What is Web Services Hacking and Hardening
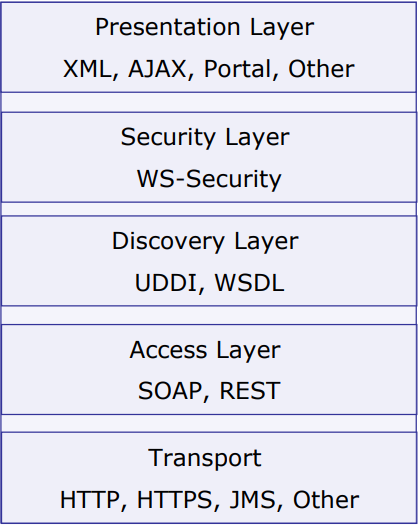
Web Service Stack
Web Service supplier or Server-Side
Web Services client or Client-Side
 |
| Add caption |
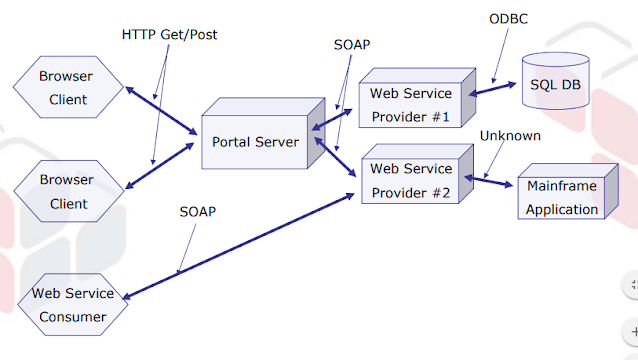
Common Net Services Usage
Web Service Threats
Transport Threats
Sniffing and Snooping
- Message confidentiality considerations
- SOAP messages will contain long-winded directions on their desired routing. If one node during this routing the path is compromised multiple threats are often complete.
- Message integrity considerations and potential Denial of Service by taking an accurate message with valid certification and causing it 1000+ times
- a standard threat in relevance network Denial of Service
Almost all products use an equivalent parser, thus if a vulnerability exists during a single product leverage MS computer program then all others have an equivalent threat.
The XML specification itself doesn't place any restrictions on the structure itself and rather is a receptive interpretation by the creator of the computer program. Example: Some parsers can stop reading associate XML Attribute price once they reach some range of characters and
others can continue.
The following are going to be discussed:
- Buffer, Heap, number Overflows
- XML computer programme Attacks
Warning: Through a winning buffer overflow a malicious
the command could also be dead on your system.
We see these all the time! Through passing a malicious buffer to an online Server or Application server the offender will produce an associate overflow condition wherever a segmentation fault happens.
- This oversized/malicious buffer is often sent as a part of the transport header OR as a part of the SOAP message.
- Associate expected number price is often overflowed by surpassing the value allowed inflicting a segmentation fault.
XML Parser Attack Threats
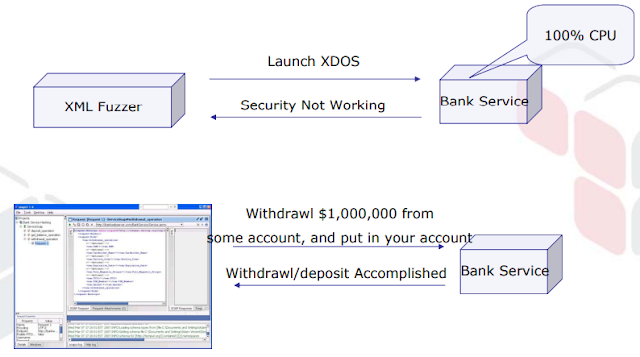
The following threats may result during a denial of service usually referred to as XML Denial of Service (XDOS) by intense 100% of the processing power on the system doing the parsing.
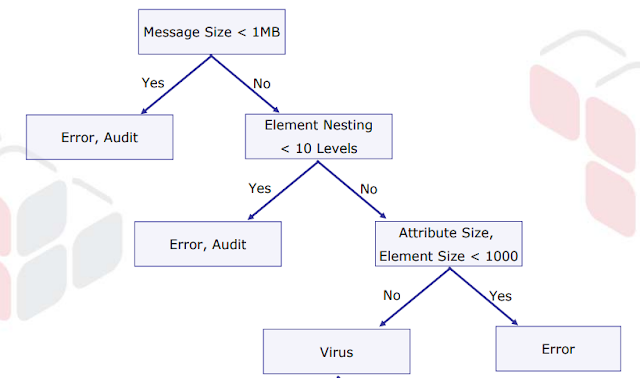
Complex or Recursive Payload
- Again, the XML specification and structure has no limits!
- Machine-controlled applications area unit is accessible that produce hirsute information for XDOS attacks.
- several parsing technologies load entire documents into memory
- net Services were usually NOT designed around massive message sizes.
- distinctive attacks are going to be found wherever underlying parsers have vulnerabilities
Web Service Automation is Our Friend…..Or Is It?
UDDI, WSDL, SOAP Faults (errors), Descriptions….OH BOY!
UDDI
- UDDI contains plus data
- Machine-controlled War-Dialers (scanners) will rummage around for UDDI’s for services (i.e. Bank service found here)
- Contains adequate data to attack service (i.e Here is however the bank service works)
- Machine-controlled programs consume WSDL and begin scanning the service (i.e. mechanically issue scanning/attack messages)
- SOAP Faults come back data regarding the service (i.e Bank service is running on IIS version ?? and uses.Net parser)
- SOAP Faults returns errors from the backend resources like the SQL DB, or Mainframe (i.e Bank service is mistreatment Oracle sound unit version
Good development practices will alleviate this threat. How many programs or programmers area unit good though?
Parameter Tampering
- Parameters are changed
Code Injection
- Code is injected inside associate XML part
Virus/Spyware/Malware Injections
- XML Attachments (MTOM, DIME, MIME) area unit used as a delivery mechanism for virus
Session Tampering and Identity Hijacking
- Some net Services keep track of sessions with a singular ID. Attackers will use that ID to become a part of the dealing going down.
Web Services Hacking
Attackers See Opportunities!
Web Services provide an entirely new dimension to the normal security stack.
This new layer could be a business layer and current security practices don't provide sufficient protection. Why:
- entirely new technology, with new, comes issues
- Operates over common net transports, ancient firewalls have supported the thought of stopping a
- attacks at the OS level not at the Message Level (Layer 3-5).
- Automation and Toolkit development (Reuse of those tools)
- Standardization of attack vectors, you'll attack .NET and Java business applications mistreatment equivalent messages.
- Inherent Descriptions (WSDL, outfit websites, etc.)
A Significant Problem in System Distribution
The problem with any distributed system is that one
a failure inside the system will have an associate unknown impact on the system in its completeness.
In the use of net Services, we have a tendency to area unit adopting a observe of employ and system distribution that spans one or additional networks and potentially the web.
Steps in Web Services Hacking
I’ve broken this tutorial down into four steps:
- Learn as much as you can about the system
- Do your Homework
- Launch the Attack
- Clean up after yourself
Step 1: Learning, Finding a Web Service
You could search a Public UDDI during this step however in most cases public UDDI data can describe services that are created for public usage and area unit protected intrinsically.We’re about to be a touch trickier here by searching for services that area unit not up for public consumption. The technique is understood as creeping.
Command:
- wget –l fifty –r http://bankwebserver.com
- wherever “–l 50” is that the most range of links to show
- And “–r” recursively crawls the location
Returns:
- you've got received twenty-seven files kind the server
Command:
- realize. –name *wsdl*
Returns:.
- /ws/bankservice.asmx?wsdl
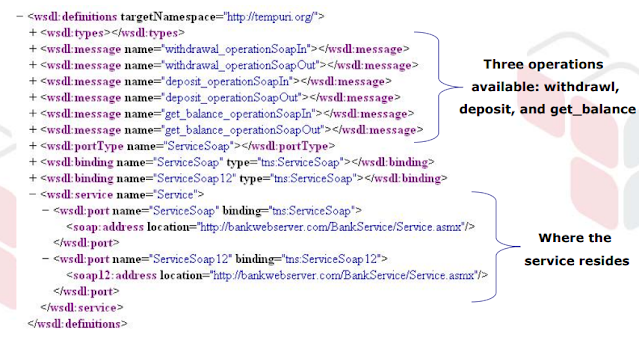
We found a WSDL, currently, let's look to envision what we will decide regarding the service….
Learning, Examining a Web Service
Learning, Examining a Web Service (cont)
Learning (Attempting to Obtain Errors)
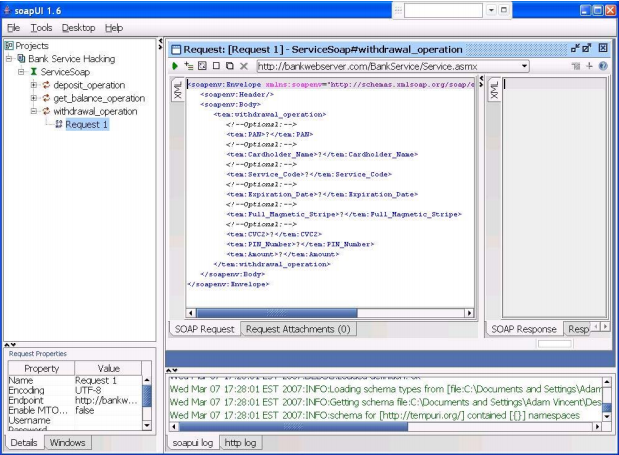
Learning (Attempting to Obtain Errors)
You would continue this method whereas searching for areas to take advantage of, their area unit machine-controlled tools that try this for you
You currently know the following:
- Service Location – web.bankwebserver.com
- Application Server Platform – IIS with.Net Version 5.0
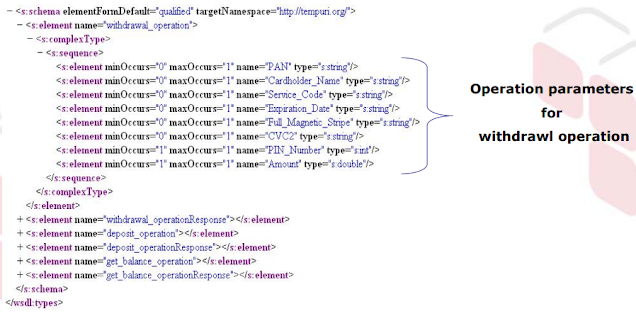
- Net Service Purpose (Withdrawl, Deposit, Balance)
- The expected values of the request? PAN, Cardholder_Name, Service_Code, Expiration_Date, Full_Magnetic_Stripe, CVC2, PIN_Number, and Amount.
- you recognize that the service is running
- The service returns errors that illustrate its not mistreatment SSL, and that it's running IIS .NET version 5.0.23.
In a world scenario, you'd need to understand tons additional, however, let's continue for currently.
Step 2: Do Your Homework
The tool of Choice: web.google.com
Research:
- Analyze Security capabilities in situ, explore for deficiencies
- Vulnerabilities in IIS .NET 5.0.23 application servers
- Vulnerabilities in.Net Parser’s with the correct version
- Analyze DOS/XDOS opportunities
- we have a tendency to currently would have enough data to thrust ahead with the actual attack.
Ready Set Go!
Step 4: Clean Up After Yourself
A real hacker would be ready to do some things to hide their tracks.
I’m but am not virtuoso enough to speak regarding those things
What is Web Services Hardening
Confidentiality, Integrity Enforcement
Mitigate Transport Threats to Include Sniffing, Snooping, Routing Detours, and other types of transport threats
Transport Layer Encryption
- SSL/TLS – solely smart whereas in transit between intermediaries, does not persist from end-to-end.
WS-Security – Persists from end-to-end
- XML secret writing – Encrypted message content, does not require the entire message to be encrypted.
- XML Digital Signatures – Digital signatures of message content doesn't need the entire message to be digitally signed.
XML Structure Threat Detection
Secure Deployment
UDDI and WSDL area unit like “Maps to the Treasure” and maybe Treated intrinsically.
You wouldn’t leave the particular map to your
treasure get into plain sight, would you?
UDDI, WSDL
- Virtualize Internal Services to shoppers through the creation of virtual endpoints delineated by generalized WSDL and UDDI descriptions.
SOAP Faults and Error Messages
- Don’t enable SOAP faults and errors to be relayed to doubtless malicious shoppers. Generalize SOAP faults to contain no information regarding deployed application varieties and versions.
Input Validation (Parameter Tampering)
The service code layer is wherever development is finished in making business capabilities and is that the best to hack. this is often in all probability the most crucial to guard.
Basic Parameter Validation
- Don’t use strings because of the allowed information sort. That’s like allowing something to pass.
- Validate number values for length
Specifically Parameter Validation
- If it's purported to be an SSN then validate it's one!
- If it’s a zipper code validate that its [[0-9][0-9] [0-9] [0-9] [0-9]]
XML Schema provides a tool to validate message parameters
according to preset business usage.
Input Validation (Code Injection)
Some Code Injection protection is inherent in having a constrained schema validation on input parameters although there are some places where Schema does not suffice.
Wherever strings or more general character sets are allowed validation should be done to verify malicious code is not present.
Be Careful about Unicode representations of characters to avoid detection. Parsers will do funny things with these….
Be Careful with CDATA and XML Comments as XML parsers are designed to overlook these.
Virus Detection (virus, spyware, malware)
XML inherently doesn't have the power to execute viruses rather it's a vector to that viruses are often sent to net Services and backend applications for execution.
There area unit primarily 2 ways in which this could happen:
Primary – SOAP with Attachments, MTOM, WS-Attachments
- Web Service needs to either execute an application stored within the SOAP attachment or issue the SOAP attachment to another system for later execution.
- Mediation: Attachments should be scanned with a virus scanner, traditional virus scanning engines generally do not offer such a capability.
Secondary – Base64 encoded worm
- Web Service or other application needs to be programmed to decode BASE64 value and execute the resulting binary. The program would have to have this purpose in mind in its inception to make this work.
- Mediation: If this is the intended purpose for a large XML element and validation cannot be accomplished, the element should be decoded and then scanned by a Virus Scanning Engine. Again Virus Engines are inadequate in this purpose
Access Control
Most security conscience net Service developers use some mechanism of authentication into deployed net service capabilities.
this could be as easy as HTTP Basic or as complicated as SAML Holder of Key (HOK).
Authorization is often supported accessing the net Server itself or more specifically associate operation inside a service.
With web services turning into additional subtle the later is that the recommended methodology in moving forward.
Even once access management is in site, a defense comprehensive the approach is usually recommended to alleviate concern once a malicious entity has hijacked associate existing licensed identity.
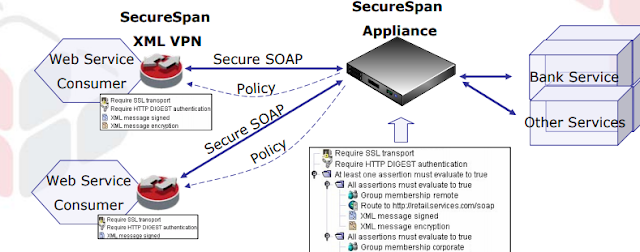
XML Appliances – All Hardening Wrapped UP
So I’ve urged many hardening ways which may be wont to defend Web Services from attack. these items aren't straightforward to implement especially with development and overhead related to parsing and crypto operations.
The easier approach, Layer seven to the Rescue!
Conclusion
I’m hoping that this was a decent summary for everyone!
Related:
- What is Password Cracking?
- Types of Cyber Attack?
- What is Dark Web? How to Access Dark Web?
- What is Identity Theft Protection?


.png)















No comments:
Post a Comment