Ethical Hacking Tutorials - Social Engineering Attack
Social engineering is the art of manipulating people so they give up confidential information.
Social Engineering is a threat, often overlooked but regularly exploited; to take advantage of what has long been considered the weakest link in the chain of an organization The "Human Factor".
A Social Engineering will commonly use the telephone or Internet to trick a person into revealing sensitive information or getting them to do something that is against the typical policy. By this method, social engineers exploit the natural tendency of a person to trust his or her word, rather than exploiting Computer security holes. It is generally agreed upon that "users are a weak link" insecurity and this principle is what Social Engineering Attack Possible.
What Motivates an Individual to carry out a Social Engineering Attack?
Human-Based Attack
A cybercriminal does a deep search for email addresses of your organization on the Internet
They find all publicly available email addresses of your employees
They use these to launch a phishing attack on as man employees as possible
if you seem which email you received it is fake email then you can report on this website phishtank.com
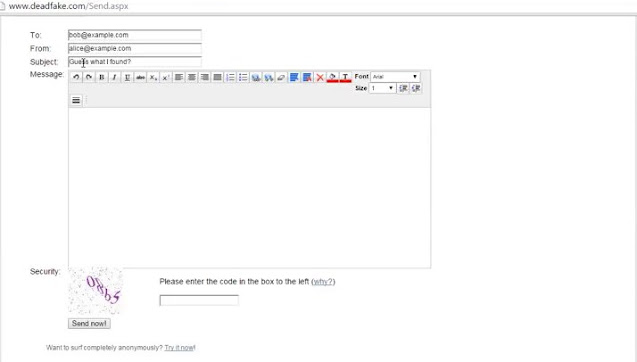
Fake Mail
Attacker use these three websites to Send Fake Mail
Related:
- Become familiar and comfortable with the target, and formulate strong pretext
- It could be connecting on a personal level over the phone or as personal os showing family pictures and sharing stories with the receptionist in the lobby. It can also be as extensive as building an online relationship with the target through a fake profile on a dating or social networking site. Creating rapport is covered more in-depth in the ......?
- This action could be the end of the attack or the beginning of the next stage
- A well planned and smooth exit strategy is the attack's goal and find activities in the attack.
What Motivates an Individual to carry out a Social Engineering Attack?
- Financial gain: For a variety of reasons, an individual might become transfixed on monetary gains. For example, he may believe he deserves more money than he earns or maybe there is a need to satisfy an out-of-control gambling habit.
- Self Interest: an individual might, for example, want to access or modify information that is associated with a family member, friend or even a neighbor.
- Revenge: for reasons only truly known by an individual, he might look to target a friend, colleague, organization or even a total stranger to satisfy the emotional desire for vengeance
- External pressure: an individual may be receiving pressure from friends, family, or organized crime syndicates for reasons such as financial gain, self-interest, or revenge.
Types of Social Engineering Attack
Human-Based Attack
- Posing The Legitimate End-User
- Posing a Technical Support
- Posing As An Important User
- Phishing
- Pop-up Windows
- Fake Mail
- Using SMS
- Repackaging Apps
How The Bad Guys Attack
A cybercriminal does a deep search for email addresses of your organization on the Internet
They find all publicly available email addresses of your employees
They use these to launch a phishing attack on as man employees as possible
if you seem which email you received it is fake email then you can report on this website phishtank.com
Fake Mail
Attacker use these three websites to Send Fake Mail
Related:
- Ethical Hacking Tutorials - What is Sniffing?
- Ethical Hacking Tutorials - What is Steganography?
- What is a Firewall? - Explain How A Firewall Works
- Google Dorks List with Example for Hacking and Pentesting


.png)

















No comments:
Post a Comment