Ethical Hacking Tutorials - What is Buffer Overflow Attack?
Buffer Overflow has been the most common form of a security vulnerability in the last ten years. Moreover buffer overflow vulnerabilities domain in the area of remote network penetration vulnerabilities, where an anonymous Internet user seeks to gain partial or total control of a host.
Because these kinds of attacks enable anyone to take total control of a host, they represent one of the most serious classes of security threats.
Buffer Overflow attacks form a substantial portion of all. Security attacks simply because buffer overflow vulnerabilities particularly dominate in the class of remote penetration attacks because a buffer overflow vulnerability presents the attacker with exactly what they need the ability to inject and execute attack code.
The injected attack code runs with the privileges of the vulnerable program and allows the attacker to bootstrap whatever other functionality is needed to control the host computer.
The overall goal of a buffer overflow attack is to subvert the function of a privileged program.
To achieve this goal, the attacker must achieve two sub-goal
1. Arrange for suitable code to be available in the program's address space.
2. Get the program to jump to that code, with suitable parameters loaded into register and memory.
A Buffer contains data that is stored for a short amount of time, typically in the computer's memory(RAM). The purpose of a buffer is to hold data right before it is used.
For example, When you Download an audio or video file from the Internet. it may load the first 20% if it into a buffer and then begin to play. While the clip pays back, the computer continually downloads the rest of the clip and stores it in the buffer. Because the clip is being played from the buffer, not directly from the Internet, there is network congestion.
The injected attack code runs with the privileges of the vulnerable program and allows the attacker to bootstrap whatever other functionality is needed to control the host computer.
The overall goal of a buffer overflow attack is to subvert the function of a privileged program.
To achieve this goal, the attacker must achieve two sub-goal
1. Arrange for suitable code to be available in the program's address space.
2. Get the program to jump to that code, with suitable parameters loaded into register and memory.
A Buffer contains data that is stored for a short amount of time, typically in the computer's memory(RAM). The purpose of a buffer is to hold data right before it is used.
For example, When you Download an audio or video file from the Internet. it may load the first 20% if it into a buffer and then begin to play. While the clip pays back, the computer continually downloads the rest of the clip and stores it in the buffer. Because the clip is being played from the buffer, not directly from the Internet, there is network congestion.
A data buffer (or just buffer) is a region of physical memory storage used to temporarily store data while it is being moved one place to another.
A Temporary Storage Area, usually in RAM. The purpose of most buffers is to act as a holding area, enabling the CPU to manipulate data before transferring it to a device.
Because the processes of reading and writing data to a disk are relatively slow, many programs keep track of data changes in a buffer and then copy the buffer to a disk. For example, word processors employ a buffer to keep track of changes to files.
What is Temporary Data Storage?
A Temporary Storage Area, usually in RAM. The purpose of most buffers is to act as a holding area, enabling the CPU to manipulate data before transferring it to a device.
Because the processes of reading and writing data to a disk are relatively slow, many programs keep track of data changes in a buffer and then copy the buffer to a disk. For example, word processors employ a buffer to keep track of changes to files.
Then when you save the file, the word processor updates the disk file with the contents of the buffer. This is much more efficient than accessing the file on the disk each time you make a change to the file.
Note: that because your changes are initially stored in a buffer, not on the disk, all of them will be lost if the computer fails during an editing session
Note: that because your changes are initially stored in a buffer, not on the disk, all of them will be lost if the computer fails during an editing session
For this reason, it is a goal idea to save your file periodically. Most word processors automatically save files at regular intervals.
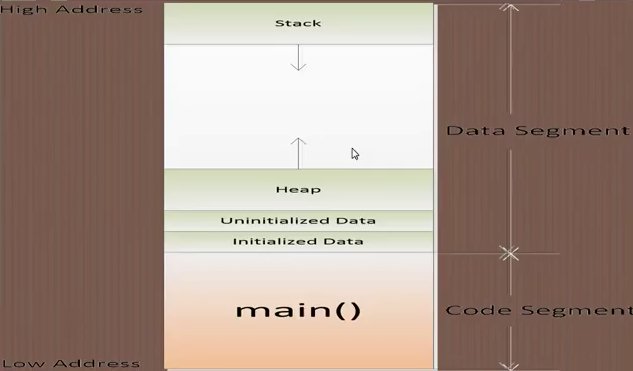
Heap Area in Programming Languages
In certain programming languages including C and Pascal, a heap is an area of pre-reserved computer main storage (memory) that a program process can use to store data in some variable amount that won't be known until the program is running.
Heap Area in Programming Languages
In certain programming languages including C and Pascal, a heap is an area of pre-reserved computer main storage (memory) that a program process can use to store data in some variable amount that won't be known until the program is running.
For example, a program may accept different amounts of input from one or more users for processing and then do the processing on all the input data at once. Having a certain amount of heap storage already obtained from the operating system makes it easier for the process to manage storage and is generally faster than aking the operating system for storage every time it's needed.
The process manages its allocated heap by requesting a "chunk" of the head (called ahead block) when needed, returning the blocks when no longer needed, and doing occasional "garbage collecting," which makes blocks available that are no longer being used and also reorganize the available space in the heap so that it isn't being wasted in small unusual pieces.
The term is apparently inspired by another term, Stack. A stack is similar to a heap except that the blocks are taken out of storage in a certain order and returned in the same way. In Pascal, a subhead is a portion
A heap is an area of preserved computer main storage (memory) that a program process can use to store data in some variable amount that won't be known until the program is running.
Mainly local variables are stored in the stack. After the program execution the stored data is automatically deleted and this for temporary storage. The memory block in the stack has a fixed size. If there is not enough memory on the stack to handle the memory being assigned to it, a Stack Overflow occurs.
The process manages its allocated heap by requesting a "chunk" of the head (called ahead block) when needed, returning the blocks when no longer needed, and doing occasional "garbage collecting," which makes blocks available that are no longer being used and also reorganize the available space in the heap so that it isn't being wasted in small unusual pieces.
The term is apparently inspired by another term, Stack. A stack is similar to a heap except that the blocks are taken out of storage in a certain order and returned in the same way. In Pascal, a subhead is a portion
Buffer Overflow Attack
A heap is an area of preserved computer main storage (memory) that a program process can use to store data in some variable amount that won't be known until the program is running.
Mainly local variables are stored in the stack. After the program execution the stored data is automatically deleted and this for temporary storage. The memory block in the stack has a fixed size. If there is not enough memory on the stack to handle the memory being assigned to it, a Stack Overflow occurs.
See: Ethical Hacking Tutorials - What is DoS Attack?
See: Ethical Hacking Tutorials - What is Session Hijacking?
Tags: buffer overflow,what is buffer overflow,what is buffer overflow attack in hindi,buffer overflow attack,buffer overflow attacks,what is the meaning of buffer overflow,what is the definition of buffer overflow,what does buffer overflow mean,buffer overflow attack in hindi,what does buffer overflow stand for,buffer overflow meaning,what is buffer overflow attack,buffer overflow vulnerability
See: Ethical Hacking Tutorials - What is Session Hijacking?
Tags: buffer overflow,what is buffer overflow,what is buffer overflow attack in hindi,buffer overflow attack,buffer overflow attacks,what is the meaning of buffer overflow,what is the definition of buffer overflow,what does buffer overflow mean,buffer overflow attack in hindi,what does buffer overflow stand for,buffer overflow meaning,what is buffer overflow attack,buffer overflow vulnerability


.png)















No comments:
Post a Comment