requirements
For example, if there is a security requirement that tells users
Before they can access the Whitepaper section of any website, it must be registered, does it mean that the user must be registered with the system or should the user be certified?
Make sure the requirements are as clear as possible.
While looking for the gap requirements, consider looking at security A mechanism such as:
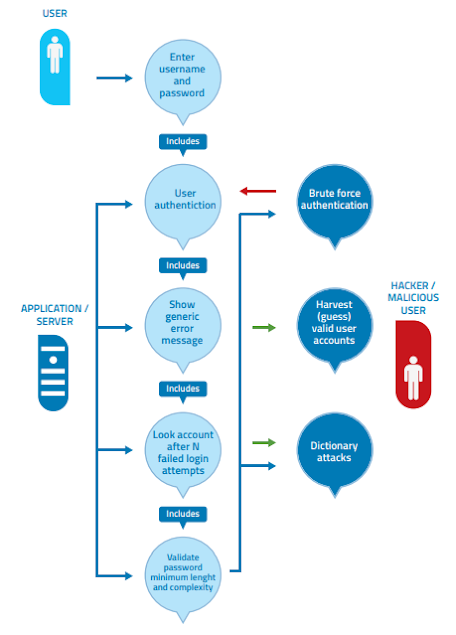
• User Management
• Authentication
• Authorization
• Data privacy
• Integrity
• Accountability
• Session management
• Transportation safety
• Tiered system isolation
• Legislative and standard compliance (including privacy)
Government and industry standards)
Review Design and Architecture
Applications should have a documented design and architecture.
This document may include models, text documents, and
Other similar artifacts.
It is necessary to test these artifacts to ensure that the design and architecture requirements apply to the appropriate level of security defined.
Identifying safety flaws in the design phase is not only one
Most cost-efficient places to identify flaws, but one can be
The most effective place to make changes
For example, if it is recognized that the design asks for authorization decisions in many places, it may be appropriate to consider the central authority component.
If the app is verifying data at multiple locations, it may be appropriate to develop the central verification framework (eg, fixing the input validation in one place, but at hundreds of places, is very cheap).
If the vulnerabilities are discovered, then the system must be given to the architect for an alternative approach.
Create a UML Model and Review
Once the design and architecture is complete, create Unified
Modeling Language (UML) models that describe how the application works. In some cases, these may already be available.
Use these models to conform with system designers
Understanding how the application works.
If vulnerabilities are discovered, they should be given to the system architect for an alternative approach.
Build and Review Danger Models
Armed with Design and Architectural Review and UML Model
Actually stating how the system works, a threat modeling exercise. Develop realistic danger scenarios.
Analyze the design and architecture to ensure that these hazards have been reduced, have been accepted by the business, or have been assigned to third parties such as an insurance company.
When there is no strategy of mitigation in identified threats, then revise the design and architecture with the system architect to modify the design.
Step 3: During Development
Theoretically, development is the implementation of a design.
However, in the real world, many design decisions are made during code development.
These are often small decisions that were either elaborate to be described in the design or such issues where no policy or standard guidance was given.
If the design and architecture were not enough, the developer would have to face many decisions.
If there were insufficient policies and standards then the developer would have to face even more decisions.
Walk Through Code
The security team should walk a code Developers, and in some cases, system architects.
A code is a high-level walkthrough of the Walkthrough code, where developers can interpret the logic and flow of the implemented code.
This code allows the review team to get a general understanding of the code and allows the developers to explain how some things were developed.
The purpose is not to review code but to understand the High-level flow, layout, and structure of the code Application.
Code Review
With a good understanding of how the code is structured And why some things were way to code, testers Now can check the actual code for security flaws.
Static code reviews validate the code against a set of the checklist,
Including:
- Business Requirements for availability, privacy, and Integrity
- Top 10 checklist for OWASP guide or technical performance (Depends on the depth of the review).
- Specific issues related to language or usage, such as As Scarlet Paper for PHP or Microsoft Secure Coding Checklist For ASP.NET
- Any industry-specific requirements, such as the Sarbanes-Oxley 404, COPPA, ISO / IEC 27002, APRA, HIPAA, Visa Trader Guidelines, Or other regulatory rules
In terms of returns on invested resources (most of the time), static codes Reviews produce higher quality returns than any other security Trust the review method and critics at least
However, they are not a silver bullet and need to carefully consider within the full spectrum testing regime.
For more information on OWASP checklist, please see the OWASP guide For the latest version of Secure Web App or OWASP Top 10
Step 4: During Deployment
Application Access Test
After testing the requirements, analyzing the design, and reviewing code, it can be assumed that all the issues have happened caught up.
Hopefully, this is the case, but after registering the application, the penetration testing provides a final check to make sure
That nothing has been missed.
Configuration Management Test
How to apply in the entrance test application should include
The infrastructure was deployed and secured.
Although the application may be safe, a small aspect of the configuration can still be on a default install stage and may be vulnerable to exploitation.
Step 5: Maintenance and Operation
Operations Management Reviews
There is a need to have a process that explains how to manage the operational aspects of both the application and the infrastructure.
Conducting health check-ups from time to time
Monthly or quarterly health check should be done on both
Application and infrastructure to ensure a new security risk
Has been introduced and the safety level is still intact.
Ensure Change Verification
Every change in the QA environment has been approved and after the test has been deployed in the production environment, it is important Changes are checked to ensure that the security level is
Not affected by the change
It should be integrated into the change management process.