Ethical Hacking Tutorials - System Identification
It is clear that someone sitting down on your computer's keyboard can gather Information about it, including Operating Systems and running programs, but It is also possible to use a Network connection to gather information about someone remote computer. This lesson will describe some of the ways in which this information may be Gathered Knowing how this information is collected will help you to ensure that your local These activities make the Computer Safe.Identifying a Server
There are many useful resources on the Web that will allow you to gather information About domain names and IP addresses
Identifying the Owner of a Domain
The first step to identify the remote system is to see the domain name or IP address. using the You can search for valuable information including a Whois Lookup, your employer's identity A domain, and contact information, which can include addresses and phone numbers. pay attention Now there are many domain name registrars, and they are not all databases Information for all domains You may have to look for more than to find a whois database The information of the domain that you are checking.
Identifying the IP address of a Domain
There are several ways to determine the IP address of a domain. May know Whois information contained in or may require you to use the DNS or Domain Name Service Look at (A web search engine will provide many resources for IP address detection From domain names.)
Once you have an IP address, you can access the records of different members Number Resource Organization (http://www.arin.net/ or http://www.ripe.net/), to achieve Information about how IP addresses are delivered.
The first step to identify the remote system is to see the domain name or IP address. using the You can search for valuable information including a Whois Lookup, your employer's identity A domain, and contact information, which can include addresses and phone numbers. pay attention Now there are many domain name registrars, and they are not all databases Information for all domains You may have to look for more than to find a whois database The information of the domain that you are checking.
Identifying the IP address of a Domain
There are several ways to determine the IP address of a domain. May know Whois information contained in or may require you to use the DNS or Domain Name Service Look at (A web search engine will provide many resources for IP address detection From domain names.)
Once you have an IP address, you can access the records of different members Number Resource Organization (http://www.arin.net/ or http://www.ripe.net/), to achieve Information about how IP addresses are delivered.
An IP number is assigned to the Service Providers and networks in large groups, and knowing which group contains the IP address, And those with the rights of that group can be very useful. Can help you determine Information about a server or service provider that uses a website.
Identifying Services
Once you establish the owner and IP address of a domain, you can start For information about the server that the domain refers to.
Ping and TraceRoute
Now that you know who the owner of the domain is, and who is assigned the IP number, then you
Check to see if the server on the website is actually active. Ping will command to Tell you if there is actually a computer connected to that domain or IP. order
Once you establish the owner and IP address of a domain, you can start For information about the server that the domain refers to.
Ping and TraceRoute
Now that you know who the owner of the domain is, and who is assigned the IP number, then you
Check to see if the server on the website is actually active. Ping will command to Tell you if there is actually a computer connected to that domain or IP. order
Ping domain or
Ping ipaddress
If the ping command output indicates that sent packets were received, then you Assume that the server is active.
Another command, Traceart (in Windows) or Traceroute (in Linux) will show you the steps that There is information when traveling from your computer to a remote computer. Trail Packet holders will sometimes give you additional information about the computer network with a computer that targets your trace. For example, the computer will Similar IP addresses that will often be part of the same network.
Banner Grabbing
The next step in identifying the remote system is to try to connect using Telnet and FTP. The server programs for these services display text messages called banners. Can state a banner Clearly and precisely what the server program is running. For example, when you connect to A Anonymous FTP server, you may receive the following message:
Connected to Anon.server.
220 ProFTPD server (welcome.)
User (anon.server: (none)):
The primary drawback of using banners for collecting information about a system is that The clever system administrators can spoil the banner. A banner in which nobody reads NoOfYourBusiness The server is clearly misleading, but a Unix system with a banner that reads WS_FTP server (A) Windows-based FTP server) is going to complicate any intelligence gathering done.
Identifying Services from Port and Protocol
You can also determine which programs are running on a port on the system Open and what protocols are in use.
Start by looking at your own local computer. Go to and go to the command line or shell prompt
program using netstat -a (or all) switch:
netstat -a
The computer will display a list of open ports and those using the services Ports:
Active connection
With this, you can see many programs and services running on your locality Computers - many of which you do not even realize.
Another program, called Fort, provides information similar to what NetStat does, but It is also information about which programs are using open ports and protocols. (Fport is available for free
Download from www.foundstone.com.)
Another program, called Nump (for Network Mapper), will conduct a thorough investigation of you
Computers for open ports. When the namp is operated, it will display a list of open ports and services
Or protocols that use those ports. It may also be able to determine what the operating system is
Is using your computer. For example, if you run the namp on your local computer, you can see
The following production:
Nmap is available on your hacker high school or L.A. It is also available for download From www.insecure.org
System Fingerprinting
Now that you know how to identify the server and scan for open ports and how to use it To determine which services are running, you can keep this information together. The fingerprint is a remote system, which most likely establishes operating systems and services Remote computer is running.
Scanning Remote Computer
Using a domain name in addition to the IP address or 127.0.0.1 allows as logic for the name You can scan for the open port on the remote computer. This does not mean that there will be open Ports, or that you will find them, but it allows you to try.
For example, imagine that you are receiving a large amount of spam e-mail, and you Want to get information about the person who is sending you these e-mails. To see the Header of one of the e-mails, you see that many e-mails have arisen Similar IP address: 256.92.116.13 (See text 9: Email security for more information on reading e-mail. Mail header).
A whois lookup shows you that the address is part of the block assigned to a large ISP, but gives
You do not have any information about this particular IP address.
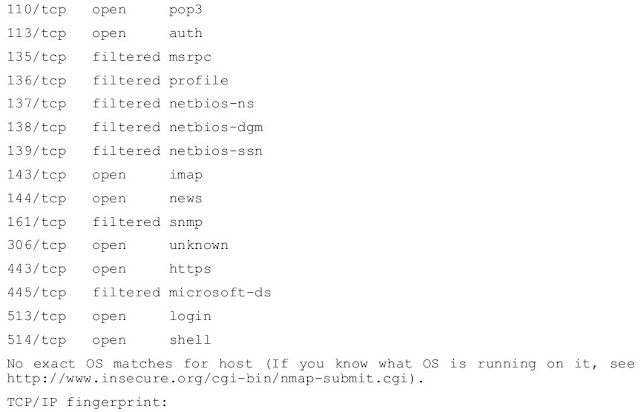
If you use Numap to scan a computer at that address, you will get the following results:
nmap -ss-o 256.92.116.13
The ports marked as filtered are potentially well-known for the attack, so this is not A Surprised to list them as filtered What is most interesting is that for ports 21, 22, and 23 - FTP, ssh, and telnet - all are listed in the open form.
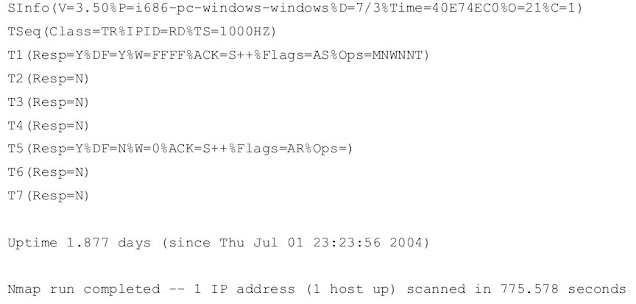
The last thing that Namap, is to try to identify the operating system that is running Computer scanned. In this example, the test that runs the NAMP is inconclusive, however, since then Nmap shows that both FTP and telnet services are running, you can try to connect Through each of them to see if there is a banner that will be broadcasted.
220 ftp316.pair.com NcFTPd Server (License Copy) is ready.
When you join through Telnet, the computer displays a banner that says FreeBSD / i386 (ttyp7)
A quick web search tells you that NcFTPd is a Unix program and that FreeBSD is a Unix-type
The operating system, it is possible that the server is running a version of FreeBSD as its operating
system. You can not be certain that this is accurate (banners can get worse), but you can Accept this as a reasonable estimate.
So, using the Nmap along with FTP and Telnet, you have determined that the server is By sending spam you run a Unix-type operating system - perhaps FreeBSD - and installed To send and receive large numbers of information through many services including FTP, Telnet, HTTP, SMTP, and pop3


.png)
















No comments:
Post a Comment