Ethical Hacking Tutorials - What is DOS Attack?
Denial of Service Attacks of DOS attacks are a form of organized attacks with the goal of taking down a server by overloading it. Often by sending useless information packets to a server in massive amounts.
A Denial-of-Service (DOS) Attack is an attempt to make a machine or network resource unavailable to its intended users, such as to temporarily or indefinitely interrupt or suspend services of a host connected to the Internet.
SYN Flood
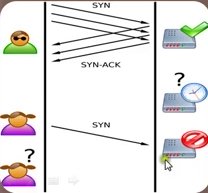
Normally when a client attempts to start a TCP connection to a server the client and server exchange a series of messages which normally runs like this:
- The client requests a connection by sending an SYN (synchronize) message to the server.
- The server acknowledges this request by sending SYN-ACK back to the client.
- The client responds with an ACK, and the connection is established.
TCP three-way handshake foundation for every connection established using the TCP protocol.
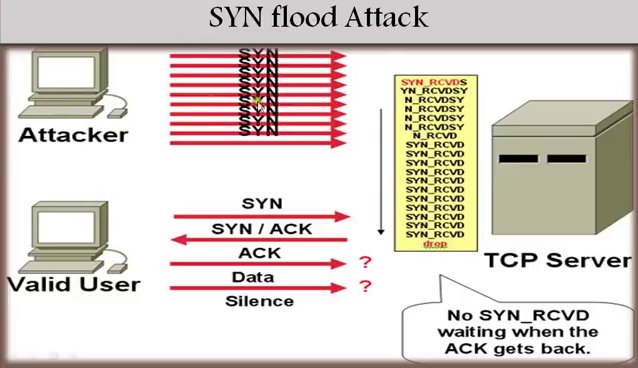
SYN Flood Attack
An SYN flood attack works by not responding to the server with the expected ACK code. The malicious client can either simply not send the expected ACK, or by spoofing the source IP address in the SYN, causing the server to send the SYN-ACK to a falsified IP address which will not send an ACK because it "knows" that it never sent an SYN.
The server will wait for the acknowledgment for some time, as simple network connection could also be the cause of the missing ACK However, in an attack, the half-open connections created by the malicious client bind resources on the server and may eventually exceed the resources available on the server.
At that point, the server cannot connect to any clients, whether legitimate or other.
Ping Flood Attack
Ping Flooding is the most primitive form of DoS attacks because anyone can do it extremely easily. When a targeted computer is under a ping flood attack, what happens is the computer's a ping request it has to compute it then send a reply with the same amount of data, ping flooding is when the attacker floods the server with ping requests and the server has to compute tons of requests every split second, which takes up a lot of resources.
ping IP address -t -l 65500
To understand the command here's the argument breakdown The -t specifies that it keeps pinging the host until it times out (Disconnects or until you stop it). -l specifies the load you want to send, so we are sending 65500 bytes to the host every ping. That's quite a lot of data to handle, the usual default ping size is 32 bytes.
Ping of Death is a type of Denial of Service (DOS) attack in which an attacker attempts to crash, destabilize, or freeze the targeted computer or service by sending malformed or oversized packets using a simple ping command.
Ping Flooding is the most primitive form of DoS attacks because anyone can do it extremely easily. When a targeted computer is under a ping flood attack, what happens is the computer's a ping request it has to compute it then send a reply with the same amount of data, ping flooding is when the attacker floods the server with ping requests and the server has to compute tons of requests every split second, which takes up a lot of resources.
ping IP address -t -l 65500
To understand the command here's the argument breakdown The -t specifies that it keeps pinging the host until it times out (Disconnects or until you stop it). -l specifies the load you want to send, so we are sending 65500 bytes to the host every ping. That's quite a lot of data to handle, the usual default ping size is 32 bytes.
Ping of Death is a type of Denial of Service (DOS) attack in which an attacker attempts to crash, destabilize, or freeze the targeted computer or service by sending malformed or oversized packets using a simple ping command.
Tags: ddos attack,what is dos attack,attack,dos,dos attack,what is ddos attack,denial-of-service attack,denial-of-service attack (literature subject),what is ddos,what is dos attack in hindi,what is a ddos,ddos attacks,dos attack hindi,dos attack in hindi,what is a ddos attack,attacks,ddos attack live,what is ddos attack in hindi,ddos,how ddos attack work,ddos attack tool,what are ddos attacks


.png)














No comments:
Post a Comment