What is E-Mail Security?
Everyone uses E-Mail. This is the second most used application on the Internet next to your web Browser But what you can not feel is an important part of network attacks and The agreement is done through e-mail. And regarding your privacy, e-mail has misused The ability to disclose the content of your message or to give spammer information About you. The objective of this module is to give you information about how e-mail works, secure e-mail usage, e-mail based attacks, and security strategies for E-Mail.
How E-Mail Works
As the airmail is sent through the air, 'e-mail' is sent through 'e' - in this case, 'e' Web of electronic connections between and within the network Internet. When you send an e-mail from your Computer, the data is sent from your computer For an SMTP server The SMTP server then searches for the correct POP3 server and sends you E-mail the server where he waits until your intended recipient receives it again.Email Accounts
E-Mail accounts are available from many different sources. You can get through one School, through your work or through your ISP. When you get an e-mail account, you can Two-part e-mail address is given in this section: username@domain.name first part, Username recognizes you on your network, separates you from all other users Networks Second part, domain.name is used to identify your specific network.
The user name must be unique within your network, such as the domain name should be unique
Between all other networks on the Internet However, user names are not unique Their networks; It is possible for two users to share user names on two different networks.
For Example, if there is a user with address @@www.thehacktech.in, then the second will not be
The user whose username is billed at bignetwork.net However, Bill @@www.thehacktech.in and
Bill@www.thehacktech.in are both valid e-mail addresses that can refer to different users.
When you are setting up your email, the first thing that comes in your e-mail is - Mail address in your e-mail client program Your e-mail client is a program that you will use To send and receive e-mails. Microsoft's Outlook Express may be the most widely known (since then It comes free with every copy of the Microsoft operating system), but there are many others Available for both Windows and Linux including Mozilla, Eudora, Thunderbird, and Pine.
POP and SMTP
Once your e-mail client knows your e-mail address, you need to know where to look for it Where to send incoming e-mails and outgoing e-mails.
Your incoming e-mails are called POP servers on the computer. POP server - Usually the name of something like pop.smallnetwork.net or mail.smallnetwork.net - there is a file on it.
This is associated with your e-mail address and has the e-mail sent to You somebody else POP stands for Post Office Protocol.
Your outgoing e-mail will be sent to a computer called the SMTP server. This server - designated smtp.smallnetwork.net - will see the domain name contained in any e-mail address The e-mail you send, the DNS lookup will determine which POP3 server is Should send the e-mail to SMTP is for the Simple Mail Transfer Protocol.
When you start your e-mail client, there are several things:
The first thing to note is that you do not send Passwords on the SMTP server. SMTP is an old one
The protocol is built in the early days of e-mail, at a time when almost all The Internet knew each other individually. The protocol was written with the notion that
Everyone who is using it will be reliable, so the SMTP does not check to ensure that You are you Most SMTP servers use other methods to authenticate users but in theory - Anyone can use any SMTP server to send e-mails.
- The client opens a network connection to the POP server
- The client sends your secret password to the POP server
- the POP server sends your incoming e-mail to your local Computer
- The client sends outgoing e-mails to the SMTP server.
The protocol is built in the early days of e-mail, at a time when almost all The Internet knew each other individually. The protocol was written with the notion that
Everyone who is using it will be reliable, so the SMTP does not check to ensure that You are you Most SMTP servers use other methods to authenticate users but in theory - Anyone can use any SMTP server to send e-mails.
Forged Headers
The other thing is when you send your secret password to the POP server, you Send it in a plain-text format. It may be hidden by very little asterisks on your Computer screen, but It is transmitted through a network in an easily readable format. Who is monitoring?
For example, traffic on the network using packet sniffer - will be able to see you clearly Password. You can feel certain that your network is safe, but you have control Being on another network through which your data may pass.
Third, and possibly the most important thing you need to know about your e-mail is that They are - like your password - transmitted and stored in a plain text format. so may They can be monitored at any time, which is transferred from the server to your Computer.
It all adds up to one truth: e-mail information is not a safe way to move. sure it's Jokes are great for relaying and sending spankball alerts, but, if you are not comfortable Something is screaming through your window from your neighbor, so you should think About two times to put in an e-mail.
Is that sound crazy? Okay, yes, it's crazy, but it is not necessary to make itlie. Most of our e-mail communications are about unimportant details. no one but you, Bob and Alice take care of their dinner plans for the next Tuesday. And, even if Carol strict Want to know what you and Bob and Alice are eating next Tuesday, Odds are Slim You have a packet sniffer running on any network, so your e-mail can pass. but if It is unlikely that a company is known to use e-mail to arrange credit card transactions. Assume that someone has, or is setting a method to sniff that credit card number Out of network traffic.
WebMail
Another option for e-mail is to use a web-based e-mail account. This will allow you to use one
Web browser to check your e-mail. Since e-mails are generally stored for these accounts
Web e-mail server - not on your local computer - using them is very convenient Services from many computers It is possible that your ISP will allow you to use your e-mail Through both POP and Web.
However, you should remember that web pages are cached or stored on local computers, Occasionally for a significant length. If you check your e-mail through a web-based The system on someone else's computer, is a good opportunity to have your e-mail Accessible to anyone else who uses that computer
Web-based e-mail accounts are often free and easy. That means they offer an offer Opportunity is for you many identities online. For example, you may have an e-mail The address that you use only for friends and the other that is for relatives only. it's usually Acceptable unless you intentionally intend to deceive someone.
The other thing is when you send your secret password to the POP server, you Send it in a plain-text format. It may be hidden by very little asterisks on your Computer screen, but It is transmitted through a network in an easily readable format. Who is monitoring?
For example, traffic on the network using packet sniffer - will be able to see you clearly Password. You can feel certain that your network is safe, but you have control Being on another network through which your data may pass.
Third, and possibly the most important thing you need to know about your e-mail is that They are - like your password - transmitted and stored in a plain text format. so may They can be monitored at any time, which is transferred from the server to your Computer.
It all adds up to one truth: e-mail information is not a safe way to move. sure it's Jokes are great for relaying and sending spankball alerts, but, if you are not comfortable Something is screaming through your window from your neighbor, so you should think About two times to put in an e-mail.
Is that sound crazy? Okay, yes, it's crazy, but it is not necessary to make itlie. Most of our e-mail communications are about unimportant details. no one but you, Bob and Alice take care of their dinner plans for the next Tuesday. And, even if Carol strict Want to know what you and Bob and Alice are eating next Tuesday, Odds are Slim You have a packet sniffer running on any network, so your e-mail can pass. but if It is unlikely that a company is known to use e-mail to arrange credit card transactions. Assume that someone has, or is setting a method to sniff that credit card number Out of network traffic.
WebMail
Another option for e-mail is to use a web-based e-mail account. This will allow you to use one
Web browser to check your e-mail. Since e-mails are generally stored for these accounts
Web e-mail server - not on your local computer - using them is very convenient Services from many computers It is possible that your ISP will allow you to use your e-mail Through both POP and Web.
However, you should remember that web pages are cached or stored on local computers, Occasionally for a significant length. If you check your e-mail through a web-based The system on someone else's computer, is a good opportunity to have your e-mail Accessible to anyone else who uses that computer
Web-based e-mail accounts are often free and easy. That means they offer an offer Opportunity is for you many identities online. For example, you may have an e-mail The address that you use only for friends and the other that is for relatives only. it's usually Acceptable unless you intentionally intend to deceive someone.
Secure Email Usage Part 1: Getting
Everyone uses e-mail, and against the surprise of many people, your e-mail can be used you. E-mail should be treated as a postcard, whatever it looks, can read it materially. You should never put anything in a simple e-mail that you do not want to do Read. It is said that there are strategies for securing your e-mail. In this part, we will cover How to use safe and secure e-mail and protect your privacy online.
Spam, Phishing, and Fraud
Everyone likes to receive e-mails. Long ago, very far in a galaxy, it used to be only You got mail from those you knew, and it was about the things you cared about. Now you can use e- The emails of those you have never heard about asking to buy software, drugs and real estate To help them mention, they get $ 24 million from Nigeria. This type of unwanted advertisement is Spam is called. It is surprising to many people that they can provide an e-mail they receive To the sender a lot of information, such as when the mail was opened and how many times it happened Read, if it was forwarded, etc.
This type of technique - called web bug - both are used Spammers and legitimate senders Also, click to reply to an email or unsubscribe The link can tell the sender that they have reached the live address. Another Invasion of Privacy Worry is a common "Phishing" attack. Have you ever received an e-mail Are you asking to log in and verify your bank or e-bay account information? Beware, because it is A trick to steal your account information To protect itself against these types of attacks, Below are some simple strategies to protect yourself.
HTML E-Mail
One of the security concerns with HTML based e-mail is the use of web bugs. Are web bugs Hidden images in your e-mail that connects to senders' web servers, and provides them The notification you have received or the mail has been opened. There is another flaw with HTML e-mail The sender can embed the link in the e-mail that recognizes the person who clicks on them.
From this, the sender can get information about the status of the message. As a rule, you need to Use a mail client that allows you to disable or download automatic downloads.
Embedded images Another problem relates to the script in an e-mail that could be a launch The application if your browser has not been patched for security flaws.
For web-based e-mail clients, you may have the option of disabling automatic downloads See pictures or message as text. Either there is a good safety practice. the best way to Protecting yourself against HTML-based security and privacy attacks is the use of text-based e- similarity. If you use HTML e-mail, be careful!
Attachment Security
Another genuine concern attached to e-mail security is the attachment. Can send the attacker You get malware, viruses, Trojan horses and all kinds of dirty programs. The best defense against The e-mail generated malware is for nothing to open anything from anyone you know. Never open File extensions with .exe or .scr, because these are extensions that will launch an executable file Which can infect your computer with a Virus?
For good measure, you should have any file you received Saved to your hard drive and scanned with an antivirus program. Beware of files that appear A well-known file type, such as a zip file. Sometimes changing the attacker file can change disguise Hide icon or file extension so that you do not know that it's an executable.
Forged Headers
Occasionally you may receive an e-mail, which seems like it is from someone you know or acquainted with "Administrator" or "Postmaster" or "Security Team" in your school or ISP. The subject may be "Return Mail" or "Hacking Activity" or some other interesting topic. There will often be Be an attachment
The problem is that it does not take any technical knowledge and is about 10 A few seconds of work to create an e-mail address. (This also - depends on where you live - may be Is very illegal.)
To do this, you make a simple change to the settings in your e-mail client software. Where is this Asks you to enter your e-mail address (under option, settings or priority) anything else. Here's a fake return address in all your messages.
Is this Does it mean that you are safe from identity? Not really. Anyone with the ability to read e-mail The purchase of mail headers and a search warrant may detect your identity Information on the header. What does it mean that a spammer can represent He wants himself as someone. So if Fannie Geotoku [telecommunicatecreatures@cox.net] You sell a magical cell phone antenna which becomes a grain box covered with tin foil, You can complain with cox.net, but do not be surprised when they tell you it is not the user.
Most ISPs certify the senders and prevent them from the relay, which means that who you are You say that you are sending mail through their SMTP server. The problem is of hackers and spammers Often run an SMTP server on your PC and thus does not have to be certified to send e-mail, and It can appear in any way they want. A suspicious e-mail is a surefire way to know Valid is to know the sender and call them.
Never respond to messages that you suspect It may be forged because the sender may know that they have reached the actual address. You can do this Also, check the header information to determine where the mail came from
The following examples:
This is the e-mail of a person I do not know, with a suspicious attachment. Generally, I will do
Just remove it but I want to know where it came from. So I'll look at the message headers. IUse Outlook 2003 as my e-mail client, and you go to> Options> and you to see the header
The header information is given below:
Now, the part I am interested in has been highlighted above. Note that "Received" is from Kara.org on an IP that appears to be a xo.net DSL line, which does not agree with innovonics.com, the alleged sender.
In addition, if I look at the mail server of innovonics.com using nslookup, its address is returned
is as follows:
Therefore, my suspicions were correct, and it is an e-mail that is taking some malware into one
Executable file as a zip file. Malware has infected the person's computer The DSL line, which is now a zombie, is sending copies of malware to everyone in the infected computer Address Book I'm glad I checked it
Secure Email Usage Part 2: Send
Sending mail is a bit more care-free. There are some things that you can do to ensure that your
However, the conversation is safe. First, make sure your connection is secure ( Connection security for more information).
There are also methods to allow you digitally Sign your messages, which guarantees that the message is from you or not Tampering on the way. And for maximum security, you can encrypt to create your messages Not sure anyone does not read them.
Digital signatures prove who comes from e-mail and that it has not been changed in transit. if
If you establish a habit of using digital signatures for important e-mails, then you will have a lot
Reliability If you ever need to discard fake mail that appears to you. They also allow You have to encrypt the e-mail so that no one can read it except the recipient. Special offers include PGP To break the high level of encryption, excessive computing power will be required.
Digital Certificate
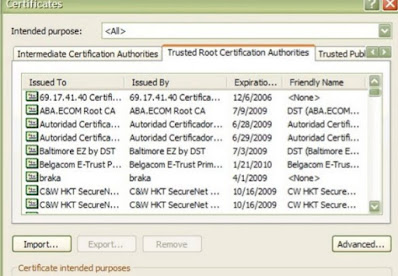
A digital certificate is unique to a person, like a driver's license or passport, and is Made up of 2 parts. These parts are a public and private key. Unique to the certificate A person, and usually the certificates are issued by a Trusted Certificate Authority, or CA. The list of certificate officials you trust is automatically delivered (if you are a Microsoft Windows Update by Windows users) and the list is available in your browser Tools> Internet Options> Content> Certificates. You can go here to see the certificate established here Your machine (you and others), and other certificate authority you trust.
You can disable automatic updates to CA, and you can choose to remove all CA from the list,
Although it is not recommended. Instructions for doing so are on Microsoft's web site.
Digital Signature
A digital signature is guaranteed by your e-mail software and your personal key The authenticity of your e-mail. The purpose of the signature is two times. The first thing to do is to prove it
It came from you, it is called non-repatriation. Second, to ensure that there is no content has been changed. This is called data integrity. The way an e-mail program completes it Run the contents of your message through a hash function in a way. It produces a definite The size of your e-mail output called the message digest. This is a unique value, and if A mathematical algorithm which creates it, it is strong, the digestive message has the following Reveal the responsible.
- Digest original message cannot be reproduced with Digest.
- Each digestion is unique
PGP is more often a computer user's choice Community, because it is based on the Trust's non-centralized web for authentication, where A The user's credibility is valid through the 'friends of a friend' system, where you agree that, If you trust me, then you can count on those whom I believe and because of the members The computer user community really does not care if they take four hours to figure out how PGP works with Thunderbird - they consider this form of a form of challenges
entertainment.
Getting a Certificate
If you are interested in getting a digital certificate or digital ID, you need to contact
Certificate Authority (Verisign and Thawte are most famous, although there is a web search
Others can get.) Both of you need to provide the identity to prove who you are
You there. You can get a free certificate from the thaw, but they require a significant amount
A government identification number (such as passport, tax enclosure) personal information
ID or driver's license).
Verisign charges a fee for your certificate and you need to pay this fee With a credit card, but asks for less personal information. (Probably, relying on Verisign The credit card company to validate your personal information.) These requests for information Intrusion can happen, but remember, you are asking these companies to vouchers for your Reliability. And - as usual - check with your parents or guardians before giving out Any personal information (or large balance on their credit card)
The biggest disadvantage of using certificate authority is that your private key is available
Certification Authority - to someone else. If the certificate is signed with the Authority, then
Your digital ID is also compromised.
Encryption
As an additional layer of security, you can encrypt your e-mail. Encryption will turn on your e-mail
Text in a glitch of numbers and letters that can be read only by your desired gonna get. Your deepest secret and your worst poem will be hidden from everyone Trusted eyes
However, you should remember that while it may look good to you - and all of us In fact, there is no desire to face bad poetry - some governments do not approve. what is ours Logic - can be valid or may not (you can discuss it among themselves), but validity It does not matter. The point is that depending on the laws of the country you live in, Sending an encrypted email can lead to crime regardless of the content.
How does it work?
Encryption is quite complex so I will try to explain it in a less technical way:
Jason wants to send an encrypted message. So Jason does the first thing to go to one
Get certificate authority and a digital certificate. This certificate has two parts, a public key
And a private key.
If Jason wants to send and send encrypted messages with his friend's rent, they have to do first
Public key exchange If you have a public key of the certificate authority that you have Chosen for trust, the key can be automatically verified back to that certified authority. This means that your e-mail program will certify that the certificate is valid, and it has not been revoked.
If the certificate does not come from the authorization to which you trust or the PGP key, then you need it Verify Key Fingerprint Usually, this is done separately, either face the exchange with one face Key or fingerprint data
Now let's assume that both Rent and Jason are using compatible encryption schemes, and Signed messages are exchanged, so they have each other's public key.
When Jason wants to send an encrypted message, the encryption process begins Changing the text of Jason's message into a former hash code. This code is generated using one The mathematical formula called encryption algorithm. There are many types of algorithms, But S / MIME and PGP are the most common for e-mail.
Jason's message hash code is encrypted using Jason's private by e-mail program Key. Jason again uses Kira's public key to encrypt the message, so only Kira can decrypt with it His private key, and it completes the encryption process.
Decryption
So the rent got an encrypted message from Jason. This is usually indicated by a lock The icon on the message in the box. The decryption process is controlled by e-mail Software, but behind the scenes is something like this: Kira's e-mail program Uses his private key to understand encrypted pre-hash codes and encrypted messages. Then Jason's public key is remembered from storage in the rental e-mail program (remember, we Keys previously have done).
This public key is used to decrypt and verify the pre-hash code The message came from Jason. Kira's e-mail program then creates a post hash code message. If the post hash code is the same as the hash code, the message has not changed In the Road.
Note: If you lose your private key, then your encrypted files become useless, so it is important
There is a process for backing up your personal and public key.
Is Encryption Incompatible?
According to the number, the level of encryption, for example, is PGP Unbreakable, Of course, one million computers working on breaking it will eventually succeed, but Before millions of monkeys did not finish their script for Romeo and Juliet. number theory This type of encryption involves involving the products of very large prime numbers, And despite the fact that mathematicians have studied the prime numbers for years, There is no easy way to do this.
But encryption and privacy are more than numbers. However, if someone else has Access to your private key, then you have access to all of their encrypted files. Encryption Only works when it is part of a large security framework that protects you both Private key and your pass-phrase.
Connection Protection
Last but not least connection protection. For webmail, make sure you are using an SSL Connection to your ISP e-mail. You will see a small lock icon at a time below Browser If you are using POP and an email client, make sure that you have re-configured your Mail Client to use SSL with SMTP on POP and Port 465 on port 995.
It encrypts your mail To protect you on your server, as well as your POP / SMTP username and password. Your ISP How to configure it on their web site If they do not give safe POP / Change SMTP Connection, ISPs!
Related:


.png)

















No comments:
Post a Comment