How to Bypass Firewall Authentication?
As we all know, the internet has experienced rapid and victorious improvements
In the last decade [Ralf (1997.5)] indicates that more than a million have been Computer network and well over a billion users by the end of the last century. The internet is entering every area all over the world. In the beginning, the Internet Was designed only as research-oriented and its communication protocols were designed Now exists for the more non-lethal environment than now. But when the time passed,
The Internet is constantly rotated from the initial one and its atmosphere is very low Reliable. There are all dangerous and risky situations in it, intent and fatal attacks and Dirty people we can find in real life society as a whole. Today when users Are connected to the Internet, they are able to reach and communicate The world outside through the internet But at the same time, though, the outer world, In the same way, the network of the premises can reach and communicate. therefore it is Very important for users to protect their local system from spicy attacks From outside
Types of Firewall
As stated in [Wikipedia (2006.10)], the firewall technique has emerged for the first time The second half of the 1980s and the first paper of this technique was published in 1988.
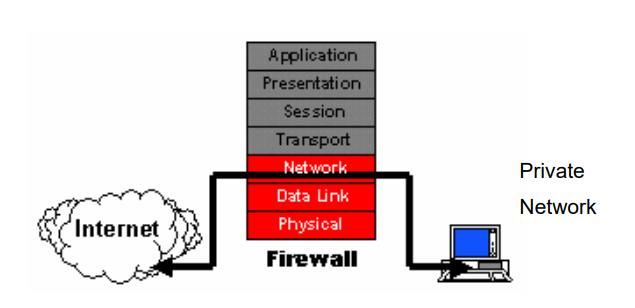
[Tom (2001)] writes that the firewall (as shown in Figure 1) is a kind of gateway It controls the flow of traffic load between borders and networks, usually in the middle An internal ethernet network and the internet.
It is designed to establish a restraint Link and an external security wall Firewall checks all exchanged messages By blocking these packets in or out of the intranet or outside, which do not meet specified Safety criteria and therefore, it should be designed to fulfill the following:
- All traffic, those who try to go to or out of the network, have to go through a firewall.
- Only authorized traffic defined by the local security policy will be allowed to pass the firewall.
- The firewall itself is immune to penetrate, which means that the operating system is safe.
 |
| Figure 1 Firewall Infrastructure |
To create a specific firewall, each user has its own different approach. Firewall Can be implemented in combination with hardware and software, or both. Generally, there are three common types of firewalls:
1. Packet-Filtering Router: Checking this kind of firewall (as shown in Figure 2) Accept all packets to enter or leave the network and reject it on the basis of it User-defined rules Packet filtering router is working on the packet on the TCP / IP network layer. The designing of filtering rules is based on information In the network, the packet contained: source IP address, destination IP address, source and Address of destination transport level, IP protocol area, and interface. Internal The network is directly connected to the external network. The main advantage of packet-filtering routers is its simplicity. It's quite easy, Effective and transparent for users, but it is difficult to configure. In addition to this, This is susceptible to security breaches due to improper configuration like IP Spoofing
 |
| Figure 2 Packing-Filtering Router |
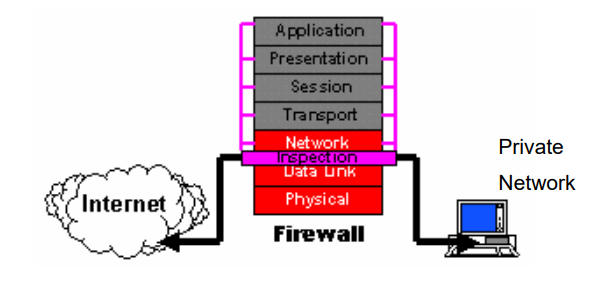
It delivers filtering information on conventional packet-filtering Does not consider individual packets and reference to any high layer. Generally, this Traditional technology filters only portions of less than 1 to 1024 Allow the occurrence of internal network traffic from all high-end ports 1024 to 16383.
Therefore, a better method called Stateful Inspection Packet Filter (As shown in Figure 3) adds the state-level inspection module between the data-link layer And the network layer. There is an entry for each connection currently established. this Enable incoming traffic in high-port ports only when packets fit Profile of one of the entries in the directory.
 |
| Figure 3 Stateful Inspection Packing-filtering |
2. Circuit-Level Gateway: Circuit-level gateway (as shown in Figure 4), which is [Described in Tom (2001)], provides a controlled network connection Internal and external systems It works on the transport layer. This kind of firewall The safety mechanism applies when the TCP or UDP connection is established.
A virtual "Circuit" is built between the internal client and the proxy server. Internal Client requests are sent through the circuit to proxy servers and proxy servers After changing the IP address, this request sends over the internet. External users Only see the IP address of the proxy server. When the proxy server receives
A virtual "Circuit" is built between the internal client and the proxy server. Internal Client requests are sent through the circuit to proxy servers and proxy servers After changing the IP address, this request sends over the internet. External users Only see the IP address of the proxy server. When the proxy server receives
Reactions and then send them back to the client through the circuit. although The traffic is allowed to go through, external users never know the internal systems. This type of connection is often used to connect "reliable" internal customers Internet. As soon as the connection has been created, these data packets can be flown.
Without further investigation between the hosts
 |
| Figure 4 Circuit-Level Gateway |
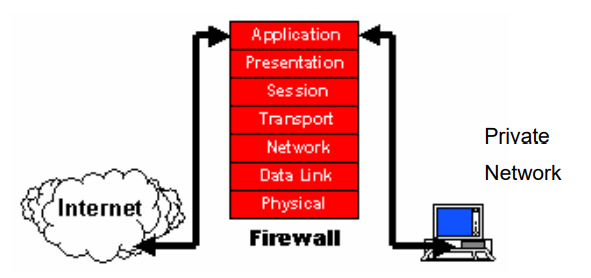
(3). Application-Level Gateway: As shown in [Tom (2001)], application level The entrance gateway (as shown in Figure 5) can provide all basic features of Proxy and A Comprehensive packet analysis. It implements a security mechanism for some special
FTP and Telnet services, such as applications, and also interfere through it Managing the entrance and traffic from both inside and outside
The application layer is defined in the OSI model. When Packets Come They are examined and evaluated by the gateway, gateway from the external network To determine whether they are allowed to enter the internal network according to security Policy. The server not only checks the IP address of these packets but also verifies what is it The data in these packets is of a trusted user or a deadly hacker. The disadvantage of such a firewall is that performance may fall, but This is the most effective and popular.
 |
| Figure 5 Application-Level Gateway |
Both of these doors can provide more opportunities for surveillance
Prevent access between different networks because they work on higher layers.
The entrance works as a moderate person and they obtain data packets from the internal customers For external services. Proxy service hides the client by changing the internet The IP address of data packets And on the other hand, it also acts as an agent
Customers on the Internet
How to Bypass Firewalls
As mentioned above, there are various types of firewalls and each of them has its advantage and disadvantage. In the following section, we will talk about something definite Ways to Bypass Firewalls
(1). IP Address Spoofing: an effective way to bypass IP address spoofing Firewall As mentioned in [Matthew (2003.3)], users gain unauthorized access The computer or the network makes it clear that the message came from a reliable The machine's IP address by machine "spoofing" To fully understand how It works, we should review the structure of the TCP / IP protocol suite.
Basic The understanding of these headers and network exchanges is essential for the whole process. Internet Protocol (IP) is a network protocol that works on network layers OSI model. This protocol is no connection and there is no information in this regard.
Transaction status used to route data packets over the network.
 |
| Figure 6 IP Packet Header |
As shown in Figure 6, the IP packet header has the first 12 bytes
Miscellaneous information about packets, However, the next 8 bytes will have a source And destination IP addresses. Using some types of devices, users can easily modify These address information in the IP packet header, especially the source address bits Fields, to bypass the firewall to create them.
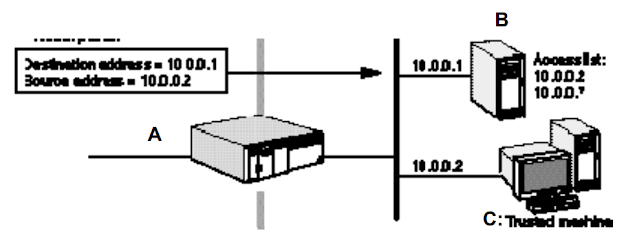
For example, suppose we have three hosts A, B, and C. Host C is a reliable The host BK machine. Now, the host wants to send some packets to host A and A By changing the IP address of these packets indicates itself as C (shown) Figure 7). When these packets are received, then B thinks that these packets are C, But in reality, they are from A.
 |
| Figure 7 IP Address Spoofing |
2). Source Routing: As presented in [ISS], Source Routing is another way Bypassing the firewall and the packet sender can specify the path that needs a packet Take through the network. When these packets travel between the nodes in the network,
Each router will check the IP address of the destination in these packets and choose To forward them to the next node. In the source routing, the sender makes some or all of these The decision on Router. In Figure 8, it shows the principle of the source path
But this is an optimal way, which makes all the decisions of the next hop.
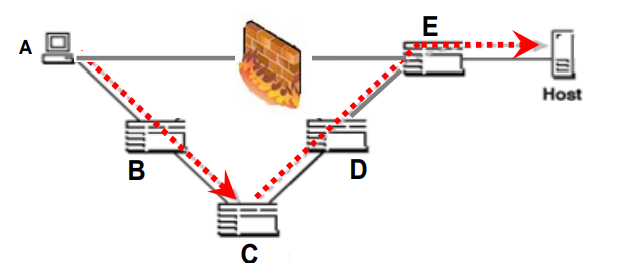 |
| Figure 8 Source Routing |
(3). Tiny Fragments: The way of small pieces is also an effective way Bypass the firewall and through this, the user uses IP fragmentation to make Very small pieces and TCP headers compel the information to separate Packet pieces. This method is designed to bypass filtering rules that depend on TCP header information Users expect that only the first piece is examined The filtering router and the remaining fractions are passed. The way The work of Tiny Fragment has been defined and explained [Zimba (1995.10)
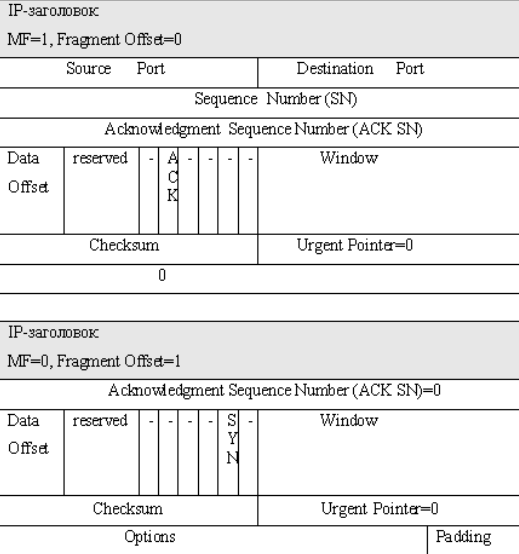 |
| Figure 9 TCP Packet Header |
As shown in Figure 9, the TCP header is very different from the IP header. it is us TCP is interested with the first 12 bytes of packets, which contains the information Ports and sequence numbers. As with IP packets, TCP packets can also be Manipulate by some tools or software. Host the Source and Destination Ports, For example, rely on network applications, for example, via FTP 21 and via FTP and SSH Port 22
The functionality of small pieces method is to make the TCP header packet in the block Extremely small sections, which are smaller than the size of the minimum piece Defined in filter rules. Therefore, these packets are free to check by the firewall. For example, all Internet modules 68 should be able to forward the datagrams. Octet without further fragmentation. This is because of the size of the internet header Must be up to 60 octets, and the minimum piece is 8 octets.
Last but not least, there are some other "illegal" ways to bypass the firewall, Such as rootkit and trojan. They are not just using some tricks to bypass firewalls, But changing the rule or eliminating the firewall in a certain way.
Related:


.png)














No comments:
Post a Comment