Monday, 12 April 2021
Labels:
Kali Linux Tutorials
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Wednesday, 16 December 2020
Labels:
Kali Linux Tutorials
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Tuesday, 8 December 2020
Labels:
Kali Linux Tutorials
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Tuesday, 21 July 2020
Labels:
Hacking,
Kali Linux,
Penetration Testing
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Thursday, 15 August 2019
Labels:
Hacking
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Labels:
Hacking
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Wednesday, 14 August 2019
Labels:
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Tuesday, 6 August 2019
Labels:
Hacking
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Saturday, 3 August 2019
Labels:
Cryptocurrency
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Thursday, 13 June 2019
Labels:
Penetration Testing
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Sunday, 9 June 2019
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Saturday, 8 June 2019
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Friday, 7 June 2019
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Thursday, 6 June 2019
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Wednesday, 5 June 2019
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Tuesday, 4 June 2019
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Friday, 31 May 2019
OWASP Tutorials - The OWASP Testing Framework
This section describes a specific
It can be seen as a reference framework, which includes techniques and functions that are suitable at various stages of the software development life cycle (SDLC).
Companies and project teams can use this model to develop their own testing framework and to scope for testing services from vendors.
This structure should not be seen as a precipitative but can be seen as a flexible approach that can be enhanced and molded to fit an organization's Development process and culture.
The purpose of this section is to help organizations to make a full strategic The testing process, and which is not intended for consultants or contractors The trial is engaged in more strategic, specific areas.
It is important to understand why an end-to-end test is made
The framework is important for assessing and improving software security.
In writing secure code, Howard and LeBlanc said that in releasing a security bulletin, Microsoft costs at least $ 100,000, and this is their cost. Clients are more than complying to collective security
Patches
He also said that the U.S. government's cybercrime web
Site (
Damage to criminal cases and organizations. Specific losses are more than $ 100,000 so far.
With such economics, it is little wonder why the software vendor
Completely display black box safety test, which can
Only to be performed on applications that have already been developed, to focus on testing in the initial chapters of the application Development, such as definition, design, and development.
Many safety practitioners still see safety testing in the radius
penetration Testing.
As discussed earlier, while the entrance test is played, it is usually unable to find the bug and depends heavily on the tester's skill.
It should be considered only as an implementation technique, or to raise awareness of production issues. To improve the security of applications, the security quality of the software should be improved.
This means testing the security in definition, design, development, deployment, and maintenance stages, and do not rely on the expensive strategy of waiting until the code is fully formed.
As discussed at the beginning of this document, there are many
Methods of development, such as the rational integrated process,
eXtreme and agile development, and traditional waterfall system.
The objective of this guide is neither to suggest any particular development method nor provide specific guidance to follow a particular method.
Instead, we are presenting a generic The development model and the reader must follow it according to their company's process.
There are the following activities in this test structure.
Should take place:
- Before development begins
- During definition and design
- During development
- During the deployment
- Maintenance and operation
Step 1: Before Development Begins
Define an SDLC
There should be an adequate SDLC before application development begins It has been defined that where protection lies in each stage.
Review policies and standards
Ensure that there are appropriate policies, standards, and documentation.
Documentation is very important because it gives guidelines and policies to development teams they can follow.
People can do the right thing only if they know what is the right thing.
If the application is to be developed in Java, then it is necessary that there There is a Java Secure coding standard.
If the application needs to use cryptography, then it is important that cryptography is standard.
No policy or standard can cover every stage of development The team will face.
By documenting general and predictable issues, There will be fewer decisions that need to be made during the development process.
Develop the Measurement and Metrics Criteria and Sure Detection ability
Before development begins, plan a measurement program. by
Requirements need to be defined, it provides visibility
Fault in both process and product
It is necessary to define Before the development begins, the metrics may need to be done in the form of Modify the process to capture data.
Step 2: During Definition and Design
Review of Security Requirements
Defines safety requirements, how an application works from a security perspective.
It is necessary that there are safety requirements Tested. The test, in this case, means that testing the assumptions Requirements and testing have been made to see if there are an interval Definitions of requirements
For example, if there is a security requirement that tells users
Before they can access the Whitepaper section of any website, it must be registered, does it mean that the user must be registered with the system or should the user be certified?
Make sure the requirements are as clear as possible.
While looking for the gap requirements, consider looking at security A mechanism such as:
• User Management
• Authentication
• Authorization
• Data privacy
• Integrity
• Accountability
• Session management
• Transportation safety
• Tiered system isolation
• Legislative and standard compliance (including privacy)
Government and industry standards)
Review Design and Architecture
Applications should have a documented design and architecture.
This document may include models, text documents, and
Other similar artifacts.
It is necessary to test these artifacts to ensure that the design and architecture requirements apply to the appropriate level of security defined.
Identifying safety flaws in the design phase is not only one
Most cost-efficient places to identify flaws, but one can be
The most effective place to make changes
For example, if it is recognized that the design asks for authorization decisions in many places, it may be appropriate to consider the central authority component.
If the app is verifying data at multiple locations, it may be appropriate to develop the central verification framework (eg, fixing the input validation in one place, but at hundreds of places, is very cheap).
If the vulnerabilities are discovered, then the system must be given to the architect for an alternative approach.
Create a UML Model and Review
Once the design and architecture is complete, create Unified
Modeling Language (UML) models that describe how the application works. In some cases, these may already be available.
Use these models to conform with system designers
Understanding how the application works.
If vulnerabilities are discovered, they should be given to the system architect for an alternative approach.
Build and Review Danger Models
Armed with Design and Architectural Review and UML Model
Actually stating how the system works, a threat modeling exercise. Develop realistic danger scenarios.
Analyze the design and architecture to ensure that these hazards have been reduced, have been accepted by the business, or have been assigned to third parties such as an insurance company.
When there is no strategy of mitigation in identified threats, then revise the design and architecture with the system architect to modify the design.
Step 3: During Development
Theoretically, development is the implementation of a design.
However, in the real world, many design decisions are made during code development.
These are often small decisions that were either elaborate to be described in the design or such issues where no policy or standard guidance was given.
If the design and architecture were not enough, the developer would have to face many decisions.
If there were insufficient policies and standards then the developer would have to face even more decisions.
Walk Through Code
The security team should walk a code Developers, and in some cases, system architects.
A code is a high-level walkthrough of the Walkthrough code, where developers can interpret the logic and flow of the implemented code.
This code allows the review team to get a general understanding of the code and allows the developers to explain how some things were developed.
The purpose is not to review code but to understand the High-level flow, layout, and structure of the code Application.
Code Review
With a good understanding of how the code is structured And why some things were way to code, testers Now can check the actual code for security flaws.
Static code reviews validate the code against a set of the checklist,
Including:
- Business Requirements for availability, privacy, and Integrity
- Top 10 checklist for OWASP guide or technical performance (Depends on the depth of the review).
- Specific issues related to language or usage, such as As Scarlet Paper for PHP or Microsoft Secure Coding Checklist For ASP.NET
- Any industry-specific requirements, such as the Sarbanes-Oxley 404, COPPA, ISO / IEC 27002, APRA, HIPAA, Visa Trader Guidelines, Or other regulatory rules
In terms of returns on invested resources (most of the time), static codes Reviews produce higher quality returns than any other security Trust the review method and critics at least
However, they are not a silver bullet and need to carefully consider within the full spectrum testing regime.
For more information on OWASP checklist, please see the OWASP guide For the latest version of Secure Web App or OWASP Top 10
Step 4: During Deployment
Application Access Test
After testing the requirements, analyzing the design, and reviewing code, it can be assumed that all the issues have happened caught up.
Hopefully, this is the case, but after registering the application, the penetration testing provides a final check to make sure
That nothing has been missed.
Configuration Management Test
How to apply in the entrance test application should include
The infrastructure was deployed and secured.
Although the application may be safe, a small aspect of the configuration can still be on a default install stage and may be vulnerable to exploitation.
Step 5: Maintenance and Operation
Operations Management Reviews
There is a need to have a process that explains how to manage the operational aspects of both the application and the infrastructure.
Conducting health check-ups from time to time
Monthly or quarterly health check should be done on both
Application and infrastructure to ensure a new security risk
Has been introduced and the safety level is still intact.
Ensure Change Verification
Every change in the QA environment has been approved and after the test has been deployed in the production environment, it is important Changes are checked to ensure that the security level is
Not affected by the change
It should be integrated into the change management process.
A Typical SDLC Testing Workflow
The following figure shows a specific SDLC test workflow.
Labels:
OWASP Tutorials.
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Labels:
OWASP Tutorials.
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Thursday, 30 May 2019
Labels:
OWASP Tutorials.
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Wednesday, 29 May 2019
OWASP Tutorials - Deriving Security Test Requirements
These purposes are specified by security requirements.
This section discusses in detail how to obtain requirements from the applicable standards and how to document requirements for Security
And from rules and positive and negative application requirements. It also discusses how security requirements work effectively
How can security tests and security test data be done during SDLC
Software security is used to manage risks effectively.
OWASP Testing Objectives
One objective of a security test is to validate that security
Control works as expected. It has been documented through security requirements that describe the functionality of security control.
At A Higher level, this means proving confidentiality, integrity, and availability Service with data only Another objective is to validate
Security controls are implemented with some vulnerabilities.
These are common weaknesses, such as
During the SDLC, the previously identified vulnerabilities with security assessment, such as threat modeling, sources
Code analysis, and entrance exam.
Security Requirements Documentation
The first step in the documentation of security requirements is
Understand business needs. A business requirement
The document can provide initial high-level information on the expected Application Functionality,
For example, one of the main objectives The application may be to allow customers to provide financial services or to purchase goods from the online catalog.
A security section The need to protect business needs should be highlighted Following customer data as well as the applicable security documentation such as rules, standards, and policies.
A general checklist of applicable rules, standards, and policies is a good initial security compliance analysis for web applications. For example, compliance rules can be identified To check information about the business sector and country or state where the application will operate.
Some of these compliance Guidelines and rules can be transformed into specific technical requirements for security control. For example, in the case of financial For compliance with FFIEC guidelines for applications, certification, financial institutions will have to apply those applications which Reduce vulnerable authentication risks with multi-layered security controls and multi-factor authentication.
Industry standards applied for protection needs should also be captured General Security Requirements Checklist For example, in case Compliance with applications that handle customer credit card data PCI denies the storage of PINs and CVV2 with DSS standard
Data and necessity keep the Merchant Magnetic Strip data safe
Performance by storage and broadcasting and masking with encryption. Such PCI DSS security requirements can be validated through the source code analysis
To comply with the information security of the organization, another section of the checklist is required to implement general requirements Standards and policies.
From the perspective of functional requirements, the requirements for security control need to go on a specific map Section of Information Security Standards An example of such a requirement can be:
"A password complexity of six alphanumeric characters must be implemented by the authentication control application. "
Map to comply with safety requirements rules Security testing can validate the risk of compliance risks. If there is a violation With information security standards and policies, they will meet
As a result of a risk that can be documented and business needs to be done Take it.
Since these safety compliance requirements are enforceable, they should be well documented and valid with safety testing.
To be a successful test program, one should know what the purpose of the testis. These purposes are specified by security requirements.
This section discusses how to get the requirements from applicable standards and how to document requirements for security testing.
And from rules and positive and negative application requirements.
It also discusses how security requirements work effectively
How to make a security test and security test data during SDLC
Software security is used to manage risks effectively.
One objective of a security test is to validate that security
Control works as expected. It has been documented through security requirements that describe the functionality of security control.
At A Higher level, this means proving confidentiality, integrity, and availability Service with data is valid only for one more purpose Security controls are implemented with some vulnerabilities.
These are common weaknesses, such as OWASP Top Ten, such as During SDLC, the previously identified vulnerabilities with security assessment, such as threat modeling, sources Code analysis, and entrance exam.
Security Requirements Document
The first step in the documentation of security requirements is
Understand business needs.
A business requirement
The document can provide initial high-level information on expected Application functionality, for example, one of the main objectives The application may be to allow customers to provide financial services or to purchase goods from the online catalog.
A security section The need to protect business needs should be highlighted Client data as well as application security documentation such as rules, standards, and policies.
A general checklist of applicable rules, standards, and policies is a good initial security compliance analysis for web applications.
For example, compliance rules can be identified To check information about the business area and country or state where the application will operate.
Some of these compliance Guidelines and rules for security control can be changed in specific technical requirements.
For example, in the case of financial For applications, authentication, financial institutions, the FFIEC guidelines have to be implemented to comply with those applications Reduce vulnerable authentication risks with multi-layered security controls and multi-factor authentication.
Industry standards applicable to protection requirements should also be caught Common Security Requirements Checklist For example, in case Compliance with applications that handle customer credit card data PCI denies the storage of PIN and CVV2 with DSS standard Data and requirement merchants reserve magnetic stripe data
Performance by masking with storage and transmission and encryption. Such PCI DSS security requirements can be validated through the source code analysis
To comply with the information security of the organization, another section of the checklist is necessary to implement general requirements Standards and Policies From the point of view of the functional requirements, the safety control requirements need to go on a specific map Section of Information Security Standards may be an example of such a requirement:
"A password complexity of six alphanumeric characters must be implemented by authentication application. "Maps to follow the safety requirements rules Safety tests can validate the risk of compliance risks.
If there is a violation With information security standards and policies, they will meet As a result of a risk that can be documented and business needs to be done Take.
Since these safety compliance requirements are enforceable, they should be well documented and valid with safety
Test
Security Testing and Risk Analysis
Security requirements need to be kept in mind Vulnerabilities to support risk mitigation strategy.
Assuming The organization keeps the reserves of weaknesses found In applications (i.e., the basis of a vulnerability knowledge), security Issues can be reported by type, problem, quenching, root cause, and they are mapped to applications where they are found.
Such a vulnerability knowledgebase can be used to establish a metric to analyze the effectiveness of security tests in SDLC.
For example, consider an input validation problem, such as SQL injection, which was identified through source code analysis, and a coding error was reported with the original reason and the input validation vulnerability its types.
The risk of such vulnerability can be assessed through one By checking the input fields with penetration testing, multiple SQL injections Attack on vectors This test can validate that there are special characters Filtered before hitting the database and reducing vulnerability.
By combining source code analysis and results of penetration
Testing is possible and it is possible to determine the risk
Calculation of risk rating of vulnerability and vulnerability By reporting the vulnerability risk rating in the findings (e.g., the test report)
It is possible to decide on a mitigation strategy. For example, high and Prioritization can be given to overcome the vulnerabilities of moderate risk, while Less risk can be fixed in further releases.
By considering the risks of harassment of common weaknesses, it is possible to identify potential risks that apply Security testing requires security testing.
For example, OWASP Phishing, privacy violation, identity theft, system agreement, Data changes or data loss, financial loss, and reputation loss.
Such issues should be documented as part of the danger Scenarios. Thinking about the dangers and weaknesses, It is possible to prepare a battery of trials that mimic such attacks Scenarios.
Ideally, organization vulnerability is the basis of knowledge
Verification can be used to obtain security risk-driven test cases
The most probable attack scenario
For example, if identity theft is High risk is considered, negative test scenarios should be validated Mitigation of the effects of the exploitation of vulnerabilities In authentication, cryptographic controls, input validation, and authorization control.
Derivative Functional and Non Functional Test Requirements
Functional Security Requirements
From the point of view of functional safety requirements, both applicable standards, policies, and regulations are required.
One type of security control as well as control functionality. In
Needs are also known as "positive requirements" because
They tell the expected functionality that can be validated through
Safety test Examples of positive requirements are:
"Applications will lock out the user after six failed logs on attempts" or "The password must be at least six alphanumeric characters".
Recognition of positive requirements include Expected functionality and testing can be tested by rebuilding Conducting tests according to the conditions and predetermined inputs.
The results are then shown as failed or nearby status.
To validate safety requirements with safety tests, security requirements are required to operate and they need to be done.
Light up the required functionality (what) and briefly tell
Implementation (how).
Examples of high-level security design Requirements for authentication can be:
- Protect user credentials and shared secrets in transit and storage
- Mask any confidential data in the display (e.g., password, account)
- Lock user account after a certain number of failed logs in attempts
- Do not show user-specific verification errors as a result of failed login
- Only allow passwords that are alphanumeric, special characters and six characters are included in the minimum length, to limit the attack surface
- Allow the functionality of password change for valid users only by past password, new password, and validation The user responds to the question of challenge, to prevent passwords from being password changed.
- The password reset form must be valid before sending the user's username and the user's registered email through a temporary password via email. The temporary password issued should be a one time password. A link to the password reset web page will be sent to the user. The password reset web page should answer the user's temporary password, new password, as well as the question of user challenge.
Risk Driven Security Requirements
Safety tests need to be risk-driven, that is, they have to validate the application for unexpected behavior.
They are also called "Negative Needs" because they specify what the application is Should not do.
Examples of negative requirements are:
- The application should not allow data to be changed or deleted
- The application should not be compromised or misused for unauthorized financial transactions by a malicious user.
Negative requirements are difficult to test because there is
There is no expected behavior to look at.
This may require unexpected input statuses, causes, and a threat analyzer to come along effect.
This is where safety testing is required to operate with risk Analysis and Threat Modeling Danger Document is Circumstances and counter-clockwise function as a factor To reduce danger.
For example, in the case of authentication control, the following
Security requirements can be documented by threats and
Counterparty perspective:
- Encrypt authentication data in storage and transit to minimize risk
- Encrypt passwords using non-reversible encryption such as using Digestion (eg, HASH) and seed to prevent dictionary attacks
- Lock the accounts after reaching the log on the failure limit and Apply password complexity to reduce the risk of brute force password attack
- Display common error messages upon credential verification Reduce the risk of account cutting or condensation
- Authenticate clients and servers to prevent noncompliance And Man in the Middle (MITM) attack
Threatening trees and attack libraries, such as a modeling device may be in danger Useful for getting negative test scenarios.
A danger tree Assume the root attack (i.e., the attacker may be able to read the messages of other users) and identify the different causes of security control (E.g., data validation fails due to SQL injection vulnerability)
And necessary counter notifications (e.g., implementing data validation) And paraphrased questions) that can be valid for being effective In reducing such attacks Getting Safety Testing Requirements through Use and Abuse The case
One condition to describe the application's functionality is to understand what the application has to do and how to do it.
This may happen to be used to describe the use of cases. Use cases, in graphical form As commonly used in software engineering, show interaction Of actors and their relationships.
They help identify the actor's Application, their relationship, the desired sequence of tasks For each scenario, alternative actions, special requirements, preconditions, and post-states.
Similar to using cases, abuse and misuse cases describe the application's unexpected and malicious use scenarios.
These abuse cases provide a way to describe an attacker's scenarios
The application can misuse and misuse.
Going through individual steps in a usage scenario and wondering how this can happen Maliciously exploited, potential flaws or aspects of the application which cannot be well defined? Describe the key All possible or, at least, the most important use and abuse scenario.
Abuse scenarios allow the analysis of applications from the attacker's perspective and contribute to the identification of possible weaknesses and the counter-missions that require enforcement to Reduce the effect caused by the potential risk of such weaknesses.
Given all the usage and abuse cases, it is important to analyze them to determine which of them are most important And security requirements need to be documented.
The identities of the most important abuse and misuse cases inspire the safety requirements and documentation of the necessary controls. Where safety risks should be reduced.
It is a matter of obtaining security requirements and misuse of it
Functional scenarios and negative scenarios are important for defining and they are kept in graphical form.
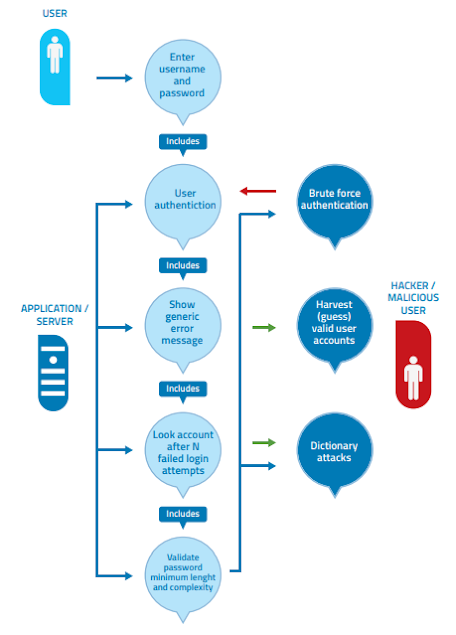
In the case of the derivation of security requirements for authentication, for example, the following step-by-step method can be followed.
Step 1:
Supply of username and password. Application uses grant
Depending on the authentication of user credentials by the app, and users with authentication fails, the user provides specific errors.
Step 2:
Verification errors provide specific information to an attacker
It looks like which accounts are actually valid registered accounts (user name).
Then the attacker will try to force the password Such a valid account A brutal force invades four minimum lengths All digits passwords can be successful with a limited number of attempts
(I.e., 10 ^ 4).
Step 3:
Case of abuse:
An illustrative illustration in the picture below is shown Derivation of security requirements through cases of use and misuse Functional scenarios have user actions (intranet user name and password) and application actions (authentication) Provides user an error message if verification fails).
In case of abuse involves aggressive action, i.e. trying to break the authentication to force through a dictionary attack and by password
Estimate valid user name by error messages By graphing.
It is possible to represent the dangers of user actions (abuse)
To achieve counter makers as the application functions to reduce such risks.
Step 4:
Security requirements for authentication are derived:
- Password must be alphanumeric, lower and upper case and a minimum of 7 character length
- Accounts need to be locked after five failed logs in the endeavor
- Requires Log Files to be Generic Generic Requirements
These security requirements need to be documented and tested.
Labels:
OWASP Tutorials.
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Saturday, 25 May 2019
OWASP Tutorials - Testing Techniques Explained
This section presents a high-level overview of various
It does not present specific methods for these Techniques. This section has been included to provide references for the designs presented in the next
- Manual inspection and review
- Threatening Modeling
- Code review
- Penetration Testing
Manual Inspection and Review of OWASP Testing
Manual inspection is a human review which generally tests the safety implications of people, policies, and procedures.
The manual inspection may include inspection of technology decisions such as architectural design.
They are usually conducted by analyzing the documentation or documentation with designers or system owners.
While the concept of manual inspection and human review is simple, they can be among the most powerful and effective techniques available.
When someone asks how something works and why it has been implemented in a specific way, the examiner can quickly determine whether any security concerns are likely to be obvious.
Manual inspection and review software development are one of the few ways to test the life-cycle process and to ensure that adequate policy or skill has been set in place.
While doing manual inspection and review with many things in life, it is recommended that a trust-but-verified model be adopted. It is not everything that has been shown or told to the tester, it will be accurate.
Manual review is particularly good for testing whether people understand safety procedures, have been made aware of the policy, and have the appropriate skills to design or implement a secure application.
Manually review the documentation, secure coding policies, safety requirements, and other activities, including architectural design, should be completed using manual inspections.
Advantages:
- Need some supportive technology
- Can be implemented for different types
- Flexible
- Promotes teamwork
- Early in SDLC
Disadvantages:
- It may take time
- Supporting material is not always available
- Important human ideas and skills are needed to be effective
Threat Modeling
Threat modeling has become a popular technique, which will help system designers to think about security threats that can withstand their systems and applications.
Therefore, modeling can be seen as a risk assessment for applications.
In fact, it enables the designer to develop mitigation strategies for potential vulnerabilities and helps them focus on their essentially limited resources and those parts of the system which are most needed.
It is recommended that a hazard model is developed and documented in all applications.
The SDLC should be prepared as soon as possible threat model, and the application should be revived as the development progress and progress.
To develop the hazard model, we recommend taking a simple approach that follows the NIST 800-30 standard for risk assessment. This approach includes:
- Deletion of application - Use a process of manual inspection to understand how the application works, its assets, functionality, and connectivity.
- Defining and classifying assets - classify assets into tangible and intangible assets and rank them according to business importance.
- Discover potential vulnerabilities - whether technical, operational or management
- Exploring potential threats - Developing an actual outlook of potential attacker vectors from an attacker's point of view, using threat scenarios or attacking trees.
- Creating mitigation strategies - Develop mitigation controls for each hazard identified as realistic.
The Output can vary from a hazardous model, but there is usually a collection of lists and diagrams.
The OWASP Code Review Guide outlines an application throat modeling methodology that can be used as a reference for testing tests of potential security flaws in the design of the application.
There is no right or wrong way to develop risk models and assess risks on applications.
Advantages:
- Practical attacker's approach to the system
- Flexible
- Early in SDLC
Disadvantages:
- Relatively new technology
- Good threat model does not mean good software
Source Code Review
The review of the source code is the process of manually checking the source code of the web application for security problems.
Many serious security vulnerabilities cannot be diagnosed with analysis or any other form of testing.
As the popular saying is "If you want to know what is really happening, go straight to the source." Almost all security experts agree that there is no alternative to actually viewing the code.
All information is somewhere in the code to identify security problems. Unlike testing, the third party closed
Software such as operating systems, when testing web applications (especially if they have been developed at home), the source code should be made available for testing purposes.
Many unknowingly but important security problems are also extremely difficult to find, with the analysis or other forms of testing, such as penetration testing, source code analysis, making the technique of choice for technical testing.
With the source code, a tester can accurately determine what is happening (or is being considered) and the black box test estimates work out.
Examples of issues specifically found through source code reviews include concurrency problems, inaccurate business logic, access control problems, and cryptographic vulnerabilities, as well as backdoors, trojans, easter eggs, time bombs, logic bombs and other types of malicious code.
These problems often appear as the most harmful vulnerabilities in web sites.
Source code analysis can also be extremely efficient in finding implementation issues, such as at places where input was not verified or unsuccessful open control procedures may exist.
But keep in mind that operational procedures should also be reviewed, as the source code being deployed cannot be the same as it is being analyzed here.
Advantages:
- Completion and Effectiveness
- Accuracy
- Fast (for competent reviewers)
Disadvantages:
- Highly skilled security developers are required
- Recall issues in compiled libraries
- Can not easily detect run-time errors
- The source code actually posted may be different from being analyzed.
For more information on code review, check out the OWASP Code Review Project.
Penetration Testing
Penetrating testing is a common technique used for testing network security for many years. It is also commonly known as black-box testing or ethical hacking.
Penetrating testing is essentially the "art" of the far-running application to detect security vulnerabilities, without knowing the internal functioning of the application.
Typically, the entrance exam team will have access to an app such that they were users.
The tester works like an attacker and attempts to find and exploit weaknesses. In many cases, the tester will be given a valid account on the system.
While penetration testing in network security has proved to be effective, the technique does not translate naturally into applications.
When penetration testing is done on the network and operating system, most of the tasks are involved in detecting and exploiting known weaknesses in specific technologies.
As web applications are almost bespoke exclusively, penetration testing in the web application area is similar to more pure research.
Entrance test tools have been developed which automate the process, but their effectiveness with the nature of web applications is generally poor.
Many people today use the web application login test as their primary security testing technique. Whenever it definitely holds its place in a test program, we do not think it should be considered primary or only testing techniques.
Gary McGrath told the entrance test well when he said, "If you fail in an entrance exam, then you know that you really have a very bad problem.
If you pass an entrance exam, then You do not know that you do not have a very bad problem. "However, concentrated penetration testing (i.e., the test which attempts to take advantage of known weaknesses in previous reviews ) It may be useful to find out if certain vulnerabilities have been fixed in the source code posted on the web site.
Advantages:
- Can be fast (and therefore cheap).
- Comparatively less skill set is needed than reviewing source code
- Examines the code that is actually exposed
Disadvantages:
- SDLC is too late.
- Front effect test only.
The Need for a Balanced Approach
With many techniques and approaches to test the safety of
Web applications can be difficult to understand which technologies are To use and when to use them.
Experience shows that it is not Correct answer or wrong answer to the question of technology The test should be used to build the structure.
In fact, all techniques should be used to test all those areas that need to be tested.
Although it is clear that there is no single technique that can be
Effectively to cover all the security tests and to ensure it was performed All issues have been noticed, many companies adopt only one point of view.
Historically used approaches are approaching Test
Penetration tests, although useful, can not effectively address many problems that need to be checked. It is just "too late" in the Software Development Life Cycle (SDLC).
A right approach is a balanced approach that involves many
From technology, manual reviews to technical tests Balanced
The approach should cover the testing at all stages of SDLC.
This approach takes advantage of the most suitable techniques available on the basis of the current SDLC phase.
Of course, there are times and situations where only one technique is possible.
For example, a test on a web application is already made, but where the trial party does not have access to the source code.
In this case, admission testing is clearly better without any test.
However, challenge parties should be encouraged to challenge theories, such as not accessing the source code, and to explore the possibility of more complete testing.
A balanced approach depends on many factors, such as the testing process and maturity of the corporate culture.
It is recommended that a balanced test framework should look like the representation shown in Figure 3 and Figure 4.
The following figure shows a normal proportional representation Software development has been kept on the life cycle.
Keeping in mind the research and experience, it is essential that companies put more emphasis on the early stages of development.
The following figure shows a specific proportional representation
Overlaid on testing techniques.
The Web Application Scanners
Many organizations have started using automatic web apps
Scanner Although he is undoubtedly a place in a test program,
Some fundamental issues need to be highlighted because it is believed that automating the black box test (or never will) is effective.
However, highlighting these issues should not discourage the use of web app scanners.
Rather, its purpose is to ensure that the boundaries are understood and the test structure should be properly employed.
Important: OWASP is currently working to develop a web application Scanner benchmarking platform. The following examples show why Automatic black box test is not effective.
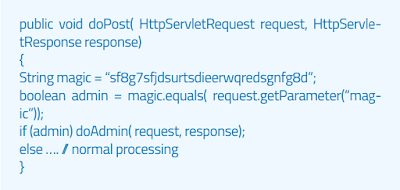
‘Example 1: Magic Parameters’
Imagine a simple web app that accepts a name-value pair
"Magic" and then value. For simplicity, the GET request may be:
To make the case easier, in this case, the value can only be ASCII characters a - z (upper or lower part) and integer 0 - 9.
Designers of this application created an administrative backdoor
During the test, but interrupted it to prevent an accidental supervisor Its exploration By submitting the value sf8g7sfjdsurtsdieerwqredsgnfg8d (30 characters), the user will then be logged in and presented With an administrative screen with total control of the application.
Given that all other parameters were simple-and It is not possible to guess the combination on the three-letter field, about 28 characters. Will be a web app scanner There is a need to put force (or estimates) in the entire primary position of 30 characters.
It is up to 30 ^ 28, or trillions of HTTP requests. That
There is an electron in a digital his toot.
This exemplary magic parameter may look like code for checking
Following:
By looking at the code, vulnerability is practically out of the page
As a potential problem.
Example 2: Bad cryptography
Cryptography is widely used in web applications. Imagine a developer decided to write a simple cryptography algorithm to sign the user Automatically by site A to Site B In her knowledge, the developer Determines if a user is logged into Site A, they will generate A key that uses the MD5 hash function, which includes: hash {username: date }
When a user goes to Site B, they will send the key to the query
String for site b in an HTTP redirect. Site B calculates independently Hash and compares it with a hash passed on request. If they Match, site B signs the user as the user who they claim to be.
As it has been said about this plan, the inadequacies can be worked out. Anyone who detects the plan (or is told how it works or downloads it Information from Bugtraq) can be logged as any user.
Manual inspection, such as a review or code inspection, must have exposed it Security issue quickly There will be no black box web app scanner The vulnerability is highlighted.
It must have seen the 128-bit hash That changed with each user, and the nature of the hash function, done No change in the way of forecast
Static Source Code Review Tools
Many organizations have started using the stable source code scanner.
However, undoubtedly he has got a place in a comprehensive test program, so it is necessary to highlight some basic issues
This approach is not effective when used alone.
Static source code analysis alone cannot identify issues due to flaws in the design It cannot understand the context in which the code has been created.
Source code analysis tools are useful in determining security issues
Due to coding errors, however important manual effort is required
Validate the findings.
Labels:
OWASP Tutorials.
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.