Ethical Hacking Tutorials - Web Security and Privacy
Fundamentals of Web Security
What you are doing on the global World Wide Web is your business. more or less you'd assume. however, it's simply not true. What you are doing on the online is regarding as personal and anonymous as wherever you go after you leave the house.
Again, you'd assume that it is your business and lots of, as well as ISECOM, would believe you. However, take into account a personal investigator following you around the city, writing down what you saw and WHO you spoke with.
The focus of this lesson is to urge you to find out how to guard yourself online and to try to that, you may need to learn wherever the hazards square measure.
The World Wide Web works terribly} very straight-forward manner. Once connected to the web through your ISP, you open a browser, tell it a web site, and you get that web site on your screen. However, the reality is within the details. however will the online extremely work?
So what happens for real after you simply wish to urge to the ISECOM website? presumptuous you're already connected to the web, here square measure the steps that occur in order:
The focus of this lesson is to urge you to find out how to guard yourself online and to try to that, you may need to learn wherever the hazards square measure.
The World Wide Web works terribly} very straight-forward manner. Once connected to the web through your ISP, you open a browser, tell it a web site, and you get that web site on your screen. However, the reality is within the details. however will the online extremely work?
How the Web Really Works
The steps concerned in connecting to the web so to the online square measure terribly elaborated though it will appear to be sleek from the user finish.So what happens for real after you simply wish to urge to the ISECOM website? presumptuous you're already connected to the web, here square measure the steps that occur in order:
- You open your browser.
- You type the URL (the name of the website).
- Name of the website saved in the history cache on the hard disk.
- Your computer looks at the name of the address to find your default DNS server IP address
- Your computer connects to the server at the IP address provided by default If you use "HTTPS: //" then 80 TCP web ports if you use "HTTP: //" or 443 TCP By the name of the webserver (by the way, there are other steps if you use HTTPS Server certificate, which we will not follow in this example).
- Your computer requests a page or directory that you specify by default If you do not specify anything then "index.htm". But the default of server t is fixed And not your browser.
- The pages are stored in the cache on your hard disk. Even if you ask it to be stored Information in memory (RAM), a good chance that it will end somewhere Your disc is either in a profile or in a sweeper
- The browser is almost immediately showing you what he has stored. Again, there is one The difference between "perceived speed" and "real speed" of your web surfing The difference between what is actually downloaded some faster (Real) and how fast your browser and graphics card can present the page and Graphics and show them to you (perceived). Just because you did not see it This means that it has not ended in your browser cache.
Over the succeeding few years, Tim Berners-Lee continued to develop the system till in 1993 CERN proclaimed that the online was free for anyone to use, and also the Web as we all know it currently exploded onto the scene.
The Web could be a shopper and server primarily based idea, with shoppers like the net individual, Firefox, Mozilla, Opera, browser et al connecting to Web servers like IIS and Apache that offer them contained within the variety of HTML2 pages.
The Web could be a shopper and server primarily based idea, with shoppers like the net individual, Firefox, Mozilla, Opera, browser et al connecting to Web servers like IIS and Apache that offer them contained within the variety of HTML2 pages.
Several corporations, organizations, and people have collections of pages hosted on servers delivering massive|an outsized|an oversized} quantity of data to the globe at large.
So why can we care regarding
So why can we care regarding
Web Servers
What you do not wish to try to do is leave the window open in order that any passerby will reach in and take what they require without charge, and you ideally wish to create certain that if somebody throws a brick, that the window does not shatter! sadly
Web servers square measure complicated programs, and per se have a high likelihood of containing a variety of bugs, and these square measures exploited by the less scrupulous members of society to urge access to knowledge that they should not be seeing.
And the reverse is true likewise. There square measure risks conjointly related to the shopper facet of the equation like your browser.
And the reverse is true likewise. There square measure risks conjointly related to the shopper facet of the equation like your browser.
There square measure variety of vulnerabilities that are discovered within the last year which permit a malicious computing machine to compromise the safety of a shopper machine creating an affiliation to them.
Rattling the Locks
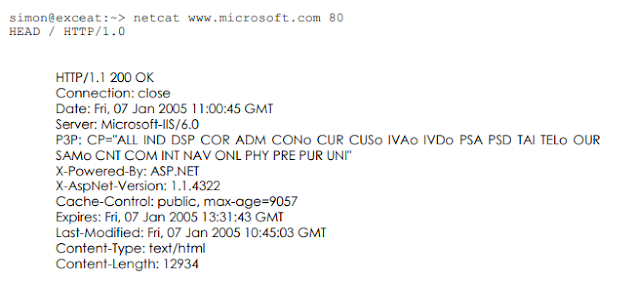
Standard hypertext markup language pages square measure transferred victimization HTTP3, this normal protocol {based|based mostly|primarily based} protocol is obvious text-based and this suggests that we will create connections to a server simply victimization tools like “telnet” or “netcat”. we will use this facility to realize a good deal of data regarding what package is running on a particular server. for instance :
Rattling the Locks
Standard hypertext markup language pages square measure transferred victimization HTTP3, this normal protocol {based|based mostly|primarily based} protocol is obvious text-based and this suggests that we will create connections to a server simply victimization tools like “telnet” or “netcat”. we will use this facility to realize a good deal of data regarding what package is running on a particular server. for instance :
- Centre Européen pour la elegant Nucléaire (European Centre for Nuclear Research)
- Hyper Text nomenclature
- HyperText Transfer Protocol
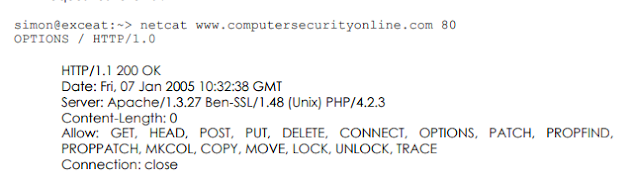
You can take this more and acquire a lot of info by victimization the “OPTIONS” request within the HTTP request as follows:
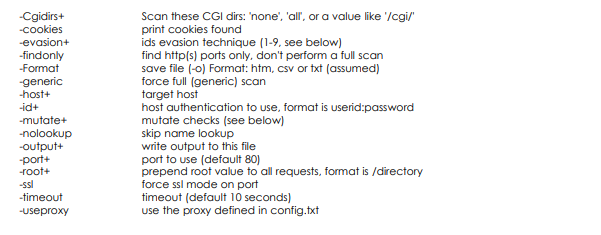
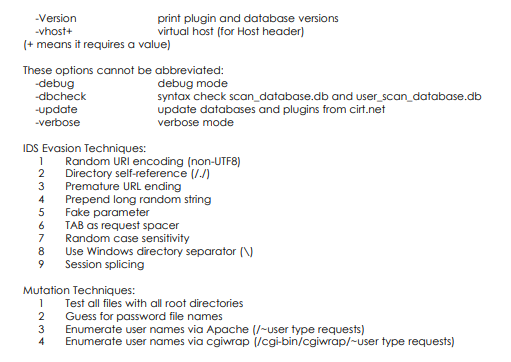
Doing all of this by hand is very tedious, and matching it manually against the information of know signatures and vulnerabilities is quite anyone would wish to try to to. fortuitously for North American nation, some terribly enterprising individuals have return up with an automatic resolution referred to as “Nikto”.
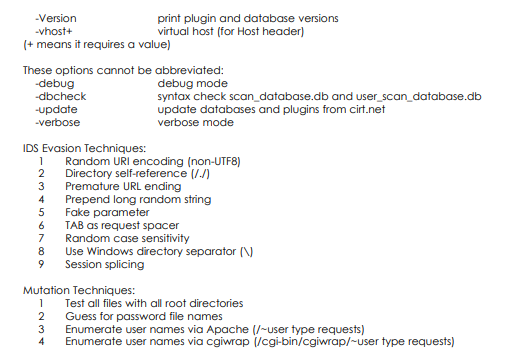
“Nikto” could be a Perl script that carries out varied tests automagically ! the choices square measure as follows:
including stealing, mutation, and cookie detection.
Looking through Tinted Windows - SSL
It wasn't too long before everybody complete that protocol in plain text wasn't a lot of sensible for security. therefore the next variation was to use coding to that.
This comes within the variety of SSL4 and could be a fairly secure forty or 128 bit public key coding technique. employing a forty-bit key's a great deal less secure than the 128 bit and, with specialized hardware, maybe brute force breakable among a number of minutes, wherever because the 128-bit key can still take longer than the age of the Universe to interrupt by brute force.
There square measure but a lot of complicated technical attacks victimization one thing referred to as a familiar cyphertext attack – this concerned scheming the encryption key by analyzing an oversized variety of messages ( > one million ) to deduce the key.
In any case, you are not reaching to be speeding to undertake and crack 128-bit coding – thus what will we tend to learn about SSL protocol Servers?
Quite a heap truly. because the SSL just encrypts the quality protocol traffic, if we tend to established AN SSL the tunnel, we will question the server as we tend to do in section one.1. making AN SSL tunnel is sort of straight forward, and there's a utility referred to as “tunnel” strictly for this purpose. Enter the following into a file referred to as a tunnel.conf, (replacing SSL.enabled.host with the name of the SSL the server that you simply wish to attach to:
client=yes
verify=0
[psuedo-https]
accept = eighty
connect = ssl.enabled.host:443
TIMEOUTclose = 0
Stunnel can then map the native port eighty to the remote SSL Port 443 and can pass out plain text, so you'll hook up with it victimization any of the strategies listed on top of :
Having someone else do it for you – Proxies
Proxies square measure middlemen within the protocol dealing method. The shopper requests the proxy, the proxy requests the server, the server responds to the proxy so the proxy finally passes back the request to the shopper, finishing the dealing.
Quite a heap truly. because the SSL just encrypts the quality protocol traffic, if we tend to established AN SSL the tunnel, we will question the server as we tend to do in section one.1. making AN SSL tunnel is sort of straight forward, and there's a utility referred to as “tunnel” strictly for this purpose. Enter the following into a file referred to as a tunnel.conf, (replacing SSL.enabled.host with the name of the SSL the server that you simply wish to attach to:
client=yes
verify=0
[psuedo-https]
accept = eighty
connect = ssl.enabled.host:443
TIMEOUTclose = 0
Stunnel can then map the native port eighty to the remote SSL Port 443 and can pass out plain text, so you'll hook up with it victimization any of the strategies listed on top of :
Proxies square measure middlemen within the protocol dealing method. The shopper requests the proxy, the proxy requests the server, the server responds to the proxy so the proxy finally passes back the request to the shopper, finishing the dealing.
Proxy servers square measure at risk of attacks in themselves and are capable of being a jumping-off purpose for launching attacks onto other Web servers. they will but increase security by filtering connections, each to and from servers.
The simplicity of giving somebody one thing that they elicit is created rather more complicated when you are within the business of commerce.
Web Vulnerabilities
The simplicity of giving somebody one thing that they elicit is created rather more complicated when you are within the business of commerce.
Web sites that sell to you, corporations commerce merchandise, bloggers commerce concepts, and temperament, or newspapers commerce news, needs quite simply HTML-encoded text and photos.
Dynamic web content that assists you to decide what to elicit, show you alternatives, advocate alternative choices, upsell add-ons, and solely provide you with what you pay for need complicated package.
Once we say adios to Web sites and how-do-you-do to web applications we tend to square measure during a whole new world of security issues.
Many scripting languages are accustomed to developing applications that permit businesses to bring their merchandise or services to the online. tho' this is often nice for the proliferation of businesses, it conjointly creates a replacement avenue of attack for hackers.
Scripting Languages
Many scripting languages are accustomed to developing applications that permit businesses to bring their merchandise or services to the online. tho' this is often nice for the proliferation of businesses, it conjointly creates a replacement avenue of attack for hackers.
The bulk of Web application vulnerabilities return not from bugs within the chosen language however within the strategies and procedures accustomed to develop the online application likewise as however the online server was configured.
for instance, if a kind requests a zipper code and also the user enters “abcde”, the application could fail if the developer failed to properly validate incoming kind knowledge.
Several languages may be used for making Web applications, as well as CGIs, PHP and ASP.
Web applications don't essentially have their own special forms of issues however they are doing have a number of their own terms for issues as they seem online.
- Common Gateway Interface (CGI): server to pass an online user’s request to AN applications program and to receive knowledge back to forward to the user.” CGI is a component of the web’s machine-readable text Transfer Protocol (HTTP). Several languages may be accustomed to facilitate the applying program that receives and processes user data. the foremost well-liked CGI applications are C, C++, Java, and PERL.
- PHP – Hypertext Preprocessor: where the script is embedded among an online page at the side of its hypertext markup language. Before a page is shipped to a user, the online server calls PHP to interpret and perform any operations involved within the PHP script. Whereas hypertext markup language displays static content, PHP permits the developer to make pages that gift the user with dynamic, custom-made content supported user input. HTML pages that contain PHP scripting square measure typically given a file name with the suffix of “.php”.
- Active Server Pages (ASP): web content that has AN .asp Active server pages (ASP), is a database drive dynamically created a website with a.ASP extension. They utilize ActiveX scripting -- typically VBScript or JScript code. once a browser requests AN ASP, the online server generates a page with hypertext markup language code and like a shot sends it back to the browser – during this means they allow internet users to look at real-time knowledge, however, they're a lot of at risk of security problems.
Common Web Application Problems
Web applications don't essentially have their own special forms of issues however they are doing have a number of their own terms for issues as they seem online.
As Web application testing has an adult, a particular security following has adult too and therewith, a specific classification of Web vulnerabilities.
Common Web application issues square measure classified below according to the OSSTMM Risk Assessment Values
While there square measure several opinions and most of the main points to assembling with security in mind return from the logic of the technologist and their ability with the programing language, these basic guidelines are derived from materials on the market from the OSSTMM (http://www.osstmm.org).
HTML could be a set of directions that explains, however, the info is to be bestowed from an online server (Apache, net info Server) to a browser (Firefox, Opera). it's the guts of the globe Wide Web.
HTML will do rather more than simply show knowledge on an online page. It can even give knowledge entry forms, wherever knowledge may be entered for the process by the next level language (Perl, PHP, etc).
Guidelines for Building Secure Web Applications
While there square measure several opinions and most of the main points to assembling with security in mind return from the logic of the technologist and their ability with the programing language, these basic guidelines are derived from materials on the market from the OSSTMM (http://www.osstmm.org).
- Assure security doesn't need user choices.
- Assure business justifications for all inputs and outputs within the application.
- Quarantine and validate all inputs as well as app content.
- Limit trusts (to systems and users).
- code knowledge.
- Hash the parts.
- Assure all interactions occur on the server facet.
- Layer the safety.
- Invisible is best- show solely the service itself.
- Trigger it to alarm.
- Security awareness is needed for users and helpdesks.
HTML Basics – A Brief Introduction
HTML could be a set of directions that explains, however, the info is to be bestowed from an online server (Apache, net info Server) to a browser (Firefox, Opera). it's the guts of the globe Wide Web.
HTML will do rather more than simply show knowledge on an online page. It can even give knowledge entry forms, wherever knowledge may be entered for the process by the next level language (Perl, PHP, etc).
During a business setting, this is often wherever hypertext markup language is at its most helpful however during a hacker setting, this is where hypertext markup language is at its most vulnerable.
Reading HTML
HTML is communicated with a series of tags or markups. every gap tag,, as an example, must have a closing tag,.
Reading HTML
HTML is communicated with a series of tags or markups. every gap tag,, as an example, must have a closing tag,.
This tells the browser to prevent the markup delineate by the preceding tag. gap and shutting tags square measure a neighborhood of grammatical hypertext markup language.
Take, for instance, the code:
<html>
<head><title>Hello World!</title></head>
<body>
<h>Hello World!</h>
</body>
</html>
We square measure telling the browser this is often AN hypertext markup language document with the tag <html> and that we have a title of 'Hello World' with the <title> tag.
Take, for instance, the code:
<html>
<head><title>Hello World!</title></head>
<body>
<h>Hello World!</h>
</body>
</html>
We square measure telling the browser this is often AN hypertext markup language document with the tag <html> and that we have a title of 'Hello World' with the <title> tag.
The <body> tag tells our browser “here is wherever the information you may be displaying goes.” Finally, the tags tell the browser to show the information in “Heading 1” vogue.
The tags that square measure preceded with a '/' square measure just the closing tag, this tells the browser to prevent displaying the contents delineate by the gap tag.
Viewing HTML at its Source
All fashionable browsers contain the simplest way to look at the underlying hypertext markup language code that generated the web page you're watching. In most cases, this is often the “view source” possibility beneath the “view” menu in your browser.
Links
Links (or hyperlinks) square measure extremely the guts of hypertext markup language page building. the largest strength of hypertext markup language is the ability to link to alternative documents.
Hello World!
Viewing HTML at its Source
All fashionable browsers contain the simplest way to look at the underlying hypertext markup language code that generated the web page you're watching. In most cases, this is often the “view source” possibility beneath the “view” menu in your browser.
Links
Links (or hyperlinks) square measure extremely the guts of hypertext markup language page building. the largest strength of hypertext markup language is the ability to link to alternative documents.
A link, within the context of hypertext markup language, is denoted as www.yahoo.com The link can seem like web.yahoo.com on your web site. this can take guests of your website to Yahoo.
Links may be checked and followed by questionable link checker programs. These programs search hypertext markup language ASCII text files for the tags to produce a file or index of the found links.
Links may be checked and followed by questionable link checker programs. These programs search hypertext markup language ASCII text files for the tags to produce a file or index of the found links.
Spammers can typically use this system to search out email addresses or contact forms they will use to unfold their mass emails. Link checkers can even be accustomed check your website for “broken” links or links that do not go anyplace. this could happen a great deal even in relatively little sites.
Proxy methods for Web Application Manipulation
A protocol proxy server is a middle man between an online server and an online shopper (browser). It intercepts and logs all connections between them and in some cases will manipulate that knowledge request to check however the server can respond.
Proxy methods for Web Application Manipulation
A protocol proxy server is a middle man between an online server and an online shopper (browser). It intercepts and logs all connections between them and in some cases will manipulate that knowledge request to check however the server can respond.
This could be helpful for testing applications for varied cross-site scripting attacks (provide reference link here), SQL Injection attacks, and the other direct request vogue attack.
A proxy testing utility (SpikeProxy, WebProxy, etc), can assist with most of those tests for you. whereas some have AN automation feature, you will quickly learn that it's truly a weak substitute for a true author the wheel of such tools.
Once the proxy server is put in and your browser is pointed at it, surf around the website your testing. Remember, take care to use a web site that you simply have permission to check. Once you have got surfed around, purpose your browser to the proxy's admin page (for SpikeProxy, it http://www.immunitysec.com/resources-freesoftware.shtml) and start testing the location.
From the admin interface, you'll have the tool brute force the site's authentication strategies or test for cross-site scripting. (Actually, we tend to advocate victimization Mozilla or Firefox and http://livehttpheaders.mozdev.org/modify headers and cookies on the fly while not the requirement for a separate proxy port.
A proxy testing utility (SpikeProxy, WebProxy, etc), can assist with most of those tests for you. whereas some have AN automation feature, you will quickly learn that it's truly a weak substitute for a true author the wheel of such tools.
Once the proxy server is put in and your browser is pointed at it, surf around the website your testing. Remember, take care to use a web site that you simply have permission to check. Once you have got surfed around, purpose your browser to the proxy's admin page (for SpikeProxy, it http://www.immunitysec.com/resources-freesoftware.shtml) and start testing the location.
From the admin interface, you'll have the tool brute force the site's authentication strategies or test for cross-site scripting. (Actually, we tend to advocate victimization Mozilla or Firefox and http://livehttpheaders.mozdev.org/modify headers and cookies on the fly while not the requirement for a separate proxy port.
Not only does it extremely alter things, but it is also a rather more powerful toolset as we tend to teach it in ISECOM's OSSTMM skilled Security Tester category (PST).
However, since you may understand setting up proxies for alternative things, like an ad and spam filters, privacy filters, etc. we tend to thought you should truly set one up for real and Spike could be a sensible one to undertake.)
A proxy server may be a strong tool in serving to you identify however solid an online application is. For penetration tests or vulnerability assessments, you need to have an honest proxy tool in your toolbox. Their square measure elaborated tutorials on the market on victimization SpikeProxy at http://www.immunitysec.com/resources-papers.shtml.
Protecting your Server
There square measure many steps that will be taken to protect your server. These embody guaranteeing that your package is usually updated and patched with any security updates that square measure available from the manufacturer.
A proxy server may be a strong tool in serving to you identify however solid an online application is. For penetration tests or vulnerability assessments, you need to have an honest proxy tool in your toolbox. Their square measure elaborated tutorials on the market on victimization SpikeProxy at http://www.immunitysec.com/resources-papers.shtml.
Protecting your Server
There square measure many steps that will be taken to protect your server. These embody guaranteeing that your package is usually updated and patched with any security updates that square measure available from the manufacturer.
This includes guaranteeing that your OS and Web servers square measure updates likewise. additionally, Firewalls and Intrusion detections systems will facilitate defend your server, as mentioned below.
Firewall
Firewalls originally were fireplace roof walls used as barriers to stop the fire from spreading, such as between housing units among a building. an equivalent term is employed for systems (hardware and software) that seeks to stop unauthorized access of AN organization's info.
Firewall
Firewalls originally were fireplace roof walls used as barriers to stop the fire from spreading, such as between housing units among a building. an equivalent term is employed for systems (hardware and software) that seeks to stop unauthorized access of AN organization's info.
Firewalls are like security guards that, supported sure rules, permit or deny access to/from the traffic that enters or leaves a company (home) system. they're necessary systems safeguards that seek to stop AN organization’s system from being attacked by internal or external users. It is the first and most vital security gate between external and internal systems.
Firewalls square measure usually placed between the web ANd an organization’s system. The firewall administrator configures the firewall with rules permitting or denying info packets from getting in or departure the organization.
The rules square measure created employing a combination of net Protocol (IP) address and Ports; such rules are created counting on the organization's desires e.g. during a college, students square measure allowed in based on the card.
The rule to the safety guard during a college would be to permit all persons that carry a legitimate identity card and deny everybody else. but the safety guard would have another rule for exiting from the school; the rule would be to permit everybody exit except babies unless in the midst of adults.
Firewalls square measure usually placed between the web ANd an organization’s system. The firewall administrator configures the firewall with rules permitting or denying info packets from getting in or departure the organization.
The rules square measure created employing a combination of net Protocol (IP) address and Ports; such rules are created counting on the organization's desires e.g. during a college, students square measure allowed in based on the card.
The rule to the safety guard during a college would be to permit all persons that carry a legitimate identity card and deny everybody else. but the safety guard would have another rule for exiting from the school; the rule would be to permit everybody exit except babies unless in the midst of adults.
An analogous system is followed for firewall configuration depending on the character of the organization, the criticality of data quality, cost of security, security policy, and risk assessment.
The firewall similar to a guard cannot decide the contents of the data packet; simply like the guard permits all persons with a legitimate card regardless of the nature of the persons, firewall permits entry or exit primarily based principally on scientific discipline address and Port numbers.
The firewall similar to a guard cannot decide the contents of the data packet; simply like the guard permits all persons with a legitimate card regardless of the nature of the persons, firewall permits entry or exit primarily based principally on scientific discipline address and Port numbers.
Therefore AN entry or exit is feasible by masking scientific discipline address or Port. To mitigate this risk, organizations use the Intrusion Detection System, which is explained within the next section.
Their square measure varied sorts of firewall counting on the options that it's viz. packet filter (operates on scientific discipline packets), stateful firewall (operates primarily based affiliation state), or application firewall (using a proxy).
An example of a firewall rule may be: Block arriving protocol address two hundred.224.54.253 from port one hundred thirty-five.
Their square measure varied sorts of firewall counting on the options that it's viz. packet filter (operates on scientific discipline packets), stateful firewall (operates primarily based affiliation state), or application firewall (using a proxy).
An example of a firewall rule may be: Block arriving protocol address two hundred.224.54.253 from port one hundred thirty-five.
(An notional example); such rule would tell a laptop connected to the net to dam any traffic originating from the pc with AN scientific discipline address two hundred.224.54.253 victimization Port one hundred thirty-five.
Important activities regarding firewalls square measure initial configuration (creating initial rules), system maintenance (additions or amendment in the environment), review of audit logs, performing on alarms, and configuration testing.
Intrusion Detection System (IDS)
Imagine during a college that has correct security guards; however, can the authorities sight entry of unauthorized persons? The authorities would install a stealer alarm that may ring on the entry of unauthorized persons. this is often precisely the operation of the intrusion detection system in laptop parlance.
Intrusion Detection System (IDS)
Imagine during a college that has correct security guards; however, can the authorities sight entry of unauthorized persons? The authorities would install a stealer alarm that may ring on the entry of unauthorized persons. this is often precisely the operation of the intrusion detection system in laptop parlance.
Firewall (security guard or fence) and IDS (burglar alarm or patrolling guard) work
together; whereas firewall regulates entry and exits, IDS alerts/denies unauthorized access.
So however will IDS help? similar to stealer alarms, IDS alerts the licensed person (alarm rings) that a certified packet has entered or left. Further, IDS can even instantly stop such access or user from coming into or exiting the system by disabling user or access.
together; whereas firewall regulates entry and exits, IDS alerts/denies unauthorized access.
So however will IDS help? similar to stealer alarms, IDS alerts the licensed person (alarm rings) that a certified packet has entered or left. Further, IDS can even instantly stop such access or user from coming into or exiting the system by disabling user or access.
It can even activate some other script; IDS will, for instance, forestall or cut back the impact of denial of service by blocking all access from a laptop or teams of laptop.
IDS may be host {based|based mostly|primarily based} or network-based; host-based IDS square measure used on individual computers while network IDS square measure used between computers.
IDS may be host {based|based mostly|primarily based} or network-based; host-based IDS square measure used on individual computers while network IDS square measure used between computers.
Host primarily based IDS may be accustomed sight, alert or regulate abnormal activity on vital computers; network IDS is equally employed in respect of traffic between computers. IDS so can even be accustomed to sight abnormal activity.
IDS like a patrolling guard frequently monitors network traffic to sight any abnormality e.g. high traffic from some computers or uncommon activity on a server, e.g. user logged onto the application and concerned in malicious activity.
IDS like a patrolling guard frequently monitors network traffic to sight any abnormality e.g. high traffic from some computers or uncommon activity on a server, e.g. user logged onto the application and concerned in malicious activity.
IDS compares any event with historical knowledge to sight any deviation. On detection of deviation, IDS acts counting on the rule created by IDS administrator like alerting, storing such intrusion in audit logs, stopping the user from doing any activity, or generating a script for beginning a string of activities.
IDS can even sight deviation based on its information of signatures – any deviation to signature is detected and acted upon this action is comparable to an anti-virus package. IDS is additionally used for the detection of any activity on critical resources or for rhetorical by quiet observation of the suspect.
Secure Communications
Generally, the idea related to secure communications square measure the processes of computer systems that make confidence and reduces risks. For electronic communications, three necessities square measure necessary to make sure security. A) credibleness b) Integrity c) Nonrepudiation.
For example, if an online website grants a prize to ME, and that I will prove it - that's to mention if an online website sends a reduction coupon, and that I verify that the online website is authentic, which no one manipulated the data within the means, the location cannot deny that the coupon was sent.
The form accustomed assure these conditions from an online website is named AN electronic certificate. Maintaining the conditions of security offers North American nation tranquillity in our electronic communications, and permits to assure the principle the privacy within the Web.
Privacy and Confidentiality
Most Web sites receive some info from people who browse them - either by express means like forms, or a lot of covert strategies like cookies or perhaps navigation registries.
Secure Communications
Generally, the idea related to secure communications square measure the processes of computer systems that make confidence and reduces risks. For electronic communications, three necessities square measure necessary to make sure security. A) credibleness b) Integrity c) Nonrepudiation.
- Authenticity: it claims to be. it's not tough to falsify electronic message or to slightly vary the name of an online page, and so airt users, for instance, http://www.diisney.com seems to be the filmmaker web page, however, it's a pair of letters "i" and may be confusing. during this case, you're truly transferred to a gambling website and also the communications don't seem to be safe.
- Integrity:arrives, and has not undergone alterations (voluntary or involuntary) within the passage.
- Non-Repudiation: means that the electrode cannot deny the causation of the transmission.
For example, if an online website grants a prize to ME, and that I will prove it - that's to mention if an online website sends a reduction coupon, and that I verify that the online website is authentic, which no one manipulated the data within the means, the location cannot deny that the coupon was sent.
The form accustomed assure these conditions from an online website is named AN electronic certificate. Maintaining the conditions of security offers North American nation tranquillity in our electronic communications, and permits to assure the principle the privacy within the Web.
Privacy and Confidentiality
Most Web sites receive some info from people who browse them - either by express means like forms, or a lot of covert strategies like cookies or perhaps navigation registries.
This information may be useful and cheap – like memory, your book preferences on Amazon.com, and, therefore, in order to make sure security to the one that browses, many sites have established declarations of Privacy and Confidentiality.
Privacy refers to keeping your info as yours – or limiting it to shut family or your friends, or your contacts, however at the foremost, people who you have got united to share the data. No one wants their info shared everyplace while not management, for that reason, there square measure subjects declared as personal, that's to mention, that of restricted distribution.
On the opposite hand, the confidentiality talks that a subject's info can keep secret, but this point from the angle of the person receiving that info.
For example, if you need a prize, however, you are doing not wish your info distributed, you declare that this info is personal, authorize the data to a couple of individuals, and they maintain confidentiality.
Privacy refers to keeping your info as yours – or limiting it to shut family or your friends, or your contacts, however at the foremost, people who you have got united to share the data. No one wants their info shared everyplace while not management, for that reason, there square measure subjects declared as personal, that's to mention, that of restricted distribution.
On the opposite hand, the confidentiality talks that a subject's info can keep secret, but this point from the angle of the person receiving that info.
For example, if you need a prize, however, you are doing not wish your info distributed, you declare that this info is personal, authorize the data to a couple of individuals, and they maintain confidentiality.
If for a few reasons, in some survey, they raise to you specifically for that the prize, and you respond that if you have got it, you'd hope that that info stays confidential, that's to mention, WHO receive the data keep it in reserve.
We may generalize the definition of confidentiality like "that the data received beneath condition of privacy, I'll maintain as if it absolutely was my very own personal information". it's necessary to declare the conditions of the privacy of data handling, to provide basic assurances of security.
Also, it's suggested that you simply browse the conditions established by the online website you visit in their privacy policy.
Knowing if you are communicating securely
Even with conditions of Privacy and Confidentiality, someone will still intercept the communications.
so as to provide conditions mentioned at the start of this section, a layer of security has been antecedently mentioned referred to as SSL, that uses digital certificates to ascertain a safe affiliation (is to mention that it fulfills the credibleness, integrity, and nonrepudiation) and provides
A level with coding in communications (this is to cover info in order that if somebody takes a part of the data, they can not access it, as a result of the message is encrypted in order that solely the sender that sends it and also the receiver, with an accurate certificate, is able to perceive it).
This layer is named Security Socket Layer, SSL, and is visible through 2 elements among the online browser.
The communications are taken into account to be safe once the online address uniform resource locator changes from protocol to https, this variation even modifies the port of the communication, from eighty to 443.
The communications are taken into account to be safe once the online address uniform resource locator changes from protocol to https, this variation even modifies the port of the communication, from eighty to 443.
Also, in the lower bar of the navigator, a closed padlock seems, that indicates conditions of security in the communications.
If you place the mouse on this padlock, a message can appear particularization the number of bits that square measure used to give the communications (the coding level), that as of these days, 128 bits is that the recommended coding level. this suggests that variety is employed which will be depicted in 128 bits to base the communications.
A type of referred to as trick phishing exists (http://www.antiphishing.org/) during which an online mimics the page to create appear from a bank (they copy the graphics, in order that the shoppers enter their knowledge, trusting that it's the bank, though it's not it).
If you place the mouse on this padlock, a message can appear particularization the number of bits that square measure used to give the communications (the coding level), that as of these days, 128 bits is that the recommended coding level. this suggests that variety is employed which will be depicted in 128 bits to base the communications.
A type of referred to as trick phishing exists (http://www.antiphishing.org/) during which an online mimics the page to create appear from a bank (they copy the graphics, in order that the shoppers enter their knowledge, trusting that it's the bank, though it's not it).
So as to avoid these things, the authenticity of the location ought to be verified, and checked that the communications square measure safe (https and also the closed padlock), and to the most effective of your information, it verifies the certificate.
Strategies of Verification
At now, you have got had a chance to grasp the foundations the safety within the Web, the main aspects associated with a number of the vulnerabilities found normally within the Web servers used
to lodge the various sites with that we tend to habitually act once browsing in net, and the form during which totally different defects within the development of Web applications, have an effect on the safety and/or the privacy of the users normally.
On the opposite hand, you have got learned a number of the technologies on that we tend to trust to guard our servers and conjointly our privacy.
Strategies of Verification
At now, you have got had a chance to grasp the foundations the safety within the Web, the main aspects associated with a number of the vulnerabilities found normally within the Web servers used
to lodge the various sites with that we tend to habitually act once browsing in net, and the form during which totally different defects within the development of Web applications, have an effect on the safety and/or the privacy of the users normally.
On the opposite hand, you have got learned a number of the technologies on that we tend to trust to guard our servers and conjointly our privacy.
However, in all probability at this moment, you're realizing questions such as I'm safe, currently that I even have taken the corresponding actions? Is my system safe?
The developers that have programmed a number of the functionalities that I even have employed in my computing machine, have they taken care of guaranteeing aspects to the security? however, I will verify these aspects?
As in all probability, you have got thought, it's not enough to use manufacturer updates or trust the good intentions of the developer, once your security or privacy worries.
As in all probability, you have got thought, it's not enough to use manufacturer updates or trust the good intentions of the developer, once your security or privacy worries.
Within the past, there are many cases during which manufacturer's patches corrected one vulnerability, but inflicting another downside within the system, or once patched discovered a replacement vulnerability.
Due to this and alternative reasons, you may need to take into account, that's completely necessary to verify frequently the enforced systems, so as to the system "remains" safe.
Luckily, many folks have developed in their own time, some "Methods of Verification", most of that square measure on the market free, in order that we tend to all could cash in of the advantages of its use.
Luckily, many folks have developed in their own time, some "Methods of Verification", most of that square measure on the market free, in order that we tend to all could cash in of the advantages of its use.
Such they have supported the expertise of many professionals, and embody varied "good practices" concerning implementing technology in safe kind. Therefore, it's suggested, that you adopt these methodologies at the time of creating your tasks of verification.
An example of those, the OSSTMM is mentioned concisely below.
OSSTMM
The OSSTMM, that is AN abbreviation for "Open supply Security Testing Manual Methodology" is one in all the methodologies of testing security that's widely used. As delineate in its introduction, though sure individual tests square measure mentioned, these don't seem to be notably revolutionary, the methodology altogether represents a customary of essential reference, for anyone eager to do a check of security in AN ordered format and with skilled quality.
OSSTMM
The OSSTMM, that is AN abbreviation for "Open supply Security Testing Manual Methodology" is one in all the methodologies of testing security that's widely used. As delineate in its introduction, though sure individual tests square measure mentioned, these don't seem to be notably revolutionary, the methodology altogether represents a customary of essential reference, for anyone eager to do a check of security in AN ordered format and with skilled quality.
The OSSTMM is split into many sections. within the same means, it's doable to spot within it, a series of specific testing modules, through that every dimension of security is tested and integrated with the tasks required to make sure security.
These sections include Personnel Security, knowledge Network Security, Telecommunications Security, Wireless Communications Security, and Physical Security, and also the sections of this system detail security from the purpose of reading of that check to try to, WHY to try to to it and once to try to it.
The OSSTMM by itself details the technical scopes and ancient operation of security, but, and this is often maybe one in all the important aspects, not the precise tests, rather it presents, what ought to be tested, the shape during which the check results should be presented/displayed, the rules for testers to follow to assure best results, and also, incorporates the idea of security metrics with RAVs (Risk Assessment Values) to place a factual variety on what proportion security you have.
These sections include Personnel Security, knowledge Network Security, Telecommunications Security, Wireless Communications Security, and Physical Security, and also the sections of this system detail security from the purpose of reading of that check to try to, WHY to try to to it and once to try to it.
The OSSTMM by itself details the technical scopes and ancient operation of security, but, and this is often maybe one in all the important aspects, not the precise tests, rather it presents, what ought to be tested, the shape during which the check results should be presented/displayed, the rules for testers to follow to assure best results, and also, incorporates the idea of security metrics with RAVs (Risk Assessment Values) to place a factual variety on what proportion security you have.
The OSSTMM could be a document for professionals however it's ne'er too early to undertake to understand it and find out how it works. The ideas square measure terribly thorough ANd it's written in an easy-to-comprehend vogue.
Related:
Related:
- Ethical Hacking Tutorials - What is Malware?
- Ethical Hacking Tutorials - What is Wireless Hacking?
- Ethical Hacking Tutorials - What is Buffer Overflow Attack?
- Hacking with Android - Become a True Android Hacker


.png)
















No comments:
Post a Comment