OWASP Tutorials - Deriving Security Test Requirements
These purposes are specified by security requirements.
This section discusses in detail how to obtain requirements from the applicable standards and how to document requirements for Security
And from rules and positive and negative application requirements. It also discusses how security requirements work effectively
How can security tests and security test data be done during SDLC
Software security is used to manage risks effectively.
OWASP Testing Objectives
One objective of a security test is to validate that security
Control works as expected. It has been documented through security requirements that describe the functionality of security control.
At A Higher level, this means proving confidentiality, integrity, and availability Service with data only Another objective is to validate
Security controls are implemented with some vulnerabilities.
These are common weaknesses, such as
During the SDLC, the previously identified vulnerabilities with security assessment, such as threat modeling, sources
Code analysis, and entrance exam.
Security Requirements Documentation
The first step in the documentation of security requirements is
Understand business needs. A business requirement
The document can provide initial high-level information on the expected Application Functionality,
For example, one of the main objectives The application may be to allow customers to provide financial services or to purchase goods from the online catalog.
A security section The need to protect business needs should be highlighted Following customer data as well as the applicable security documentation such as rules, standards, and policies.
A general checklist of applicable rules, standards, and policies is a good initial security compliance analysis for web applications. For example, compliance rules can be identified To check information about the business sector and country or state where the application will operate.
Some of these compliance Guidelines and rules can be transformed into specific technical requirements for security control. For example, in the case of financial For compliance with FFIEC guidelines for applications, certification, financial institutions will have to apply those applications which Reduce vulnerable authentication risks with multi-layered security controls and multi-factor authentication.
Industry standards applied for protection needs should also be captured General Security Requirements Checklist For example, in case Compliance with applications that handle customer credit card data PCI denies the storage of PINs and CVV2 with DSS standard
Data and necessity keep the Merchant Magnetic Strip data safe
Performance by storage and broadcasting and masking with encryption. Such PCI DSS security requirements can be validated through the source code analysis
To comply with the information security of the organization, another section of the checklist is required to implement general requirements Standards and policies.
From the perspective of functional requirements, the requirements for security control need to go on a specific map Section of Information Security Standards An example of such a requirement can be:
"A password complexity of six alphanumeric characters must be implemented by the authentication control application. "
Map to comply with safety requirements rules Security testing can validate the risk of compliance risks. If there is a violation With information security standards and policies, they will meet
As a result of a risk that can be documented and business needs to be done Take it.
Since these safety compliance requirements are enforceable, they should be well documented and valid with safety testing.
To be a successful test program, one should know what the purpose of the testis. These purposes are specified by security requirements.
This section discusses how to get the requirements from applicable standards and how to document requirements for security testing.
And from rules and positive and negative application requirements.
It also discusses how security requirements work effectively
How to make a security test and security test data during SDLC
Software security is used to manage risks effectively.
One objective of a security test is to validate that security
Control works as expected. It has been documented through security requirements that describe the functionality of security control.
At A Higher level, this means proving confidentiality, integrity, and availability Service with data is valid only for one more purpose Security controls are implemented with some vulnerabilities.
These are common weaknesses, such as OWASP Top Ten, such as During SDLC, the previously identified vulnerabilities with security assessment, such as threat modeling, sources Code analysis, and entrance exam.
Security Requirements Document
The first step in the documentation of security requirements is
Understand business needs.
A business requirement
The document can provide initial high-level information on expected Application functionality, for example, one of the main objectives The application may be to allow customers to provide financial services or to purchase goods from the online catalog.
A security section The need to protect business needs should be highlighted Client data as well as application security documentation such as rules, standards, and policies.
A general checklist of applicable rules, standards, and policies is a good initial security compliance analysis for web applications.
For example, compliance rules can be identified To check information about the business area and country or state where the application will operate.
Some of these compliance Guidelines and rules for security control can be changed in specific technical requirements.
For example, in the case of financial For applications, authentication, financial institutions, the FFIEC guidelines have to be implemented to comply with those applications Reduce vulnerable authentication risks with multi-layered security controls and multi-factor authentication.
Industry standards applicable to protection requirements should also be caught Common Security Requirements Checklist For example, in case Compliance with applications that handle customer credit card data PCI denies the storage of PIN and CVV2 with DSS standard Data and requirement merchants reserve magnetic stripe data
Performance by masking with storage and transmission and encryption. Such PCI DSS security requirements can be validated through the source code analysis
To comply with the information security of the organization, another section of the checklist is necessary to implement general requirements Standards and Policies From the point of view of the functional requirements, the safety control requirements need to go on a specific map Section of Information Security Standards may be an example of such a requirement:
"A password complexity of six alphanumeric characters must be implemented by authentication application. "Maps to follow the safety requirements rules Safety tests can validate the risk of compliance risks.
If there is a violation With information security standards and policies, they will meet As a result of a risk that can be documented and business needs to be done Take.
Since these safety compliance requirements are enforceable, they should be well documented and valid with safety
Test
Security Testing and Risk Analysis
Security requirements need to be kept in mind Vulnerabilities to support risk mitigation strategy.
Assuming The organization keeps the reserves of weaknesses found In applications (i.e., the basis of a vulnerability knowledge), security Issues can be reported by type, problem, quenching, root cause, and they are mapped to applications where they are found.
Such a vulnerability knowledgebase can be used to establish a metric to analyze the effectiveness of security tests in SDLC.
For example, consider an input validation problem, such as SQL injection, which was identified through source code analysis, and a coding error was reported with the original reason and the input validation vulnerability its types.
The risk of such vulnerability can be assessed through one By checking the input fields with penetration testing, multiple SQL injections Attack on vectors This test can validate that there are special characters Filtered before hitting the database and reducing vulnerability.
By combining source code analysis and results of penetration
Testing is possible and it is possible to determine the risk
Calculation of risk rating of vulnerability and vulnerability By reporting the vulnerability risk rating in the findings (e.g., the test report)
It is possible to decide on a mitigation strategy. For example, high and Prioritization can be given to overcome the vulnerabilities of moderate risk, while Less risk can be fixed in further releases.
By considering the risks of harassment of common weaknesses, it is possible to identify potential risks that apply Security testing requires security testing.
For example, OWASP Phishing, privacy violation, identity theft, system agreement, Data changes or data loss, financial loss, and reputation loss.
Such issues should be documented as part of the danger Scenarios. Thinking about the dangers and weaknesses, It is possible to prepare a battery of trials that mimic such attacks Scenarios.
Ideally, organization vulnerability is the basis of knowledge
Verification can be used to obtain security risk-driven test cases
The most probable attack scenario
For example, if identity theft is High risk is considered, negative test scenarios should be validated Mitigation of the effects of the exploitation of vulnerabilities In authentication, cryptographic controls, input validation, and authorization control.
Derivative Functional and Non Functional Test Requirements
Functional Security Requirements
From the point of view of functional safety requirements, both applicable standards, policies, and regulations are required.
One type of security control as well as control functionality. In
Needs are also known as "positive requirements" because
They tell the expected functionality that can be validated through
Safety test Examples of positive requirements are:
"Applications will lock out the user after six failed logs on attempts" or "The password must be at least six alphanumeric characters".
Recognition of positive requirements include Expected functionality and testing can be tested by rebuilding Conducting tests according to the conditions and predetermined inputs.
The results are then shown as failed or nearby status.
To validate safety requirements with safety tests, security requirements are required to operate and they need to be done.
Light up the required functionality (what) and briefly tell
Implementation (how).
Examples of high-level security design Requirements for authentication can be:
- Protect user credentials and shared secrets in transit and storage
- Mask any confidential data in the display (e.g., password, account)
- Lock user account after a certain number of failed logs in attempts
- Do not show user-specific verification errors as a result of failed login
- Only allow passwords that are alphanumeric, special characters and six characters are included in the minimum length, to limit the attack surface
- Allow the functionality of password change for valid users only by past password, new password, and validation The user responds to the question of challenge, to prevent passwords from being password changed.
- The password reset form must be valid before sending the user's username and the user's registered email through a temporary password via email. The temporary password issued should be a one time password. A link to the password reset web page will be sent to the user. The password reset web page should answer the user's temporary password, new password, as well as the question of user challenge.
Risk Driven Security Requirements
Safety tests need to be risk-driven, that is, they have to validate the application for unexpected behavior.
They are also called "Negative Needs" because they specify what the application is Should not do.
Examples of negative requirements are:
- The application should not allow data to be changed or deleted
- The application should not be compromised or misused for unauthorized financial transactions by a malicious user.
Negative requirements are difficult to test because there is
There is no expected behavior to look at.
This may require unexpected input statuses, causes, and a threat analyzer to come along effect.
This is where safety testing is required to operate with risk Analysis and Threat Modeling Danger Document is Circumstances and counter-clockwise function as a factor To reduce danger.
For example, in the case of authentication control, the following
Security requirements can be documented by threats and
Counterparty perspective:
- Encrypt authentication data in storage and transit to minimize risk
- Encrypt passwords using non-reversible encryption such as using Digestion (eg, HASH) and seed to prevent dictionary attacks
- Lock the accounts after reaching the log on the failure limit and Apply password complexity to reduce the risk of brute force password attack
- Display common error messages upon credential verification Reduce the risk of account cutting or condensation
- Authenticate clients and servers to prevent noncompliance And Man in the Middle (MITM) attack
Threatening trees and attack libraries, such as a modeling device may be in danger Useful for getting negative test scenarios.
A danger tree Assume the root attack (i.e., the attacker may be able to read the messages of other users) and identify the different causes of security control (E.g., data validation fails due to SQL injection vulnerability)
And necessary counter notifications (e.g., implementing data validation) And paraphrased questions) that can be valid for being effective In reducing such attacks Getting Safety Testing Requirements through Use and Abuse The case
One condition to describe the application's functionality is to understand what the application has to do and how to do it.
This may happen to be used to describe the use of cases. Use cases, in graphical form As commonly used in software engineering, show interaction Of actors and their relationships.
They help identify the actor's Application, their relationship, the desired sequence of tasks For each scenario, alternative actions, special requirements, preconditions, and post-states.
Similar to using cases, abuse and misuse cases describe the application's unexpected and malicious use scenarios.
These abuse cases provide a way to describe an attacker's scenarios
The application can misuse and misuse.
Going through individual steps in a usage scenario and wondering how this can happen Maliciously exploited, potential flaws or aspects of the application which cannot be well defined? Describe the key All possible or, at least, the most important use and abuse scenario.
Abuse scenarios allow the analysis of applications from the attacker's perspective and contribute to the identification of possible weaknesses and the counter-missions that require enforcement to Reduce the effect caused by the potential risk of such weaknesses.
Given all the usage and abuse cases, it is important to analyze them to determine which of them are most important And security requirements need to be documented.
The identities of the most important abuse and misuse cases inspire the safety requirements and documentation of the necessary controls. Where safety risks should be reduced.
It is a matter of obtaining security requirements and misuse of it
Functional scenarios and negative scenarios are important for defining and they are kept in graphical form.
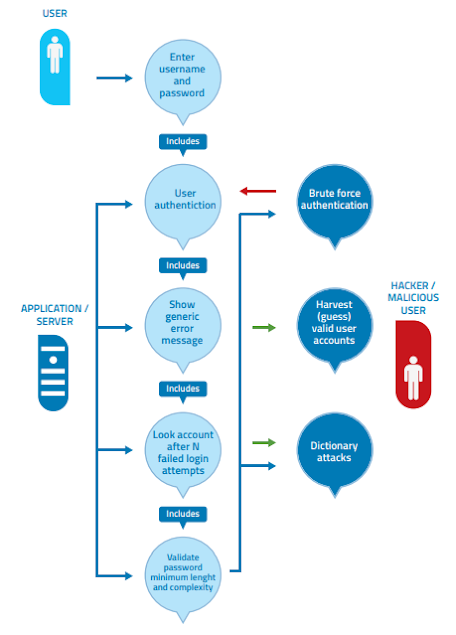
In the case of the derivation of security requirements for authentication, for example, the following step-by-step method can be followed.
Step 1:
Supply of username and password. Application uses grant
Depending on the authentication of user credentials by the app, and users with authentication fails, the user provides specific errors.
Step 2:
Verification errors provide specific information to an attacker
It looks like which accounts are actually valid registered accounts (user name).
Then the attacker will try to force the password Such a valid account A brutal force invades four minimum lengths All digits passwords can be successful with a limited number of attempts
(I.e., 10 ^ 4).
Step 3:
Case of abuse:
An illustrative illustration in the picture below is shown Derivation of security requirements through cases of use and misuse Functional scenarios have user actions (intranet user name and password) and application actions (authentication) Provides user an error message if verification fails).
In case of abuse involves aggressive action, i.e. trying to break the authentication to force through a dictionary attack and by password
Estimate valid user name by error messages By graphing.
It is possible to represent the dangers of user actions (abuse)
To achieve counter makers as the application functions to reduce such risks.
Step 4:
Security requirements for authentication are derived:
- Password must be alphanumeric, lower and upper case and a minimum of 7 character length
- Accounts need to be locked after five failed logs in the endeavor
- Requires Log Files to be Generic Generic Requirements
These security requirements need to be documented and tested.


.png)















No comments:
Post a Comment