Ethical Hacking Tutorials - What is Cryptography?
Cryptography is a method of Storing and Transmitting Data in a particular form so that only those for whom it is intended can read and process it.
kryptos - Hidden, secret
Graphein - Writing
Two Main Goal of Cryptography
- Information Privacy
- Authentication(Verify Identity)
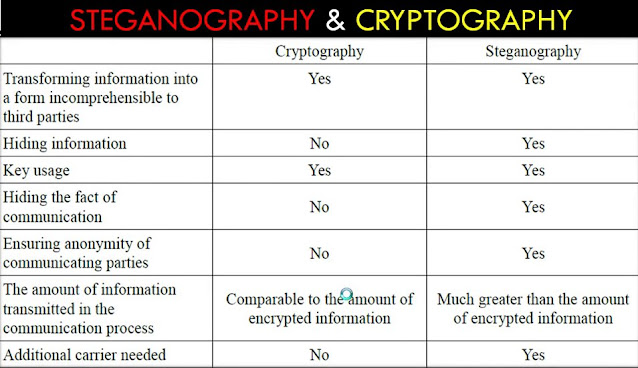
Difference Between Steganography and Cryptography
Steganography
- The encrypted letter could be seen by anyone but cryptography make the message not understandable
- The end result in cryptography is the ciphertext
- The goal of a secure cryptographic is to prevent an interceptor from gaining any information about the plaintext from the intercepted ciphertext
- Any person has the ability to detect and modifying the encrypted message
- Steganography can not be used to adapt the robustness of a cryptographic system
Cryptography
- Stenography is hiding the message in another median so that nobody will notice the message
- The end result of information hiding is the stego-media
- The goal of secure stenographic methods is to prevent an observant intermediary from even obtaining knowledge of the more presence of the secret data.
- The hidden message is imperceptible to anyone
- Stenography can be used in conjunction with cryptography by hiding an encrypted message
What is Cipher?
The ciphertext is encrypted Text. The plaintext is what you have before encryption, and the ciphertext is the encrypted result. The term cipher is sometimes used as a synonym for ciphertext, but it more properly means the method of encryption rather than the result.
Cipher is nothing more than an Algorithm used for both encryptions as well as decryption.
Types of Classical ciphers
- Substitution Ciphers
- Transposition Ciphers
In a substitution cipher, letters (or groups of letters) are systematically replaced through the message for other letters (or group of letters)
A well-known example of a substitution cipher is the Caesar Cipher. To encrypt a message with the Caesar Cipher, each letter of the message is replaced by the letter three positions later in the alphabet.
Hence, A is replaced by D, B by T, etc,
Finally, X, Y, and Z are replaced by A B and C respectively.
So, for example, "WIKIPEDIA" encrypts as "ZLNLSHGLD",
Caesar rotated the alphabet by three letters, but any number work.
Another method of substitution Cipher is based on a keyword, All spaces, and repeated letters and removed from a word or phrase, which the encoder then uses as the start of Cipher alphabet. The end of the Cipher alphabet is the rest of the alphabet in order without repeating the letters in the keyword.
For example, If the keyword is CPHIER, the cipher alphabet would look like this:
Normal Alphabet: a,b,c,d,e,f,g,h,i,j,k,l,m,n,o,p,q,r,s,t,u,v,w,x,y,z
Cipher Alphabet: c,i,p,ph,e,r,s,t,u,v,w,x,y,z,a,b,c,d,f,g,i,k,l,m,n,o,q
The previous example were all examples of monoalphabetic substitution cipher, where just one cipher alphabet is used. It is also possible to have a polyalphabetic substitution cipher, where multiple cipher alphabets are used.
The encoder would just make up two or more cipher alphabets using whatever techniques he or she chooses, and then encode their message, alternating what cipher alphabet is used with every letter or word.
This makes the message much harder to decode because the codebreaker would have to figure out both cipher phablets.
Another example of a polyalphabetic encoding method. With the square, there are 26 different cipher alphabets that are used to encrypt text. Each cipher alphabet is just another right word Caesar shift of the original alphabet. This is what a Vigenere square looks like.
This makes the message much harder to decode because the codebreaker would have to figure out both cipher phablets.
Another example of a polyalphabetic encoding method. With the square, there are 26 different cipher alphabets that are used to encrypt text. Each cipher alphabet is just another right word Caesar shift of the original alphabet. This is what a Vigenere square looks like.
Transposition Cipher
In a Transposition Cipher, the letters themselves are kept unchanged, but their order within the message is scrambled according to some well-defined scheme. many transposition ciphers are done according to a geometric would be to write every word backward.
"Hello my name is Alice"
would be now
"olleH ym eman si ecilA"
In a column cipher, the original message is arranged in a rectangle, from left to right and top to bottom,
Next, a key is chosen and used to assign a number to each column in the rectangle to determine the order of rearrangement.
The number corresponding to the letters in the key is determined by their place in the alphabet, i.e. is THE SKY IS BLUE, this is how you would arrange your message:
CAT
3120
THE
SKY
ISB
LUE
Next, you take the letters in numerical order and that is how you would transpose the message. You take the column under A first, then column under C, then the column under T, as a result, your message
"The sky is blue" has become: HKSUTSILEYBE
In the Chinese cipher's method of transposing, the letters of the message are written from right to left, down and up columns to scramble the letters. Then, starting in the first row, the letters are taken in order to get the new ciphertext,
For example, if the message needed to be enciphered was THE DOG RAN FAR, the Chinese cipher would look like this:
R R G T
A A O H
F N D E
The ciphertext then reads: RRGT AAOH FNDE
What is Stream?
A Stream Encryption is the encryption of each letter one by one and changes the encryption key after each letter.
In Cryptography, an ONR-Time pad (OTP) is an encryption technique that cannot be cracked if used correctly. In this technique, a plaintext is paired with a random secret key(or ped). Then, each bit or character of the plaintext is encrypted by combining it with the corresponding bit or character from the pad using modular addition
To Understand a One-time pad you need to have a key that has the same length of the key as the message. The key is chosen from the random of string letters and does not resemble any English language.
Linear Feedback Shift Register
A pseudorandom process is a process that appears to be random but not
The bit position that affects the next state is called the taps
The XOR gate (sometimes EOR gate, or EXOR gate and pronounced as Exclusive OR gate) is a digital logic gate that implements an exclusive or; that is, a true output (1/HIGH) results if one, and only one, of the inputs to the gate is true.
Linear Feedback Shift Register
The bit positions that affect the next state are called the taps.


.png)















No comments:
Post a Comment