Ethical Hacking Tutorials - What is Sniffing?
Sniffing is a data Interception Technology.
- very commonly used by prying hackers.
- Sniffing involves capturing, decoding, inspecting and interpreting the information.
- The purpose is to steal information, usually user IDs passwords, details, credit card numbers, etc.
- Sniffing is generally referred to as a "passive" type of attack, wherein the attackers can be silent and invisible on the network This makes it difficult to detect, and hence it is a Dangerous type of attack.
Sniffing Ethical Usage
- Packet capturing
- Network traffic usages and analysis
- Network troubleshooting
Sniffing Unethical Usage
- User identity and password-stealing
- Email or instant message data stealing
- Packet spoofing and data theft
- Monetary of reputational damage
Types of Sniffing Attack
- DHCP Attack
- Spoofing Attack
- Password Attack
- MAC Flooding
- DNS Poising
- ARP Poising
What is SSL?
- SSL Secure Socket Layer
- It provides a secure transport connection between applications (e.g. web server and a browser)
- SSL was developed by Netscape.
- SSL version 3.0 has been implemented in many web browsers (Chrome browser and MS Internet Explorer) and web server and widely used on the Internet SSL v3.0 was specified in the internet to TLS(Transport Layer Security).
- TLS can be viewed as SSL v3.1
Secure Sockets Layer(SSL)
SSL(Secure Sockets Layer) is a WEB STANDARD SECURITY TECHNOLOGY for establishing an encrypted link between a server and a client
typically a server(which means a website) and a browser(your browser); or a mail server and a mail client.
SSL allows sensitive information such as credit card numbers, social security numbers, and login credentials to be transmitted securely.
Normally, and sent between browsers and web servers are sent in plain text leaving you vulnerable to eavesdropping.
If an attacker is able to intercept all data being between a browser and a web server they can see and use that information.
SSL secures millions of people's data on the Internet every day, especially during online transactions or when transmitting confidential information.
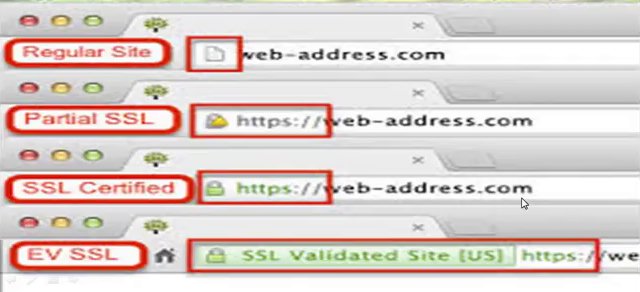
Internet users have come to associate their online security with the lock icon that comes with an SSL-secured website or green address bar that comes with an extended validation SSL-secured website SSL-secured website also begins with https rather than HTTP.
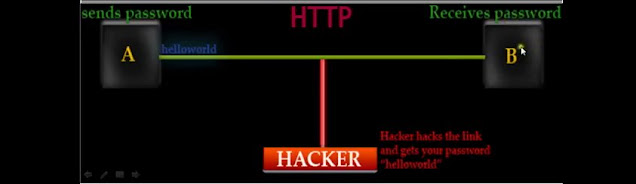
Assume that there exist two communication parties A (client) and B (server). Now A sends a message or password to and an intruder(hacker) gets unauthorized access in between.
Now lets study both the causes HTTP and HTTPS.
From case-2 you got to know that if an intruder(hacker) gets unauthorized access to ongoing communication between A and B, A will not lose his/her confidential message or password like "HelloWorld" because of the message or password is encrypted.
How HTTP and HTTPS work
Assume that there exist two communication parties A (client) and B (server). Now A sends a message or password to and an intruder(hacker) gets unauthorized access in between.
Now lets study both the causes HTTP and HTTPS.
From case-2 you got to know that if an intruder(hacker) gets unauthorized access to ongoing communication between A and B, A will not lose his/her confidential message or password like "HelloWorld" because of the message or password is encrypted.
So the hacker gets the encrypted passwords like "Sy234tyus".
The address bar tums from white to green indicating to visitors the website is using Extended Validation SSL
The website owner is a legally incorporated company name is displayed prominently on the address bar real estate.
The address bar tums from white to green indicating to visitors the website is using Extended Validation SSL
The website owner is a legally incorporated company name is displayed prominently on the address bar real estate.
Extended Validation SSL is the only way for a company to get its name displayed in the browser address bar
The standard HTTP has changed the browser that the connection between the server and browser must be secured using SSL
The yellow padlock is activated, showing you that the browser connects to the server is now secure. It there is no padlock or the padlock shows a broken symbol, the page does not use SSL
DHCP Attack
Client PC is sending DHCP requests on the network. This request is a broadcast and all Host on the LAN will receive it.
The DHCP server is then replying to the Client with messages that will configure the Host Client PC with IP Address, Subnet Mask, and Default Gateway.
Client PC is sending DHCP requests on the network. The DHCP server is then replying to the Client with messages that will configure the Host Client PC with IP Address, Subnet Mask, and Default Gateway. When we have an attacker PC in the network he will simulate the DHCP server on his host PC.
With this action, he will be able to reply to DHCP request before the Real DHCP server because of it closer to the Client Host.
The yellow padlock is activated, showing you that the browser connects to the server is now secure. It there is no padlock or the padlock shows a broken symbol, the page does not use SSL
DHCP Attack
Client PC is sending DHCP requests on the network. This request is a broadcast and all Host on the LAN will receive it.
The DHCP server is then replying to the Client with messages that will configure the Host Client PC with IP Address, Subnet Mask, and Default Gateway.
Client PC is sending DHCP requests on the network. The DHCP server is then replying to the Client with messages that will configure the Host Client PC with IP Address, Subnet Mask, and Default Gateway. When we have an attacker PC in the network he will simulate the DHCP server on his host PC.
With this action, he will be able to reply to DHCP request before the Real DHCP server because of it closer to the Client Host.
It will configure the Client host with IP address of that subnet but it will also give to host false Default Gateway address and maybe even false DNS server address.
DNS server address and Default Gateway address will both be IP address of Attacker Computer. In this manner, he will point out all the communication of the Client host to himself.
Later he will make it possible to forward the frames from the Client host to real destinations in order to make communication of Client possible.
The client will not know that his communication is always going across the Attacker PC and that Attacker can easily sniff frames.
In Computer Networking, MAC flooding is a technique employed to compromise the security of network switches
This allows the switch to direct data out of the physical port where the recipient is located, as opposed to indiscriminately broadcasting the data out of all ports as a hub does.
After launching a successful MAC flooding attack, a malicious user could then use a packet analyzer to capture sensitive data being transmitted between other Computers, which would not be accessible were the switch operating normally.
The attacker may also follow up with an ARP spoofing attack which will allow them to retain access to privileged after switches recover from the initial MAC flooding attack.
Switches keep a translation table that maps various MAC addresses to the physical ports on the switch, As a result of this, they can intelligently route packets from one host to another.
MAC Attack
In Computer Networking, MAC flooding is a technique employed to compromise the security of network switches
This allows the switch to direct data out of the physical port where the recipient is located, as opposed to indiscriminately broadcasting the data out of all ports as a hub does.
After launching a successful MAC flooding attack, a malicious user could then use a packet analyzer to capture sensitive data being transmitted between other Computers, which would not be accessible were the switch operating normally.
The attacker may also follow up with an ARP spoofing attack which will allow them to retain access to privileged after switches recover from the initial MAC flooding attack.
Switches keep a translation table that maps various MAC addresses to the physical ports on the switch, As a result of this, they can intelligently route packets from one host to another.
But switches have limited memory. MAC flooding makes use of this limitation to bombard switches with fake MAC addresses until the switches cannot keep up.
Once this happens to a switch, it then enters into what is known as "fail-open mode," where it starts acting as a hub by broadcasting packets to all the ports on the switch.
Once that happens, sniffing can be performed easily. MAC flooding can be performed by using mac off, a utility that comes with the sniff suite.
A spoofing attack is a situation where an attacker successfully pretends to be someone else by falsifying data and thereby gains access to restricted resources or steals personal information.
Spoofing attacks can be performed in various ways. An attacker can use the victim's IP address illegally to access their accounts, to send fraudulent emails, and to set up a fake website for acquiring sensitive information such as passwords, account details, etc.
Attackers can even set up the fake wireless access point and simulate legitimate users to connect through the illegitimate connection.
macof can flood a switch's CAM table, thus new MAC addresses cannot be saved, and thus we can monitor all traffic passing through it. (131000)
macof -i eth1
Let's Find the MAC address on Windows
Now you can see your computer MAC address. Also, you can change your MAC address
Next Tools is Best called CAIN and ABEL
Properties:
Host-Based Detection - you can use small utilities to detect if the NIC(Network Interface Card) is running in a promiscuous mode on any host in a network. Since the basic requirement for a sniffer to work is to put the network interface in "read all" mode, disabling it can very effectively help to shut down stray suffers.
Network-Based detection - anti-sniffer software can run to detect the presence of specific signature packets. Modern anti-virus or anti-spyware software is capable of detecting Sniffing software and disabling it.
Spoofing Attack
A spoofing attack is a situation where an attacker successfully pretends to be someone else by falsifying data and thereby gains access to restricted resources or steals personal information.
Spoofing attacks can be performed in various ways. An attacker can use the victim's IP address illegally to access their accounts, to send fraudulent emails, and to set up a fake website for acquiring sensitive information such as passwords, account details, etc.
Attackers can even set up the fake wireless access point and simulate legitimate users to connect through the illegitimate connection.
Best Tools for Sniffing
- Wireshark is a free and open-source packet analyzer.
- It is used for network troubleshooting, analysis, software and communications protocol development, and education.
- Originally named Ethereal, the project was renamed Wireshark in May 2006 due to trademark issues.
- Capturing raw network traffic from an interface requires elevated privileges on some platforms
- VoIP calls in the captured traffic can be detected. It encoded in a compatible encoding, the media flow can even be played
Download: Wireshark
MAC Flooding with macof
macof can flood a switch's CAM table, thus new MAC addresses cannot be saved, and thus we can monitor all traffic passing through it. (131000)
macof -i eth1
Let's Find the MAC address on Windows
- Step 1: Type windows-key + r
- Step 2: then Type Devmgmt.msc
- Step 3: Then go to Properties
- Step 4: and then go to Advanced
- Step 5: then Network Address
Now you can see your computer MAC address. Also, you can change your MAC address
Next Tools is Best called CAIN and ABEL
Properties:
- Network Sniffer
- Password Cracker
- APR Poison Tool(MITM)(Main in the middle attack)
- Hack Wireless Network with Airpcap
- Traceroute...and many other .propertiese
How to Detect a Sniffers
Host-Based Detection - you can use small utilities to detect if the NIC(Network Interface Card) is running in a promiscuous mode on any host in a network. Since the basic requirement for a sniffer to work is to put the network interface in "read all" mode, disabling it can very effectively help to shut down stray suffers.
Network-Based detection - anti-sniffer software can run to detect the presence of specific signature packets. Modern anti-virus or anti-spyware software is capable of detecting Sniffing software and disabling it.
Related:
Tags: what is sniffing,sniffing,what is network sniffing,what is sniffing network,what is sniffing and spoofing,packet sniffing,what is sniffing?,network sniffing,what is packet sniffing,what is sniffing attack,what is sniffing in hindi,what is sniffing in hacking,what is sniffing the network,what is sniffing attack in hindi,what is sniffing network traffic,what is sniffing and spoofing in hindi
- Ethical Hacking Tutorials - What is Steganography?
- Ethical Hacking Tutorials - What is Windows Hacking?
- Ethical Hacking Tutorials - What is Viruses
- Hacking with Android - Become a True Android Hacker
Tags: what is sniffing,sniffing,what is network sniffing,what is sniffing network,what is sniffing and spoofing,packet sniffing,what is sniffing?,network sniffing,what is packet sniffing,what is sniffing attack,what is sniffing in hindi,what is sniffing in hacking,what is sniffing the network,what is sniffing attack in hindi,what is sniffing network traffic,what is sniffing and spoofing in hindi


.png)

















No comments:
Post a Comment