Ethical Hacking Tutorials - What is Steganography?
Greek Words: Steganography is a practice to hide a file, message, image, or video within another file, message, image or video. Steganography combines the Greek words
STEGABOS - "Covered"
GRAPHIE - "Writing"
- Steganography is the art and science of writing hidden messages in such a way that no one apart from the intended recipient knows of the existence of the message.
- This can be achieved by concealing the existence of information within seemingly harmless carriers of cover.
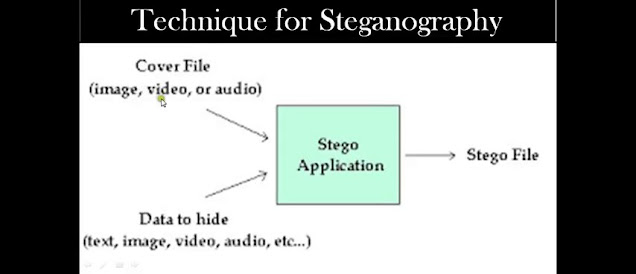
- Carrier: Steganography con used in the text, images, videos, audio and etc.
Media files are ideal for steganographic transmission due to their large size.
For example, a sender might start with an innocent image file and can adjust the color of each hundred pixels corresponding to one letter in the alphabet.
For example, a sender might start with an innocent image file and can adjust the color of each hundred pixels corresponding to one letter in the alphabet.
The change is so subtle that the person who is not specifically searching for it, that change is not likely to be kept in mind
Steganography techniques have been used for ages and they date back to ancient Greece. The aim of steganographic communication back then and now, in modern applications, is the same: to hide secret data (a sonogram) in an innocently who is aware of the information hiding procedure.
History and Evolution of STEGNOGRAPHY
Steganography techniques have been used for ages and they date back to ancient Greece. The aim of steganographic communication back then and now, in modern applications, is the same: to hide secret data (a sonogram) in an innocently who is aware of the information hiding procedure.
In an ideal situation, the existence of hidden communication cannot be detected by third parties.
Herodotus
The first use of steganography is reported by Herodotus, the so-called father of history, who mentions that in ancient Greek, the hidden text was written on wax tablets
It Uses Ethical Hacking and Non-Ethical Hacking
Steganography is widely used for centuries. Here are some
The first use of steganography is reported by Herodotus, the so-called father of history, who mentions that in ancient Greek, the hidden text was written on wax tablets
- write a message on a tablet and covered it with wax
- Secret letters can be hidden in the messengers' shoe soles
- Use pigeons to carry secret notes
- Woman's earrings
- A very common steganographic scheme in history was the use. Invisible ink (like urine or milk), is still be used by a lot of children (e.g. lemon-based ink)
Types of STEGNOGRAPHY
- Tech Steganography
- Image Steganography
- Audio Steganography
- Video Steganography
Steganography is widely used for centuries. Here are some
- Hacker can embed all sorts of Malware to an unsuspecting user. Typically, an image file is attached to an email with an attractive header, the user clicks on it and the embedded file gets executed.
- The terrorist can embed the message
- Attackers send Illegal stuff with normal video
- Hidden messages on papers written in secret ink.
- In the form of small parts (such as words or letters) between the other words of less suspect cover text, hidden messages are delivered according to a certain rule or key. This particular form of steganography is called a zero.
- Messages written in Morse code on the front and then knitted message in pieces of clothing worn by a courier.
- A message wrote on the envelope in the area covered by postage stamps
Tools are Used in Steganography
- Ethical Hacking Tutorials - What is Windows Hacking
- Ethical Hacking Tutorials - What is Scanning
- Hacking with Android - Become a True Android Hacker
- How to use Google Like a Pro?
Tags: steganography,what is steganography,what is steganography and how it works,stegnography,stenography,steganography in hindi,image steganography,image steganography tutorial,what is use steganography,what is steganography in hindi,what is steganography in cryptography,what is steganography on technical vani,stegonography,what is security,what is incryption,steganography practical tutorial


.png)














No comments:
Post a Comment