What is Password Cracking?
Password is a system designed to provide authentication. There are many different ways Authenticate users of a system: A user can present a physical object like a key card, can prove identity Using a personal feature like a fingerprint, or using something that only the user knows.Unlike the other approaches listed, the primary advantage of user authentication via password is that it can be easily changed in the event that your password becomes compromised.
This article will discuss What the Password Cracking is, the attacker has the password cracking technique The user name and password pair, the ability to try to log in to the system using techniques When an attacker has access to passwords on the system, attacks are involved See password entry in some way and finally graphical password and graphical password Cracks work.
 |
| Figure 1: The flow of password attacking possibilities. |
Password A spammer can use dictionary attacks to gain access to bank accounts or other
Also, Web Services Wireless protocols are unsafe for some crack cracking techniques Packet sniffers are capable of receiving initialization packets.
How Passwords are Stored
To understand how to compromise a password, firstly it is necessary to understand how Passwords are stored on specific systems. Clearly store user names and related passwords Text is an unacceptable solution. Attempting to hide stored passwords in clear form (such as inserting Password is deep in a deep directory hierarchy) "through security" Ambiguity "which would also be unacceptable. Unix system of file management provides a Better solution though: one of the permissions Initial version of Multics (precursor of Unix) Store the password file in clear text, but can only be viewed with superuser permissions. This solution The bug also failed when the bug cleared some temporary files and password file (in the clear text) The login was printed for each user.Unix, instead, stores the password's password for the hashed value in the password file instead of the real Password. Then when a user inputs his password, the system can simply take a hash Compare the input and the stored hash value to it. To know how the password file is stored, let's Look at the Unix password file scheme.
Unix Password File
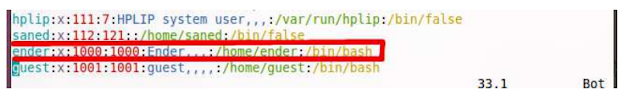
Most UNIX-based file systems are located on the password file / etc / passwd [8]. Each line in The file has account information on the system. The file is readable by all users But with the superuser privileges only the writeable. Each entry in this password file has seven fields, such as So:
The first field, "ender", is the account or username. The second area has the letter 'x' Explained below. The third area user number is an integer identifier for the user. The fourth The field is the group identifier, which shows the primary group of this user. The fifth area is a comma Information about different price lists, user's full name and contact, known as Geckos Field Information. In this particular situation, most areas are vacant in the Geckos area. The sixth area The home directory for the user is. The last field is a program that should be executed when User logs in the system; In this situation, the use of the shell is done when Ander logs in.
Second field for entries in the password file in initial versions of UNIX (letter x) Contains a one-way hash value for each account's password. They have been transferred over time A shadow file (located in / / / shadow), read only by people with super privilege this Provides an additional layer of protection.
Windows Password File
The Windows system is similar to the Unix Strategy to store the file. Password The file for Windows, which is known as Security Account Manager (SAM) file, is located in
C:\Windows\System32\config\Sam
There are seven large defunct areas in an entry in the SAM file: username, user number, The encrypted password, hashed password, full name of hashed password, under the different algorithm
Users, and finally home directories. Unlike the Unix password file, Windows is a SAM file The operating system is not readable after it is booted. Unix requires password file to remain Readable for all users so that some programs can access information. Because of this, in order To read the SAM file, before the system boots it Access is necessary. Optionally, People have installed secondary operating systems to read the SAM file from there.
Online Password Storage
For many websites and online services, users have to log in with a specific password plan. this Password information storage is required. However, online services generally store passwords
For their systems in a non-standardized way, and these systems are not always designed by engineers With a background in privacy or security, For example, Sony had a security breach in which it was
It is learned that the passwords were being stored in a SQL database in cleartext. Cracking password Such a system involves only accessing the password storage system.
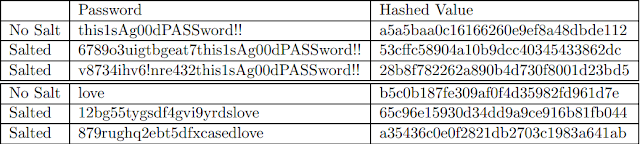
Password Salts
Archiving hashed or encrypted values for the password is definitely more secure than storage Their plain text in the password file, but there can be a general additional security measure Keep practicing. Adding extra randomity to passwords and this is known in this strategy A password or cryptographic salt When a password is created, the system will add some type Randomness for a password. This random name (or salt) password should be different each time Made from Because of this, the same password will be stored as a separate hash Machines or separate accounts on the same machine.
Figure 3 shows the effect of password salts on a strong password and a weak password. Without it, Password salts, even a strong password, will have for the same value.
This is a vulnerability The event that receives access to an attacker shadow file. An attacker can simply store Some common passwords are 'md5 hashed values and are then able to check whether a password is a Which hash match system Pickling makes this kind of attack more difficult; The password is randomized because the entropy causes a large amount of the shed value, even for Weak password.
Brute force viability depends on the password and the domain of the input characters
Password length.
Brute Force Attacks
Brute force viability depends on the password and the domain of the input characters
Password length.
Length and character set, as well as how long it will take to crack that type of password
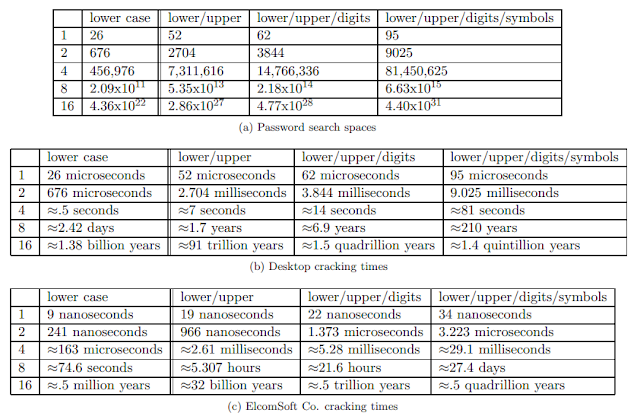
One desktop computer could try one million passwords per second while trying to use force A password. Figure 4B shows how much time will take for the worst position for each input domain
And password length. ElcomSoft Co. Claims ability to test 2.8 billion passwords per second Using a High-end Graphics Processor on a Machine Figure 4c shows how long it will take To do the same thing with the powerful graphics card and cutting edge technology.
Brute Force Password cracking does not work for long enough passwords. In addition, passwords Are really random Many passwords will be English words, probably with the first The letter was enlarged and a score was added or made [9]. Search location for common or fair Password length is too short for password 8 or less, from 2.18x1014 (even for password Upper case, lower case, and available points).
More than fifty percent of passwords in the data leaked from Sony was less than eight The letters long [4]. In addition, only four percent of passwords actually had a lower case, upper case
There are a non-alphanumeric character in digits and only one percent leak passwords. The most common roaming passwords were Seinfeld, password, 123456, abc123 and purple. Create a dictionary that usually involves entering a password, which will help the attacker Estimate accurate password more often than brute force. For example, a publicly available dictionary More than 35 percent of the leaked passwords match.
An attacker who accesses a password or shadow file cannot actually be required to try All passwords in common password (list) An attacker may be preceded Match the hash value of each of those passwords and then submit them to the assessed values Password file
This pre-infection may possibly have a very serious risk for password protection. However, As mentioned above, many systems implement the salt value which adds randomity to the password
That machine. Now if an attacker wants to stop the hash of common passwords, then he or He will actually need to precompute those hash for each password together with each possible possible
Salt. If salt is sufficiently large, it can also be an important preventative for the attacker Relatively few passwords
The idea of time-memory trade-off in computer science is very common. The principle is straightforward: precomputer part of the problem (usually by solving subproblem or By finding a common solution), while the usual time costing of problem-solving is reduced Space requirements are quite less than necessary to precompute Solution. This section explains how a similar approach can be implemented for password problems. Cracking, beginning with an innovation that has been described for decades, has contributed to describing incremental improvements from which rainbow tables have evolved.
Where hash has been precomputed for every candidate's password, it is important in Helm's algorithm Purely reduces search costs compared to brute force attacks. Introduced the main innovation
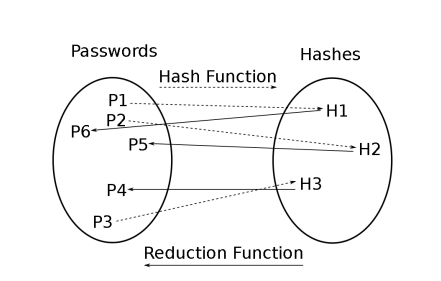
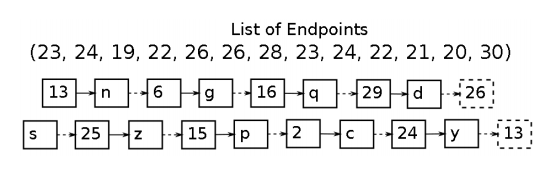
The Hellman has the idea of using a decrease function which maps the hash back to the main location To produce hash and keys (The relationship between these works is illustrated Figure 7). The complete table is created by creating a series of rows (two rows are constructed Pictured in Figure 6a). Each line starts with some random value (in this case n), which is hashed (Value 0 production here). The hash of the initial value is reduced (in this case the production Value a), and these operations are repeatedly stacked together in such a way until they are queued Finished with the desired length, some final hash value (24 in this case).
Note that after calculating the table (detailed below), only required for planned attackStart and end point for each series, which means that all intermediate points may occur during pre-mediation Leave them when used.
To attack the hash value, hash and cut functions have been chained once again Together; However, to see if it is in the list, each hash value should be checked The line end point of table (see figure 8). In this case, being attacked is 13, and after many The decrease and itching of hashing, hash value 26 is calculated, which is one of the ends of the table Points. The corresponding starting point (which is the figure) of this last point is seen, and
The row of the table is exposed to the value of the endpoint (26 inches) (just like before) This example) or target hash (13 in this example) is produced. In this case, many iterations Hashing and depletion produce a value of 13, and by checking the value immediately This, the attacker can determine that the user's password (or least collision) is y. Was The value of the last point has reached the target hash value, the attacker will continue
The creation of the original series (starting with the 13) until another final point was not produced.
Hellman's paper size uses tables of N2 / 3 (Where N is the size of the search space for the password) As a value that creates a table that will reduce the number of keys that remember the table
Completely, still giving a laudable increase in the pace of calculation. Although this A significant improvement, it is still insufficient when all but the weakest passwords have been attacked: From table 4c to 16-character lowercase-only password can be cracked in approximately 123 hours (using) The same value of 2.8 billion passwords per second from the same table), but a password of the same Using both numbers upper and lowercase as well as numbers and symbols, the length will still be taken In more than three hundred years, and even in a seriously reduced size, the lookup table will be About thirty petabytes are required. Clearly, this approach requires further improvement. If we plan to use it successfully.
The Innovation Rainbow Tables offer is the use of a series compared to the previous approach. Cut functions (unlike a series of tables, each generated with a single reduction function). When the chains are produced (as of figure 6a), then the position in the series determines which The reduced function is applied to each hash, before applying the same decrease function In every situation.
This provides a significant advantage in terms of pre-computation time: if there is a collision Degree of merged series occurs only when the collision occurs in the same position within the series
(Because otherwise the next deficiency function will be different and the possibility of the chain will be different Re-split). While a Rainbow Table series can have a series of repetitive values,
The probability of this event is incredibly low, as it is likely that two chains will do There is a series of similar values for any admirable length.
Rainbow Tables to Crack the hash stored in the Windows Security Account Manager (SAM) file? This comprehensive risk is responsible for the large portion of the LAN Manager (LM) hash system Used in earlier versions of Windows.
Usage
The only password to be used on the Windows system until the launch of LM hash is the hashing protocol Windows NT; However, in the later versions of the introduction of new hash schemes
Windows, continue to be stored by default (for back compatibility) until it is released Windows Vista (That's why, as mentioned in Section 2.2, the SAM file contains many hashes Each password). Unless a sufficiently long password is used or this behavior is discontinued, Windows XP installation still stores this hash in the SAM file.
Weaknesses
There are many weird behaviors in the implementation of LM hash that offer it more Weak for attack; One of the most important facts is that the hash is not salty. This means that the same password will always produce the same hash on any Windows installation,
Which allows for the wider availability of devices that use Rainbow Tables to crack Password. In addition, however, the protocol divides the password into parts and hashes to everyone
separately; It allows to attack in parallel, in addition to minimizing the hash. Search location for an attacker (for reference, while working with a 16-character password, this (It is more than twenty-seven years for only twenty-seven days). The hash converts all the letters into uppercase before hashing the password, which,
It is less important than the fact that it has separately, still reduces to a great extent Search location (from 246 to 243 for a 24-letter ASCII password)
Avoidance
The LM scheme cannot produce any hash for a password longer than fourteen characters; Most ordinary The way to avoid using it (in recent versions of Windows) is to use a password that is long
After that, it is This is due to the fact that the two parts of the password are used as each des key Which encrypts a plain text; This 7-character ASCII password has been explained by
Place of 56-bit key Additionally, when dealing with a system in which users can not "reasonably" The length of the password can be expected to be used, versions of Windows that default to store
LM hash can disable this behavior for back-compatibility.
Physical Attacks
Password search is obviously possible on account, although direct attacks like brutal force, Dictionary or rainbow table. However, these are far from trivial to implement and are Critical TimeLine Business Concerns Cracking passwords may be better in some situations Through less traditional means The most basic way of physical methods will be physically Forcing someone to give their password for a very important account. This type of literal attack is Generally known as "rubber tube cryptography" and it is only effective when an attacker can do A very inquisitive person is able to gain physical access to the person who knows about the password.
If there are ethical or logical issues with this kind of attack, then there are less aggressive ways to get Password also A side-channel attack is the one that collects information from the leak Arrange somehow The most basic form of this would be that someone should observe their typing Password (maybe with a well-placed camera) There is no need to see this with a strategy Worried about password files, salt values, or make a series of hashes; Must be enabled only To see the terminal in which a person enters the password.
The side-channel attack will have to recreate a more sophisticated password It sounds like typing on a keyboard generates. Especially on the old keyboard, each input key When pressed produces a slightly different sound. Berkeley researchers have used extremely sensitive microphones to understand that which key is pressed on the keyboard Voice. It is also not necessary to supply training data for the program (which is the data Notifies the system, which seems to match which key). The system is able to listen Ten minutes of normal keyboard input (such as writing a paper for a class) and rebuilds represent the sounds that represent the key using standard machine understanding and validation.
Technique.
In light of the multitude of techniques available for cracking the password, it should be clear that There is no specific "best" option. The most useful password cracking technique will be highly
Depends on the characteristics of the attacker and the target.
In addition, graphical passwords It is difficult to attack in most of the traditional senses. The automatic effort is difficult to enter Graphical password system, even if the search space is too small with a typical text password. However, a powerful security hole has been found in the Android graphical password scheme. Many users leave behind visible oil remnants by logging into their graphical password multiple times In the system, A stolen phone could possibly be broken by looking at the screen Spots
There is no cost, However, the technique of creating a password-storage scheme that will face any computational attack (within a reasonable time frame) exists for decades.
The generality of attacks The passwords are almost entirely responsible for the combination of idleness (or ignorance) against the hash On behalf of those who design and administer passwords and lazy systems (or) Ignorance) from those people who use these systems Only Salted as You Store The hash of password has reduced the effectiveness of most computational attacks to that point where They are almost useless, drawn from a search location as large as the use of big passwords It is possible (i.e. eligible to be eligible from a large set) significantly reduces the effectiveness Along with these attacks Also, keep in mind while entering a password (i.e. not writing This is on a post-it on your monitor and checking for anyone who can stand on your shoulder
As you enter it) is enough to stop everyone but will be most dedicated - physical attacker (and This type of attack greatly reduces the chances of being financially viable for the attacker).
Related:
One desktop computer could try one million passwords per second while trying to use force A password. Figure 4B shows how much time will take for the worst position for each input domain
And password length. ElcomSoft Co. Claims ability to test 2.8 billion passwords per second Using a High-end Graphics Processor on a Machine Figure 4c shows how long it will take To do the same thing with the powerful graphics card and cutting edge technology.
Dictionary Attacks
Brute Force Password cracking does not work for long enough passwords. In addition, passwords Are really random Many passwords will be English words, probably with the first The letter was enlarged and a score was added or made [9]. Search location for common or fair Password length is too short for password 8 or less, from 2.18x1014 (even for password Upper case, lower case, and available points).
More than fifty percent of passwords in the data leaked from Sony was less than eight The letters long [4]. In addition, only four percent of passwords actually had a lower case, upper case
There are a non-alphanumeric character in digits and only one percent leak passwords. The most common roaming passwords were Seinfeld, password, 123456, abc123 and purple. Create a dictionary that usually involves entering a password, which will help the attacker Estimate accurate password more often than brute force. For example, a publicly available dictionary More than 35 percent of the leaked passwords match.
An attacker who accesses a password or shadow file cannot actually be required to try All passwords in common password (list) An attacker may be preceded Match the hash value of each of those passwords and then submit them to the assessed values Password file
This pre-infection may possibly have a very serious risk for password protection. However, As mentioned above, many systems implement the salt value which adds randomity to the password
That machine. Now if an attacker wants to stop the hash of common passwords, then he or He will actually need to precompute those hash for each password together with each possible possible
Salt. If salt is sufficiently large, it can also be an important preventative for the attacker Relatively few passwords
Rainbow Tables
The idea of time-memory trade-off in computer science is very common. The principle is straightforward: precomputer part of the problem (usually by solving subproblem or By finding a common solution), while the usual time costing of problem-solving is reduced Space requirements are quite less than necessary to precompute Solution. This section explains how a similar approach can be implemented for password problems. Cracking, beginning with an innovation that has been described for decades, has contributed to describing incremental improvements from which rainbow tables have evolved.
A Time-Memory Trade-Of
The idea of applying time-memory trade-off to the problem of cryptanalysis was proposed for the first time In 1980 by Martin Hellman Although their approach attacks the encrypted ciphertext using Data Encryption Standard (DES), instead of attacking the password, only minor modifications are required. Hashing Plan. Looking at the small one prefabricated table compared to being employed in an attackWhere hash has been precomputed for every candidate's password, it is important in Helm's algorithm Purely reduces search costs compared to brute force attacks. Introduced the main innovation
The Hellman has the idea of using a decrease function which maps the hash back to the main location To produce hash and keys (The relationship between these works is illustrated Figure 7). The complete table is created by creating a series of rows (two rows are constructed Pictured in Figure 6a). Each line starts with some random value (in this case n), which is hashed (Value 0 production here). The hash of the initial value is reduced (in this case the production Value a), and these operations are repeatedly stacked together in such a way until they are queued Finished with the desired length, some final hash value (24 in this case).
Note that after calculating the table (detailed below), only required for planned attackStart and end point for each series, which means that all intermediate points may occur during pre-mediation Leave them when used.
To attack the hash value, hash and cut functions have been chained once again Together; However, to see if it is in the list, each hash value should be checked The line end point of table (see figure 8). In this case, being attacked is 13, and after many The decrease and itching of hashing, hash value 26 is calculated, which is one of the ends of the table Points. The corresponding starting point (which is the figure) of this last point is seen, and
The row of the table is exposed to the value of the endpoint (26 inches) (just like before) This example) or target hash (13 in this example) is produced. In this case, many iterations Hashing and depletion produce a value of 13, and by checking the value immediately This, the attacker can determine that the user's password (or least collision) is y. Was The value of the last point has reached the target hash value, the attacker will continue
The creation of the original series (starting with the 13) until another final point was not produced.
Hellman's paper size uses tables of N2 / 3 (Where N is the size of the search space for the password) As a value that creates a table that will reduce the number of keys that remember the table
Completely, still giving a laudable increase in the pace of calculation. Although this A significant improvement, it is still insufficient when all but the weakest passwords have been attacked: From table 4c to 16-character lowercase-only password can be cracked in approximately 123 hours (using) The same value of 2.8 billion passwords per second from the same table), but a password of the same Using both numbers upper and lowercase as well as numbers and symbols, the length will still be taken In more than three hundred years, and even in a seriously reduced size, the lookup table will be About thirty petabytes are required. Clearly, this approach requires further improvement. If we plan to use it successfully.
Further Improvement
The Innovation Rainbow Tables offer is the use of a series compared to the previous approach. Cut functions (unlike a series of tables, each generated with a single reduction function). When the chains are produced (as of figure 6a), then the position in the series determines which The reduced function is applied to each hash, before applying the same decrease function In every situation.
This provides a significant advantage in terms of pre-computation time: if there is a collision Degree of merged series occurs only when the collision occurs in the same position within the series
(Because otherwise the next deficiency function will be different and the possibility of the chain will be different Re-split). While a Rainbow Table series can have a series of repetitive values,
The probability of this event is incredibly low, as it is likely that two chains will do There is a series of similar values for any admirable length.
LanManager Hashes
An important point about Rainbow Tables is that despite their very good speed Compared to previous such attacks, they are still ineffective with the inclusion of one Salt in password hashing scheme Then, there are many widely available tools that useRainbow Tables to Crack the hash stored in the Windows Security Account Manager (SAM) file? This comprehensive risk is responsible for the large portion of the LAN Manager (LM) hash system Used in earlier versions of Windows.
Usage
The only password to be used on the Windows system until the launch of LM hash is the hashing protocol Windows NT; However, in the later versions of the introduction of new hash schemes
Windows, continue to be stored by default (for back compatibility) until it is released Windows Vista (That's why, as mentioned in Section 2.2, the SAM file contains many hashes Each password). Unless a sufficiently long password is used or this behavior is discontinued, Windows XP installation still stores this hash in the SAM file.
Weaknesses
There are many weird behaviors in the implementation of LM hash that offer it more Weak for attack; One of the most important facts is that the hash is not salty. This means that the same password will always produce the same hash on any Windows installation,
Which allows for the wider availability of devices that use Rainbow Tables to crack Password. In addition, however, the protocol divides the password into parts and hashes to everyone
separately; It allows to attack in parallel, in addition to minimizing the hash. Search location for an attacker (for reference, while working with a 16-character password, this (It is more than twenty-seven years for only twenty-seven days). The hash converts all the letters into uppercase before hashing the password, which,
It is less important than the fact that it has separately, still reduces to a great extent Search location (from 246 to 243 for a 24-letter ASCII password)
Avoidance
The LM scheme cannot produce any hash for a password longer than fourteen characters; Most ordinary The way to avoid using it (in recent versions of Windows) is to use a password that is long
After that, it is This is due to the fact that the two parts of the password are used as each des key Which encrypts a plain text; This 7-character ASCII password has been explained by
Place of 56-bit key Additionally, when dealing with a system in which users can not "reasonably" The length of the password can be expected to be used, versions of Windows that default to store
LM hash can disable this behavior for back-compatibility.
Physical Attacks
Password search is obviously possible on account, although direct attacks like brutal force, Dictionary or rainbow table. However, these are far from trivial to implement and are Critical TimeLine Business Concerns Cracking passwords may be better in some situations Through less traditional means The most basic way of physical methods will be physically Forcing someone to give their password for a very important account. This type of literal attack is Generally known as "rubber tube cryptography" and it is only effective when an attacker can do A very inquisitive person is able to gain physical access to the person who knows about the password.
If there are ethical or logical issues with this kind of attack, then there are less aggressive ways to get Password also A side-channel attack is the one that collects information from the leak Arrange somehow The most basic form of this would be that someone should observe their typing Password (maybe with a well-placed camera) There is no need to see this with a strategy Worried about password files, salt values, or make a series of hashes; Must be enabled only To see the terminal in which a person enters the password.
The side-channel attack will have to recreate a more sophisticated password It sounds like typing on a keyboard generates. Especially on the old keyboard, each input key When pressed produces a slightly different sound. Berkeley researchers have used extremely sensitive microphones to understand that which key is pressed on the keyboard Voice. It is also not necessary to supply training data for the program (which is the data Notifies the system, which seems to match which key). The system is able to listen Ten minutes of normal keyboard input (such as writing a paper for a class) and rebuilds represent the sounds that represent the key using standard machine understanding and validation.
Technique.
In light of the multitude of techniques available for cracking the password, it should be clear that There is no specific "best" option. The most useful password cracking technique will be highly
Depends on the characteristics of the attacker and the target.
Graphical Passwords
The arrival of touch screen devices has brought about a new way of authentication Usually, Android phones are now seen on devices. These tools provide users choice Certifying using the graphical password, Default android program The user needs to create a password that connects at least four points in any order (though
The user can create a longer password by connecting more dots). An advantage of graphical password In this way, humans are usually better at remembering patterns and pictures Attempt to memorize a long string of random characters. In addition, graphical passwords It is difficult to attack in most of the traditional senses. The automatic effort is difficult to enter Graphical password system, even if the search space is too small with a typical text password. However, a powerful security hole has been found in the Android graphical password scheme. Many users leave behind visible oil remnants by logging into their graphical password multiple times In the system, A stolen phone could possibly be broken by looking at the screen Spots
Conclusion
In the preceding sections, we have discussed various aspects of password-based authentication, including its origins, general implementation, and various attacks with it.There is no cost, However, the technique of creating a password-storage scheme that will face any computational attack (within a reasonable time frame) exists for decades.
The generality of attacks The passwords are almost entirely responsible for the combination of idleness (or ignorance) against the hash On behalf of those who design and administer passwords and lazy systems (or) Ignorance) from those people who use these systems Only Salted as You Store The hash of password has reduced the effectiveness of most computational attacks to that point where They are almost useless, drawn from a search location as large as the use of big passwords It is possible (i.e. eligible to be eligible from a large set) significantly reduces the effectiveness Along with these attacks Also, keep in mind while entering a password (i.e. not writing This is on a post-it on your monitor and checking for anyone who can stand on your shoulder
As you enter it) is enough to stop everyone but will be most dedicated - physical attacker (and This type of attack greatly reduces the chances of being financially viable for the attacker).
Related:
- Types of Cyber Attack?
- What is the Dark Web? How to Access the Dark Web?
- Most Common Security Vulnerability
- Hacking with Android - Become a True Android Hacker


.png)
















You should get a 100% Satisfaction Guarantee from the organization you select to make your logo. Along these lines, they will take a shot at your plan until you feel totally fulfilled.logo design service
ReplyDelete