OWASP Tutorials - Testing Techniques Explained
This section presents a high-level overview of various
It does not present specific methods for these Techniques. This section has been included to provide references for the designs presented in the next
- Manual inspection and review
- Threatening Modeling
- Code review
- Penetration Testing
Manual Inspection and Review of OWASP Testing
Manual inspection is a human review which generally tests the safety implications of people, policies, and procedures.
The manual inspection may include inspection of technology decisions such as architectural design.
They are usually conducted by analyzing the documentation or documentation with designers or system owners.
While the concept of manual inspection and human review is simple, they can be among the most powerful and effective techniques available.
When someone asks how something works and why it has been implemented in a specific way, the examiner can quickly determine whether any security concerns are likely to be obvious.
Manual inspection and review software development are one of the few ways to test the life-cycle process and to ensure that adequate policy or skill has been set in place.
While doing manual inspection and review with many things in life, it is recommended that a trust-but-verified model be adopted. It is not everything that has been shown or told to the tester, it will be accurate.
Manual review is particularly good for testing whether people understand safety procedures, have been made aware of the policy, and have the appropriate skills to design or implement a secure application.
Manually review the documentation, secure coding policies, safety requirements, and other activities, including architectural design, should be completed using manual inspections.
Advantages:
- Need some supportive technology
- Can be implemented for different types
- Flexible
- Promotes teamwork
- Early in SDLC
Disadvantages:
- It may take time
- Supporting material is not always available
- Important human ideas and skills are needed to be effective
Threat Modeling
Threat modeling has become a popular technique, which will help system designers to think about security threats that can withstand their systems and applications.
Therefore, modeling can be seen as a risk assessment for applications.
In fact, it enables the designer to develop mitigation strategies for potential vulnerabilities and helps them focus on their essentially limited resources and those parts of the system which are most needed.
It is recommended that a hazard model is developed and documented in all applications.
The SDLC should be prepared as soon as possible threat model, and the application should be revived as the development progress and progress.
To develop the hazard model, we recommend taking a simple approach that follows the NIST 800-30 standard for risk assessment. This approach includes:
- Deletion of application - Use a process of manual inspection to understand how the application works, its assets, functionality, and connectivity.
- Defining and classifying assets - classify assets into tangible and intangible assets and rank them according to business importance.
- Discover potential vulnerabilities - whether technical, operational or management
- Exploring potential threats - Developing an actual outlook of potential attacker vectors from an attacker's point of view, using threat scenarios or attacking trees.
- Creating mitigation strategies - Develop mitigation controls for each hazard identified as realistic.
The Output can vary from a hazardous model, but there is usually a collection of lists and diagrams.
The OWASP Code Review Guide outlines an application throat modeling methodology that can be used as a reference for testing tests of potential security flaws in the design of the application.
There is no right or wrong way to develop risk models and assess risks on applications.
Advantages:
- Practical attacker's approach to the system
- Flexible
- Early in SDLC
Disadvantages:
- Relatively new technology
- Good threat model does not mean good software
Source Code Review
The review of the source code is the process of manually checking the source code of the web application for security problems.
Many serious security vulnerabilities cannot be diagnosed with analysis or any other form of testing.
As the popular saying is "If you want to know what is really happening, go straight to the source." Almost all security experts agree that there is no alternative to actually viewing the code.
All information is somewhere in the code to identify security problems. Unlike testing, the third party closed
Software such as operating systems, when testing web applications (especially if they have been developed at home), the source code should be made available for testing purposes.
Many unknowingly but important security problems are also extremely difficult to find, with the analysis or other forms of testing, such as penetration testing, source code analysis, making the technique of choice for technical testing.
With the source code, a tester can accurately determine what is happening (or is being considered) and the black box test estimates work out.
Examples of issues specifically found through source code reviews include concurrency problems, inaccurate business logic, access control problems, and cryptographic vulnerabilities, as well as backdoors, trojans, easter eggs, time bombs, logic bombs and other types of malicious code.
These problems often appear as the most harmful vulnerabilities in web sites.
Source code analysis can also be extremely efficient in finding implementation issues, such as at places where input was not verified or unsuccessful open control procedures may exist.
But keep in mind that operational procedures should also be reviewed, as the source code being deployed cannot be the same as it is being analyzed here.
Advantages:
- Completion and Effectiveness
- Accuracy
- Fast (for competent reviewers)
Disadvantages:
- Highly skilled security developers are required
- Recall issues in compiled libraries
- Can not easily detect run-time errors
- The source code actually posted may be different from being analyzed.
For more information on code review, check out the OWASP Code Review Project.
Penetration Testing
Penetrating testing is a common technique used for testing network security for many years. It is also commonly known as black-box testing or ethical hacking.
Penetrating testing is essentially the "art" of the far-running application to detect security vulnerabilities, without knowing the internal functioning of the application.
Typically, the entrance exam team will have access to an app such that they were users.
The tester works like an attacker and attempts to find and exploit weaknesses. In many cases, the tester will be given a valid account on the system.
While penetration testing in network security has proved to be effective, the technique does not translate naturally into applications.
When penetration testing is done on the network and operating system, most of the tasks are involved in detecting and exploiting known weaknesses in specific technologies.
As web applications are almost bespoke exclusively, penetration testing in the web application area is similar to more pure research.
Entrance test tools have been developed which automate the process, but their effectiveness with the nature of web applications is generally poor.
Many people today use the web application login test as their primary security testing technique. Whenever it definitely holds its place in a test program, we do not think it should be considered primary or only testing techniques.
Gary McGrath told the entrance test well when he said, "If you fail in an entrance exam, then you know that you really have a very bad problem.
If you pass an entrance exam, then You do not know that you do not have a very bad problem. "However, concentrated penetration testing (i.e., the test which attempts to take advantage of known weaknesses in previous reviews ) It may be useful to find out if certain vulnerabilities have been fixed in the source code posted on the web site.
Advantages:
- Can be fast (and therefore cheap).
- Comparatively less skill set is needed than reviewing source code
- Examines the code that is actually exposed
Disadvantages:
- SDLC is too late.
- Front effect test only.
The Need for a Balanced Approach
With many techniques and approaches to test the safety of
Web applications can be difficult to understand which technologies are To use and when to use them.
Experience shows that it is not Correct answer or wrong answer to the question of technology The test should be used to build the structure.
In fact, all techniques should be used to test all those areas that need to be tested.
Although it is clear that there is no single technique that can be
Effectively to cover all the security tests and to ensure it was performed All issues have been noticed, many companies adopt only one point of view.
Historically used approaches are approaching Test
Penetration tests, although useful, can not effectively address many problems that need to be checked. It is just "too late" in the Software Development Life Cycle (SDLC).
A right approach is a balanced approach that involves many
From technology, manual reviews to technical tests Balanced
The approach should cover the testing at all stages of SDLC.
This approach takes advantage of the most suitable techniques available on the basis of the current SDLC phase.
Of course, there are times and situations where only one technique is possible.
For example, a test on a web application is already made, but where the trial party does not have access to the source code.
In this case, admission testing is clearly better without any test.
However, challenge parties should be encouraged to challenge theories, such as not accessing the source code, and to explore the possibility of more complete testing.
A balanced approach depends on many factors, such as the testing process and maturity of the corporate culture.
It is recommended that a balanced test framework should look like the representation shown in Figure 3 and Figure 4.
The following figure shows a normal proportional representation Software development has been kept on the life cycle.
Keeping in mind the research and experience, it is essential that companies put more emphasis on the early stages of development.
The following figure shows a specific proportional representation
Overlaid on testing techniques.
The Web Application Scanners
Many organizations have started using automatic web apps
Scanner Although he is undoubtedly a place in a test program,
Some fundamental issues need to be highlighted because it is believed that automating the black box test (or never will) is effective.
However, highlighting these issues should not discourage the use of web app scanners.
Rather, its purpose is to ensure that the boundaries are understood and the test structure should be properly employed.
Important: OWASP is currently working to develop a web application Scanner benchmarking platform. The following examples show why Automatic black box test is not effective.
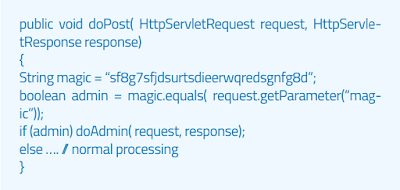
‘Example 1: Magic Parameters’
Imagine a simple web app that accepts a name-value pair
"Magic" and then value. For simplicity, the GET request may be:
To make the case easier, in this case, the value can only be ASCII characters a - z (upper or lower part) and integer 0 - 9.
Designers of this application created an administrative backdoor
During the test, but interrupted it to prevent an accidental supervisor Its exploration By submitting the value sf8g7sfjdsurtsdieerwqredsgnfg8d (30 characters), the user will then be logged in and presented With an administrative screen with total control of the application.
Given that all other parameters were simple-and It is not possible to guess the combination on the three-letter field, about 28 characters. Will be a web app scanner There is a need to put force (or estimates) in the entire primary position of 30 characters.
It is up to 30 ^ 28, or trillions of HTTP requests. That
There is an electron in a digital his toot.
This exemplary magic parameter may look like code for checking
Following:
By looking at the code, vulnerability is practically out of the page
As a potential problem.
Example 2: Bad cryptography
Cryptography is widely used in web applications. Imagine a developer decided to write a simple cryptography algorithm to sign the user Automatically by site A to Site B In her knowledge, the developer Determines if a user is logged into Site A, they will generate A key that uses the MD5 hash function, which includes: hash {username: date }
When a user goes to Site B, they will send the key to the query
String for site b in an HTTP redirect. Site B calculates independently Hash and compares it with a hash passed on request. If they Match, site B signs the user as the user who they claim to be.
As it has been said about this plan, the inadequacies can be worked out. Anyone who detects the plan (or is told how it works or downloads it Information from Bugtraq) can be logged as any user.
Manual inspection, such as a review or code inspection, must have exposed it Security issue quickly There will be no black box web app scanner The vulnerability is highlighted.
It must have seen the 128-bit hash That changed with each user, and the nature of the hash function, done No change in the way of forecast
Static Source Code Review Tools
Many organizations have started using the stable source code scanner.
However, undoubtedly he has got a place in a comprehensive test program, so it is necessary to highlight some basic issues
This approach is not effective when used alone.
Static source code analysis alone cannot identify issues due to flaws in the design It cannot understand the context in which the code has been created.
Source code analysis tools are useful in determining security issues
Due to coding errors, however important manual effort is required
Validate the findings.


.png)

















No comments:
Post a Comment