What is Virtual Private Network?
There are many improvements, including the quality of service, network in the Internet Performance, and affordable technologies, such as DSL But one of the most important advances Virtual Private Networking (VPN) has been in Internet Protocol Security (IPSec). IPSec is one of these Developed for most complete, secure and commercially available, standards-based protocols
Transporting data.
A VPN is a shared network where private data is divided by other traffic so that only The intended recipient has access. The term VPN was originally used to describe a secure connection On the Internet. Today, however, VPN is also used to describe the private network in the form of a frame
Relay, asynchronous transfer mode (ATM), and multiprotocol label switching (MPLS).
One of the major aspects of data security is that the flow of data across the network is protected by encryption.
Technologies Private network lacks data security so data attackers can tap directly Read more data in the network. IPSec-based VPNs use encryption to provide data protection, Which increases the network's resistance to tampering or theft of data.
IPSec-based VPN can be built on any type of IP network, including the internet frame. Relay, ATM and MPLS, but the internet is simply ubiquitous and inexpensive.
VPNs are Traditionally Used:
Intranet: The intranet connects the locations of an organization. From these places Headquarter office, in branch offices, to a remote employee's house. Often this connectivity Is used to share e-mails and applications and files. While Frame Relay, ATM, and MPLS Fulfill these tasks, the limitations of each boundary connectivity. The cost to add Home users is also very expensive compared to internet access technologies, such as DSL or Cable. Because of this, organizations are transferring their network to the Internet, which is Affordable to create these networks and using IPSec.
Remote Access: enables telecommunications and mobile employees to use remote access e-mail
And business applications. The dial-up connection of an organization's modem pool is one
The method of use for remote workers, but it is expensive because the organization has to pay
Connected long distance telephone and service costs. Remote Access VPNs Are Very Low
Enabling mobile workers to dial local internet connection and then set up a setup
Secure IPSec-based VPN communication for your organization
Extranets: Extranet has a secure connection between two or more organizations. Normal Use for Supply of ExtraNet-Series Management, Development Partnerships, and Subscription services. These ventures can be difficult to use legacy network techniques Due to the cost of connection, delay of time and availability Ideal for IPSec-based VPNs Extranet connection. IPSec-enabled devices can be installed quickly and cheaply Existing Internet Connection
What is IPSec and How does it Works?
IPSec is the standard suite of an Internet Engineering Task Force (IETF) protocol that provides data
Data is transferred between communication points in the form of authentication, integrity, and privacy In the whole IP network, IPSec provides data protection at the IP packet level. A packet is a data bundle.
That is organized for transmission in a network, and includes header and payload (data) In packets). IPSec emerged as a viable network security standard because the enterprise wanted to Ensure that the data can be transmitted securely over the Internet. IPSec prevents possible Security risks by data protection in transit.ures
IPSec is the safest way to commercially available network sites. IPSec was Designed to provide the following security features while transferring packets over the network:
Authentication: Verifies that the received packets are actually of the claimed sender.
Integrity: It ensures that the cont.
IPSec Security Features
IPSec is the safest way to commercially available network sites. IPSec was Designed to provide the following security features while transferring packets over the network:
- Authentication: Verifies that the received packets are actually of the claimed sender.
- Integrity: It ensures that the contents of the packet do not change in transit.
- Privacy: Includes message content via encryption.
IPSec contains the following elements:
- Encapsulating Security Payload (ESP): Provides confidentiality, authentication, and integrity.
- Authentication Header (AH): Provides authentication and integrity.
- Internet Exchange (IKE): Provides Management of Major Management and Security Associations (SA).
ESP provides certification, integrity, and privacy, which prevents data from tampering And, most importantly, providing message content protection.
Provides an open framework to implement industry-standard algorithms such as IPSec SHA And MD5 The algorithm IPSec uses a unique and inefficient identifier for each packet, Which is the equivalent data of a fingerprint. This fingerprint allows the device to determine whether The packet has been tampered with. In addition, such packets that are not certified are left and
The desired receiver was not reached.
ESP also provides all encryption services in IPSec. Encryption translates a readable message An unreadable format to hide message content. The opposite process, which is called decryption, Translates message content from an unreadable format to a readable message. Encryption / Decryption only allows the sender and authorized the receiver to read data. Also, there is ESP
An alternative to authentication, which is called ESP authentication. ESP authentication, using ESP
Provides authentication and integrity for payload and not for IP header.
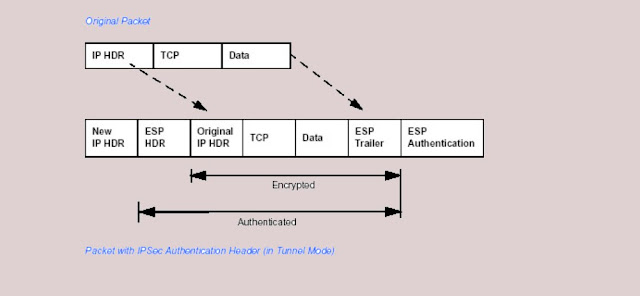
ESP header is inserted in the packet between the IP header and any subsequent packets material. However, because ESP encrypts the data, the payload is changed. ESP does not encrypt ESP header, nor does it encrypt ESP authentication.
Authentication Header (AH)
AH provides authentication and integrity, which protects against data tampering, using the same
The algorithm as ESP AH also provides alternative anti-replay protection, which prevents it Unauthorized rescheduling of packets. Authentication header is inserted into the packet
Between the IP header and any subsequent packet contents. Payload has not been touched.
Although AH protects the packet from being tangled with the origin, destination, and content,
The identity of the sender and the receiver is known. Besides, AH does not protect the data
Privacy If the data is intercepted and only AH is used, then the message content can be read. ESP
Data protects privacy. For additional protection in some cases, AH and ESP can be used
Together. In the following table, the IP HDR represents the IP header and contains the source and both Destination IP address
Security Association
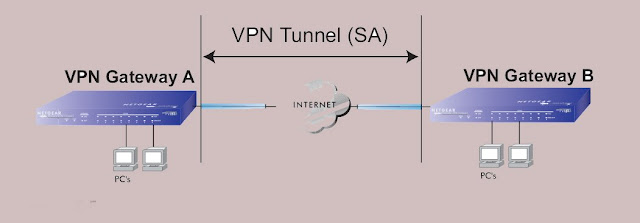
Introduces the concept of the IPSec Security Association (SA). SA is a logical connection Between two devices transferring data A SA provides data protection for unidirectional traffic Using the Defined IPSec Protocol. An IPSec tunnel usually has two unidirectional SAs, Which provide a protected, full-duplex data channel simultaneously.
SAS allows an enterprise to properly control which resources can communicate safely, According to the security policy. To do this, one enterprise can set several SAS to enable many Secure VPN, as well as define SAS within VPN to support various departments and businesses
Partners.
Mode
Work using SAS mode. One mode is the method in which the IPSec protocol is implemented
a packet. IPSec can be used in tunnel mode or in transport mode. Typically, tunnel mode is used
Gateway to Gateway IPSec tunnel protection, but transport mode is used for host-to-host IPSec
Tunnel protection An entrance door is a device that monitors incoming and outgoing people
Route traffic to traffic and traffic accordingly A host is a device that sends and receives
network traffic.
- Transport Mode: Transport mode IPSec implementation only encounters packets Payload The IP header has not changed. After processing the packet with IPSec, the new IP The packet contains the old IP header (source and destination IP address unchanged) And processed packet payload. Transport mode does not shield information in IP Header; Therefore, an attacker can learn where the packet is coming from and where it is going To. Figure 2-1 and Figure 2-2 show a packet in the above transport mode.
- Tunnel Mode: Tunnel mode IPSec implementation encapsulates the entire IP packet. The packet of packets to be processed with the entire packet IPSec is created. A new IP header Has been created which includes two IPSec gateway addresses. Perform the gateway Encapsulation/decapsulation on behalf of hosts Tunnel mode ESP prevents an attacker As well as analyzing and decrypting the data, it should also know who the packet is and whose Where is this going
IPSec SA uses the Internet Key Exchange (IKE) protocol for setup and convenience and
Keyword exchanges between parties transferring data The use of keys ensure that only sender
And the receiver of the message can access it.
IPSec requires that the keys be rebuilt, or refreshed so that parties can communicate Safely with each other Manages the process of refreshing the IKE key; However, a user can control Key strength and refresh frequency. Refreshes the key data on a regular basis Privacy between the sender and the receiver.
Understand the Process Before Starting
This manual provides examples of how to configure a secure IPSec VPN tunnel. this document
The reader assumes that NETGEAR management systems have a working knowledge.
NETGEAR, Inc. VPN is a member of Consortium, which is a group formed to facilitate IPSec VPN
Seller Difference VPN Consortium has developed specific scenarios to assist the system
Administrators often fall into the confusing process of adding two different vendor implementations
IPSec standard. The examples of this manual follow the address and configuration
Mechanics defined by the VPN Consortium Additional information regarding inter-seller
Interoperability can be found at https://www.vpnc.org/
It is a good idea to gather all the information you need to install VPN before you
Start the configuration process. You should understand whether the firmware is up-to-date, all
Those addresses that will be required, and all parameters that need to be set on both sides. try
To understand any inconsistency before starting, so that you can minimize any potential
Complications that may arise from common firewalls or WAN processes.
If you are not a full-time system administrator, it is a good idea to familiarize yourself with it
The mechanics of a VPN The brief description below in this document will help. Other good sources
Include:
- VPN Consortium - https://www.vpnc.org
VPN Process Overview
Even if IPSec is standards-based, but each vendor has its own set of conditions and procedures
Applying Standards. Due to these differences, reviewing something can be a good idea Rules and general procedure for adding two gateways before entering Nuances
Network Interfaces and Addresses
VPN Gateway is given the appropriate name because it acts as a "gatekeeper" for each Computer
It is connected to a Local Area Network.
In most cases, a "public" address (WAN side) and a "private" face at each entrance
Address (LAN side) These addresses are known in the documentation as "Network Interface"
About the creation of VPN communication Please note that addresses used in
Examples.
Interface Addressing
This document uses the VPN Consortium provided the example address. It is necessary that
Understand that you are using a specific address for the devices you are trying to do
Connect via IPSec VPN.
It is also important to ensure that addresses do not overlap or conflict. That is, each set of
The addresses should be different and different.
Knowing the subnet mask of both gateway LAN connections will also be important. Use
To gather the necessary address and subnet mask information for worksheet support in Appendix A
Configuration and troubleshooting process
Firewall
It is important to understand that there are also many gateway Firewalls. VPN tunnels can not work
Correctly if firewall settings disrupt all incoming traffic. Please see the firewall instructions
To understand both gateways, how do you open specific protocols, ports, and addresses
Want to give permission
Setting Up a VPN Tunnel Between Gateways
An SA often called a tunnel, is a set of information that allows two entities (Network, PC)
Router, Firewall, gateway) "Trust each other" and communicate safely when near you
Information on the Internet
SA has all the information necessary to secure and encrypted conversations for Gateway A
Communication stream with gateway b This communication is often known as "tunnel".
The gateway has this information so that it is not loaded on every computer Is connected to the gateway.
Each security gateway should negotiate with another gateway using the parameters to each gateway
And processes established by IPSec. The most common method, as shown below, is
This process is accomplished through the Internet Exchange (IKE) protocol which automates something Of negotiation processes Alternatively, you can configure your gateway by using the manual key The exchange, which involves manually configuring each parameter on both gateways.
In an attempt to communicate with the IPSec software on Host A, the IPSec process starts
Host b Two Computers then start Internet Exchange (IKE) process.
IKE phase I: a. Both parties interact on encryption and authentication algorithms for use in IK SA.
B. Both parties certify each other using a predetermined mechanism, such as prized keys or digital certificates.
C. A shared master key is created by the Diffie-Hellman public key algorithm within the IKE framework for both sides. To obtain an IPSec key for SAS, the master key is used in the second step.
IKE Phase II: a. Both sides interact on encryption and authentication algorithms for use in IPSec SAs.
B. The master key is used to obtain the IPSec key for SAs. Once the SA key is created and exchanged, IPSec SAs are ready to protect user data between two VPN gateways.
Data Transfer: Data is transferred between IPSec associates based on IPSec parameters and keys
SA stored in the database.
IPSec Tunnel Termination. IPSec SAs expires or expires through time.
VPNC IKE Security Parameters
It is important to remember that the same parameter should be set for both gateways
The process of working correctly In these examples, the settings follow the examples given for Scenario 1 of VPN Consortium's
VPNC IKE phase I Parameter
IKE used step 1 parameters:
- Main mode
- Triple D
- SHA-1
- MODP Group 1
- Pre-shared secrets of "hr5xb84l6aa9r6"
- The lifetime of 28800 seconds (eight hours)
VPNC IKE Phase II Parameter
The IKE step 2 parameters used in Scenario 1 are:
- Triple D
- SHA-1
- ESP tunnel mode
- MODP Group 1
- Perfect privacy for Reiki
- The lifetime of 28800 seconds (one hour)
Testing and Troubleshooting
Once you have completed the VPN configuration steps, you can use the computer, which is located
To ping different addresses on the LAN side of the second gateway, behind each gateway.
You can troubleshoot connection using the VPN status and log details on the NETGEAR gateway
To determine if IKE chat is working. Common problems faced in installing VPN
Include:
- Parameters can be configured separately on Gateway A versus Gateway B.
- Two LANs have been installed with the same or overlapping addressing scheme.
- Much of the required configuration parameters are mistakes, such as incorrect information or more likely to have mismatched parameter selections on both sides.
Also Read:


.png)





















No comments:
Post a Comment