There are lots of programs on your Computer that want to open a network connection. Some of these programs are legitimate reasons to connect (your web browser will not work It will be with one without access to almost a network connection), the other has been done Written by people with suspicion from criminal to criminal
If you want to Protect your Computer, you have to learn to locate Network access and identify the source And intends.
Every attempt on network access is an attack, but if you do not know how to Identify the friend with the enemy, you can leave your door open.
To be able to identify an attack, you need to know what applications and processes are in general
Run-on your computer. Just looking at a graphical interface, whether in Windows or Linux,
Netstat and Host Application Firewall
To be able to identify an attack, you need to know what applications and processes are in general
Run-on your computer. Just looking at a graphical interface, whether in Windows or Linux,
You will not be able to see what is happening under the surface. Netstat and firewall can be used To help you identify which programs should be allowed to connect to the network.
Netstat
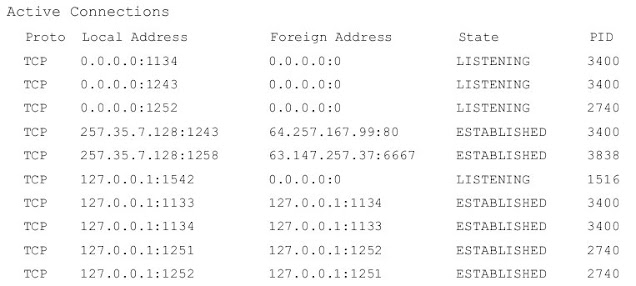
(Netstat section 5.2.3 is also discussed) will display the status of the netstat command Networks Netstat can give you information about what ports are open and IP addresses The protocols that are reaching those are using those ports, the state of the port, and Information about the processor program using the port
At the command prompt, enter:
Now, you have to match the numbers in the PID column with the names of those processes which are
It's going on. In Windows, you should bring up the Windows Task Manager by pressing
CTRL + ALT + DEL (If it does not show a PID column, click View, then select Columns, then select
PID.) In Linux, go to the command prompt and enter ps auxf to display the status of the processor.
In the case of the results of our example listed above,
Netstat
(Netstat section 5.2.3 is also discussed) will display the status of the netstat command Networks Netstat can give you information about what ports are open and IP addresses The protocols that are reaching those are using those ports, the state of the port, and Information about the processor program using the port
At the command prompt, enter:
- netstat-on (for windows) or
- netstat -pn (for Linux)
Now, you have to match the numbers in the PID column with the names of those processes which are
It's going on. In Windows, you should bring up the Windows Task Manager by pressing
CTRL + ALT + DEL (If it does not show a PID column, click View, then select Columns, then select
PID.) In Linux, go to the command prompt and enter ps auxf to display the status of the processor.
In the case of the results of our example listed above,
we find that PID 3400 is related to our web The browser and PID 2740 are from our email client, which we both know to Execute, and both of which are valid reasons for establishing a connection to the Internet.
However, PID 3838 is related to a program called 6r1n.exe, and PID 1516 belongs to one
The program whose name is buscanv.exe, neither of which we are familiar with.
However, just because you do not recognize the name of a program, this does not mean that it There is no reason to run on your system. The next step in this process is for us to Go to an internet search engine and try to figure out what these two programs do.
In our quest, we know that Buscanv.exe is required by our virus scanner and should be It's going on. However, 6r1n.exe may be a trojan. Looking at the performance from Netstat, You can see that the port connected to the 6r1n.exe program is 6667, usually the IRC port Used for remote access by a Trojan. At this point, we start researching remedies, Trojan.
However, PID 3838 is related to a program called 6r1n.exe, and PID 1516 belongs to one
The program whose name is buscanv.exe, neither of which we are familiar with.
However, just because you do not recognize the name of a program, this does not mean that it There is no reason to run on your system. The next step in this process is for us to Go to an internet search engine and try to figure out what these two programs do.
In our quest, we know that Buscanv.exe is required by our virus scanner and should be It's going on. However, 6r1n.exe may be a trojan. Looking at the performance from Netstat, You can see that the port connected to the 6r1n.exe program is 6667, usually the IRC port Used for remote access by a Trojan. At this point, we start researching remedies, Trojan.
Firewall
Now, you can sit on your computer and run the netstat again and again, Keep an eye on the data inside and out of your computer, or you can use one Firewall program for you to do this.
Firewall monitors network traffic on your computer and uses many rules or filters to Determine whether the program should be allowed to access the network or not. Can make a firewall Filter data by IP Address and domain name, Port, and Protocol, or even Transmitted data. This means that you can do such things:
This process is going to be similar to what we do Use to identify programs listed by netstat. A program named iexplorer.exe is obvious Microsoft's Internet Explorer and, if you use it as your web browser, the firewall must allow This is to use the internet. But a program named cbox.exe can be anything. You have not got
Like, but go to your favorite web search engine and see it. (Of course, before You can do this, you have to tell the firewall to allow access to your web browser. Internet.)
The firewall program should also give you the option to allow access to a program Frequently, or just once. Some programs - like your web browser - should be allowed Use the network at any time, but for other programs - such as automatically Check for program updates - You can learn a lot about how your computer works The firewall asks permission every time that the program requests access.
Firewall stand-alone programs (including many free versions for both) are available Windows and Linux) or they are often bundled with anti-virus software. Additionally, Windows XP comes with a built-in firewall, but, as with Windows Internet Explorer, it will be Targeted by people looking for exploitation - flaws can never be found in other firewalls, but there are flaws A Microsoft firewall will be found and exploited.
Packet Sniffers
Netstat will tell you which programs are connected to the network, but it will not show you what These programs are sending data. A packet sniffer, however, gives you the means to record And study the actual data that the programs are sending through the network.
Sniffing
A packet sniffer will record network traffic on your computer so you can see Data tcpdump (and its Windows port, Windpipe) can be considered as the Arctic Packet sniffers, but we are going to use others for our examples because they are graphical The interface is simple, and it allows you to record faster and see a basic capture file.
If you do not already have ethereal, then it can be downloaded from www.ethereal.com. note to
Windows users: To use either on a Windows-based system, you must first download and do Install winpcap packet capture driver. WinPcap is available on the Ethereal download Page or you can go directly to https://www.winpcap.org/ download it.
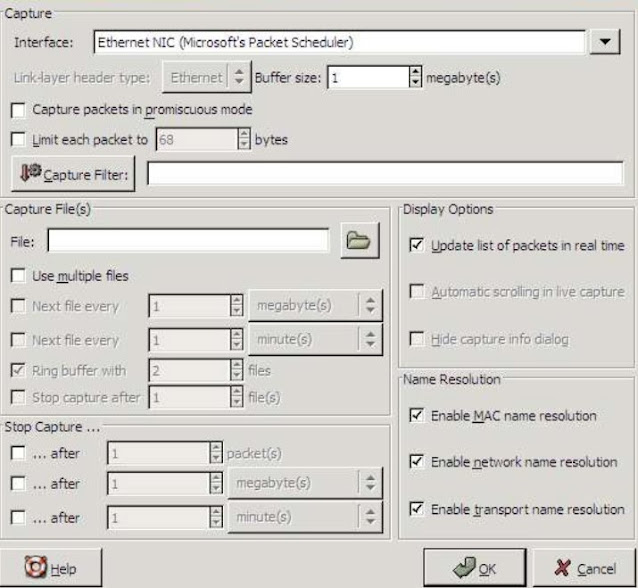
Close all other applications, then start ethereal. Click View in the menu AutoScope in Live Capture Next, click Capture, then start moving on to Capture Options Screen. On the Capture Options screen, make sure that the box "Mark Capture Packet" There are three checkboxes under "Mode Resolution"
Checked, and "Update list of packets in real-time" is marked.
Now, click on the "OK" button.
In principle, now nothing should be done. You will see a window for ether that displays The packets that are held, and, behind it, you will see an ether screen Which displays data in those packets. You can see a small amount of traffic Trying to track each other due to computers on the local network (ARP, NBNS, ICMP) tried to resolve Ethereal's name after DNS activity.
To see the activity, you are going to generate some activity. While ether is running, open your Web browser. Minimize everything except the main ether screen and your web browser, Arrange ether and web browser windows so that you can see both of them alike Time. Now go to a web search engine, such as www.google.com.
As soon as the web page loads, you should see information about scrolling the captured packet Through the ether screen. Choose a search term and enter it in the search bar. Click on Some web pages that are brought by search and see what happens Ether as you do.
Note: If either does not report any network activity, you may have an incorrect network interface
Chose. Go to the Interface drop-down list in the Capture Options screen and select a Different network interface.
Now, you can sit on your computer and run the netstat again and again, Keep an eye on the data inside and out of your computer, or you can use one Firewall program for you to do this.
Firewall monitors network traffic on your computer and uses many rules or filters to Determine whether the program should be allowed to access the network or not. Can make a firewall Filter data by IP Address and domain name, Port, and Protocol, or even Transmitted data. This means that you can do such things:
- Block or allow all data coming from a specific IP address
- Block or allow all data coming from a specific domain
- Turn off or open a specific port
- Block or allow specific protocols
- Block or allow packets that have specific data strings.
- Only allow data from www.ibiblio.com via port 20 or 21
- Allow data from www.google.com which uses the UDP protocol
- Allow data via port 80 only from www.yahoo.com and only when the text string in the packet "I will not waste bandwidth".
This process is going to be similar to what we do Use to identify programs listed by netstat. A program named iexplorer.exe is obvious Microsoft's Internet Explorer and, if you use it as your web browser, the firewall must allow This is to use the internet. But a program named cbox.exe can be anything. You have not got
Like, but go to your favorite web search engine and see it. (Of course, before You can do this, you have to tell the firewall to allow access to your web browser. Internet.)
The firewall program should also give you the option to allow access to a program Frequently, or just once. Some programs - like your web browser - should be allowed Use the network at any time, but for other programs - such as automatically Check for program updates - You can learn a lot about how your computer works The firewall asks permission every time that the program requests access.
Firewall stand-alone programs (including many free versions for both) are available Windows and Linux) or they are often bundled with anti-virus software. Additionally, Windows XP comes with a built-in firewall, but, as with Windows Internet Explorer, it will be Targeted by people looking for exploitation - flaws can never be found in other firewalls, but there are flaws A Microsoft firewall will be found and exploited.
Packet Sniffers
Netstat will tell you which programs are connected to the network, but it will not show you what These programs are sending data. A packet sniffer, however, gives you the means to record And study the actual data that the programs are sending through the network.
Sniffing
A packet sniffer will record network traffic on your computer so you can see Data tcpdump (and its Windows port, Windpipe) can be considered as the Arctic Packet sniffers, but we are going to use others for our examples because they are graphical The interface is simple, and it allows you to record faster and see a basic capture file.
If you do not already have ethereal, then it can be downloaded from www.ethereal.com. note to
Windows users: To use either on a Windows-based system, you must first download and do Install winpcap packet capture driver. WinPcap is available on the Ethereal download Page or you can go directly to https://www.winpcap.org/ download it.
Close all other applications, then start ethereal. Click View in the menu AutoScope in Live Capture Next, click Capture, then start moving on to Capture Options Screen. On the Capture Options screen, make sure that the box "Mark Capture Packet" There are three checkboxes under "Mode Resolution"
Checked, and "Update list of packets in real-time" is marked.
Now, click on the "OK" button.
In principle, now nothing should be done. You will see a window for ether that displays The packets that are held, and, behind it, you will see an ether screen Which displays data in those packets. You can see a small amount of traffic Trying to track each other due to computers on the local network (ARP, NBNS, ICMP) tried to resolve Ethereal's name after DNS activity.
To see the activity, you are going to generate some activity. While ether is running, open your Web browser. Minimize everything except the main ether screen and your web browser, Arrange ether and web browser windows so that you can see both of them alike Time. Now go to a web search engine, such as www.google.com.
As soon as the web page loads, you should see information about scrolling the captured packet Through the ether screen. Choose a search term and enter it in the search bar. Click on Some web pages that are brought by search and see what happens Ether as you do.
Note: If either does not report any network activity, you may have an incorrect network interface
Chose. Go to the Interface drop-down list in the Capture Options screen and select a Different network interface.
Decoding Network Traffic
Now when you can see the network data running through your computer, you have to Find out how to explain it.
In the ether, the first step is to see the summary before ending the summary session Capture the screen that appears while capturing the program.
Now when you can see the network data running through your computer, you have to Find out how to explain it.
In the ether, the first step is to see the summary before ending the summary session Capture the screen that appears while capturing the program.
For our web Browsing session, most packets should have TCP packets (though if you Streaming video has been discontinued, your UDP packet number has increased) However, if you are capturing a simple web browsing session, and you see a large number of ARP or ICMP packet, which can indicate a problem.
After the capture session ends, you are going to see similar outputs:
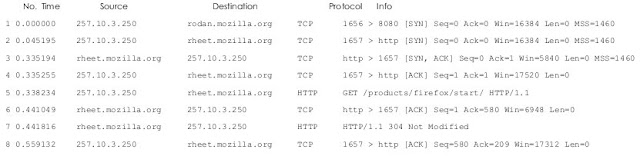
In this example, these twelve packets reflect the activity of the web browser because it connects them.
Its specified start page source and destination have the most easily decoded information The column IP address is 257.10.3.250 local computer; Has other IP addresses Names were solved by ether.
After the capture session ends, you are going to see similar outputs:
In this example, these twelve packets reflect the activity of the web browser because it connects them.
Its specified start page source and destination have the most easily decoded information The column IP address is 257.10.3.250 local computer; Has other IP addresses Names were solved by ether.
Because the use of web browsers as Mozilla Firefox Browser, And since its initial page was the default Mozilla Firefox page, it's not surprising to see it The requests sent to Name.server.com were probably from the Mozilla.org domain When generated by ether, it sends a DNS query to resolve the IP address in names. (pay attention:
This access by ether program was due to the options you set in the performance Option and name resolution box. They were ready to produce in this example More readable output. If you turn off these options, then you will not have this extra Data.)
Looking at source and destination information, you can see unauthorized activity. for, For example, an unfamiliar domain name that is accessed frequently and can indicate that A spyware program is installed.
The next column is the protocol column, which tells you which protocol is used. Then, to know if something is wrong here, then you have to know what to expect. In our web browsing session, we expect TCP and HTTP, and we understand why the DNS Packets are there, but, for example, a large number of ICMP packets may mean that you're The machine is being pinged or traced.
The final column provides more detailed information about information, packets. Packet 2, 3 and
TCP of 4 SYN, SYN / ACK, ACK shows a three-handed handshake, which shows that A The connection has been made. Packet 5 indicates that the HTTP GET command is in packet 7 A 304 modified reaction
If you want more information about packets, then the two pieces below are in ether screen. Show a detailed description. The middle pane shows the details of the packet header. The bottom panel shows a hex and ASCII dump of data in the packet.
Sniffing Other Computers
Some of you are looking for information in this section - and looking at the data can be recorded by ether, think about the possibilities of using packets Sniff the software to record activity on other people's computers. Is this possible?
Yes and No This is called Promise mode and it allows a packet sniffer to monitor the network activity for all computers on a network. This means that you may be able to record the network
Activity on another computer that is in your own network (depending on whether Hardware is installed), but you can not choose any one computer at random and they can smuggle them magically
Data - Two computers must be physically connected, and hardware and software Must be properly configured.
Intrusion Detection Systems
You've probably felt that in order to find unauthorized activity in the actual use of a packet sniffer At that time, you will have to sit on your computer, looking at the packet sniffer output And look forward to seeing any type of pattern. An intrusion detection system performs
This work is for you. This program adds the ability to record network activity with the set rules which allow them to mark unauthorized activity and generate a real-time warning.
Looking at source and destination information, you can see unauthorized activity. for, For example, an unfamiliar domain name that is accessed frequently and can indicate that A spyware program is installed.
The next column is the protocol column, which tells you which protocol is used. Then, to know if something is wrong here, then you have to know what to expect. In our web browsing session, we expect TCP and HTTP, and we understand why the DNS Packets are there, but, for example, a large number of ICMP packets may mean that you're The machine is being pinged or traced.
The final column provides more detailed information about information, packets. Packet 2, 3 and
TCP of 4 SYN, SYN / ACK, ACK shows a three-handed handshake, which shows that A The connection has been made. Packet 5 indicates that the HTTP GET command is in packet 7 A 304 modified reaction
If you want more information about packets, then the two pieces below are in ether screen. Show a detailed description. The middle pane shows the details of the packet header. The bottom panel shows a hex and ASCII dump of data in the packet.
Sniffing Other Computers
Some of you are looking for information in this section - and looking at the data can be recorded by ether, think about the possibilities of using packets Sniff the software to record activity on other people's computers. Is this possible?
Yes and No This is called Promise mode and it allows a packet sniffer to monitor the network activity for all computers on a network. This means that you may be able to record the network
Activity on another computer that is in your own network (depending on whether Hardware is installed), but you can not choose any one computer at random and they can smuggle them magically
Data - Two computers must be physically connected, and hardware and software Must be properly configured.
Intrusion Detection Systems
You've probably felt that in order to find unauthorized activity in the actual use of a packet sniffer At that time, you will have to sit on your computer, looking at the packet sniffer output And look forward to seeing any type of pattern. An intrusion detection system performs
This work is for you. This program adds the ability to record network activity with the set rules which allow them to mark unauthorized activity and generate a real-time warning.
Honeypots and Honeynets
People who like to see monkeys go to the zoo because there can be monkeys. Those who like to see birds, they feed the birds, and the birds come to them. Those people Make fish aquariums and choose fishes. But what do you do Want to see hackers?
You excluded a honeypot.
Think like this - you are a bear. You do not know a lot (being a bear) but you do Know that honey is delicious, and there is nothing better than a big hot day The handful of honey So you see a large pot filled with honey, which is sitting in the center of a clearing, and You are thinking, 'Yum!' But once you stick your claw into a honey vessel, you take the risk of trapping.
if Nothing else, you are leaving big, sticky claw prints everywhere, and everyone is going To know that someone has been in honey, and this is a good chance that anyone who After the large, sticky claw print shows it is you. There is more than one bear Tasty honey was trapped due to their affection.
A honeypot is a computer system, network, or virtual machine that does not have any other purpose
Compared to woo hackers. In a honeypot, there are no authorized users - no actual data is stored
No actual work is done on this system -
People who like to see monkeys go to the zoo because there can be monkeys. Those who like to see birds, they feed the birds, and the birds come to them. Those people Make fish aquariums and choose fishes. But what do you do Want to see hackers?
You excluded a honeypot.
Think like this - you are a bear. You do not know a lot (being a bear) but you do Know that honey is delicious, and there is nothing better than a big hot day The handful of honey So you see a large pot filled with honey, which is sitting in the center of a clearing, and You are thinking, 'Yum!' But once you stick your claw into a honey vessel, you take the risk of trapping.
if Nothing else, you are leaving big, sticky claw prints everywhere, and everyone is going To know that someone has been in honey, and this is a good chance that anyone who After the large, sticky claw print shows it is you. There is more than one bear Tasty honey was trapped due to their affection.
A honeypot is a computer system, network, or virtual machine that does not have any other purpose
Compared to woo hackers. In a honeypot, there are no authorized users - no actual data is stored
No actual work is done on this system -
Therefore, every access, every attempt to use it, maybe Is recognized as unofficial. Instead of going through the log to identify intrusion, the system The administrator knows that each access is an intrusion, so there is already a large part of the work
done.
Types of Honeypots
Honeypots are of two types: production and research. Production honeypots are mainly used as warning systems. A production identifies the honeypot Generates an intrusion and an alarm They can show you that an intruder has identified a System or network as the object of interest, but not much.
done.
Types of Honeypots
Honeypots are of two types: production and research. Production honeypots are mainly used as warning systems. A production identifies the honeypot Generates an intrusion and an alarm They can show you that an intruder has identified a System or network as the object of interest, but not much.
For example, if you wanted to know that if the bears lived near your clearing, then you can keep ten small utensils of honey. if you check them in the morning and found one or more of them empty, you will know This bear was in the vicinity, but you will not know anything about the bear.
Research Honeypots are used to collect information about hacker activities. a research Honeypot lies in hackers, then puts them in their possession while it quietly records their actions.
Research Honeypots are used to collect information about hacker activities. a research Honeypot lies in hackers, then puts them in their possession while it quietly records their actions.
For example, if - instead of simply documenting their presence - you wanted to study the bear So you can set a big, delicious, sticky pot of honey in the middle of your clearing, but Then you will surround that pot with a movie camera, still camera, tape recorder and Research assistant with a clipboard and pith helmets.
The two types of honeypots mainly differ in their complexity. You can set up more easily Maintain production hinge due to its simplicity and limited quantity The information that you want to collect. In a production honeypot, you just want to know You've been killed; You do not care so much whether or not hackers live around, however, in A Research Honeypot, you want hackers to remain so that you can see what they are doing.
This makes finding a research honeypot more difficult to maintain because you must make the system a real, functional system that provides files or services to hackers it looks interesting. A bear who knows what a honeypot looks like, it may take a minute In an empty vessel, but only a full pot filled with delicious honey is going to hang the bear You've been studying it for a long time.
Building a Honeypot
In the most basic sense, a honeypot is nothing more than a computer system that has been installed
With the hope that it will be compromised by intruders. Essentially, it means that if you connect a computer to an insecure operating system from the Internet, then let it sit there, Waiting for the agreement, you made a honeypot!
But this is not a very useful honeypot. It's like leaving your honey out in the clearing, then Going home in town When you come back, honey will go away, but you will not know Anything about who, how, when or why? You do not learn anything from your honeypot, useless You have a way to gather information about it. To be useful, even the most basic Most of the honeypot intrusion detection systems are some kind of.
Intrusion detection systems can be as simple as a firewall. Generally, a firewall is used to prevent unauthorized users from accessing computer systems, but they also log everything Which passes or stops. Can provide a review of the logs produced by the firewall Basic information about attempts to reach Honeypot
Add more complex Honeypot hardware, such as switch, router, or hub Monitor or control network access They can also use packet sniffers to collect additional information about network traffic.
Research Honeypots can also run programs that simulate normal usage, from which it appears Honeypot is actually being accessed by authorized users, and teasing potential intruders With incorrect email, password, and data. These types of programs can also be used To hide the Operating System, it appears, for example, that is a Linux-based computer Windows is running.
But talk about honey - it's sticky, and there's always a chance that your honeypot is Bees turned into nests. And when the bees come home, you do not want to be one Your hands got trapped in honey. An improperly configured honeypot can easily change In a launching pad for additional attacks
The two types of honeypots mainly differ in their complexity. You can set up more easily Maintain production hinge due to its simplicity and limited quantity The information that you want to collect. In a production honeypot, you just want to know You've been killed; You do not care so much whether or not hackers live around, however, in A Research Honeypot, you want hackers to remain so that you can see what they are doing.
This makes finding a research honeypot more difficult to maintain because you must make the system a real, functional system that provides files or services to hackers it looks interesting. A bear who knows what a honeypot looks like, it may take a minute In an empty vessel, but only a full pot filled with delicious honey is going to hang the bear You've been studying it for a long time.
Building a Honeypot
In the most basic sense, a honeypot is nothing more than a computer system that has been installed
With the hope that it will be compromised by intruders. Essentially, it means that if you connect a computer to an insecure operating system from the Internet, then let it sit there, Waiting for the agreement, you made a honeypot!
But this is not a very useful honeypot. It's like leaving your honey out in the clearing, then Going home in town When you come back, honey will go away, but you will not know Anything about who, how, when or why? You do not learn anything from your honeypot, useless You have a way to gather information about it. To be useful, even the most basic Most of the honeypot intrusion detection systems are some kind of.
Intrusion detection systems can be as simple as a firewall. Generally, a firewall is used to prevent unauthorized users from accessing computer systems, but they also log everything Which passes or stops. Can provide a review of the logs produced by the firewall Basic information about attempts to reach Honeypot
Add more complex Honeypot hardware, such as switch, router, or hub Monitor or control network access They can also use packet sniffers to collect additional information about network traffic.
Research Honeypots can also run programs that simulate normal usage, from which it appears Honeypot is actually being accessed by authorized users, and teasing potential intruders With incorrect email, password, and data. These types of programs can also be used To hide the Operating System, it appears, for example, that is a Linux-based computer Windows is running.
But talk about honey - it's sticky, and there's always a chance that your honeypot is Bees turned into nests. And when the bees come home, you do not want to be one Your hands got trapped in honey. An improperly configured honeypot can easily change In a launching pad for additional attacks
If a hacker compromises your honeypot, then Immediately attacks a large corporation or uses it to distribute its honeypot Flood of Spam is a good opportunity that you will be identified as a response. Correctly configured honeypots control network traffic from the inside and out of the computer.
A Simple production honeypot can allow incoming traffic through the firewall, but stop everyone Outbound traffic This is a simple, effective solution, but intruders will quickly realize that
A real, working computer system A little more complex honeypot can allow something Outgoing traffic, but not all.
Research Honeypots - Those intruders who want to stay as long as possible - Occasionally uses Mailers, who audit outgoing traffic and abort potentially hazardous data By modifying it so that it is ineffective.
A real, working computer system A little more complex honeypot can allow something Outgoing traffic, but not all.
Research Honeypots - Those intruders who want to stay as long as possible - Occasionally uses Mailers, who audit outgoing traffic and abort potentially hazardous data By modifying it so that it is ineffective.


.png)















No comments:
Post a Comment