What is Penetration Testing?
One of the major issues of security information system. Increasing connectivity Computer, Increasing Sensitivity and Belgaum System Through Internet The development of the system's size and complexity has made software security a major problem Now compared to the past.
Apart from this, it is a business essential for adequate security Organization's information assets by following a comprehensive, structured approach Protecting from the risks that the organization can face.
In an attempt to solve Safety experts and mandatory safety rules are followed by security experts Developed various safety assurance methods including proof of correctness, layered design, Software engineering environment, and penetration testing.
Penetrating Testing is a comprehensive method to complete, integrate, operate and test Trusted computing base consists of hardware, software, and people. process Includes an active analysis of the system for any potential vulnerabilities including poor or
Inappropriate system configurations, hardware and software flaws, and operational vulnerabilities Processor Technical Counter
Penetrating Test is different from the safety functional Test. The latter displays Measurement determines the correct behavior of the system's security controls when testing No one is able to to circumvent the security control of an organization against unauthorized Its access to information and information system. This is done by imitating an unauthorized user Attacking the system using an automated device or manual method or combination of both.
This article provides an overview of the Penetration Testing. The benefits of penetration are discussed in this Testing, admission test strategies, and types, as well as a methodology for entry Test It further shows the process of using web application penetration testing Two example web applications:
Tunostore and BOG. These web applications were developed Department of Software and Information Systems, the University of North Carolina at Charlotte To display weaknesses in web applications
Why Penetration Testing?
The main goal of a vulnerability assessment is to identify controlled security vulnerabilities Conditions that can be terminated before unauthorized users exploited them.
Computing Systems use penetration testing to solve problems contained in professional vulnerabilities Focused on evaluation, high severity vulnerabilities.
Penetrating testing is a valuable assurance The assessment tool that benefits both business and its operations.
Benefits of Penetration Testing from a Business Perspective
From a professional perspective, the penetration test helps the organization to provide protection against failure Through prevention of financial loss; Prove appropriate diligence and compliance for industry regulators, Customers, and shareholders; Protect corporate image; Rationalization of information security
Investment.
Due to the notification, the organization spends millions of dollars to recover from security breaches Cost, corrective efforts, decrease in productivity and decrease in revenue. CSI study estimates
Recovery attempts may be $ 167,713.00 per event. Penetrating testing can identify and Find out risks before safety violations, thus preventing financial loss due to security Breaches
The industry has made regulatory requirements mandatory for computing systems. Can non-compliance The organization may receive heavy fines, imprisonment or last failure. Entrance test as an active service provides missing information that helps
Organization to meet the auditing or compliance aspects of the rules.
A single incident of compromised customer data can be devastating. Loss of consumer confidence And business reputation can put the whole organization in jeopardy. Penetrations make test
Increase awareness about the importance of security at all levels of the organization. this helps The organization avoids security incidents which put their corporate image in jeopardy, risk their reputation And affect customer's loyalty.
Penetrating testing evaluates and provides the effectiveness of existing safety products Assistive reasoning for upgrading future investment or security technologies It provides one "Proof of the issue" and a solid case for the proposal of investment to senior management.
Benefits of Penetration Testing from an Operational Perspective
From the operational point of view, admission test helps shape the information security strategy.
Through a quick and accurate identification of weaknesses; Active abolition of identity Risk; Implementation of corrective measures; And an increase in IT knowledge.
Penetrating test provides detailed information on actual, absorbent safety hazards if it is The safety principles and processes of an organization are included.
This will help the Organization to quickly and accurately identify the real and potential weaknesses.
Effectively and efficiently, by providing different information and priority Vulnerability, the penetration test can help the organization in a well-organized and tested configuration Changes or patches to end the identified risks.
Penetrating testing can help determine the effectiveness and probability of an organization Weaknesses This will allow the organization to prioritize and implement corrective measures.
For known weaknesses.
It takes a lot of time, effort and knowledge to deal with the process of penetration testing.
With the complexity of the test location, Therefore, penetrating testing will increase knowledge And the skill level of anyone involved in the process.
What is Involved in Penetration Testing
There are two areas that should be considered when determining its scope and objectives Access testing: used test strategies and test type.
Penetration Testing Strategies
Based on the amount of information available to the tester, there are three entrance tests Strategies: Black Box, White Box, and Gray Box.
In the Black Box Entrance Test, testers have no information about the test goal. they have To detect system loopholes from scratches.
It is like a blind similar strategy, which imitates the actions and processes of a real attacker who do not have Information about test targets
On the contrary, in the white box entrance test, the testers are provided with all the necessary Information about the test goal.
This strategy is referred to as a targeted test where Test teams and organizations work together to test, all information is provided
Before the test, the tester Partial disclosure of information about the test target is a gray box entry test.
Candidates need to collect more information before conducting the exam.
Based on the specific objectives to be obtained, there are two entrance test strategies. Including external and internal tests.
The external test refers to an attack on the test target, which uses the processes done from outside
The organization that owns the test goal. The objective of the external test is to find out whether A The external assailant can get inside and once he gets access, how far he can get out.
Internal testing is done from within the organization that owns the test goal.
Strategy It is useful to assess how much disadvantaged the employee can do. Internal test
It is focused on understanding what can happen if the test goal is successfully entered. An authorized user with standard access privileges
Penetration Testing Types
There are three areas for testing in the entrance test: System physical structure, system
The logical structure of the system, and system feedback or workflow.
These three Area scopes and penetration test define the types of networks, applications, and social engineering.
The network admission test is a moral and safe way to identify safety gaps or shortcomings The design, implementation or operation of the organization's network.
Testers analyze And exploit to determine whether modem, remote access device and maintenance connection The test can be used to penetrate the target.
Application login test is an attack simulation aimed at highlighting the effectiveness of someone Security of the application by highlighting the risks generated by the actual exploiting vulnerabilities.
Although the organization uses firewalls and surveillance systems to protect the information, Security can still be compromised as traffic can be allowed to pass through the firewall.
Social engineering attempts to obtain or compromise information about human contact The organization and its computer system are used to determine the level of security Awareness among employees in the organization which owns the target system.
It's helpful To check the organization's ability to prevent unauthorized access to its information and Information Systems.
Thus, it is an examination centered on the organization's workflow.
How to Conduct Penetration Testing?
Penetrating testing is not the only automated means and production stream This is often seen as a technical report.
It should provide a clear and concise direction How to secure information and information systems of an organization from real-world attacks An important factor in the success of the penetration test is its underlying functioning.
The systematic and scientific approach should be used to successfully prepare and form a test.
Reports that are targeted at different levels of management within an organization. It should not be To enable the tester to fully detect his intuition, the restrictive.
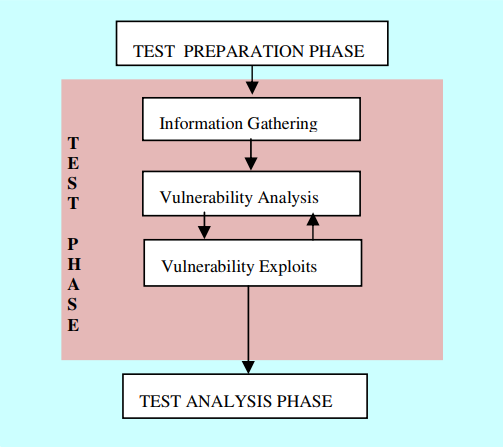
Generally, the entrance test consists of three steps:
All the necessary documents are arranged and finalized for testing during the preparation of the test.
Phase Meet the scope, purpose, timing, and decision of the examiners and organization Test period Issues such as information leakage and downtime are solved Legal contract document. Other legal agreements that are considered necessary are concluded And signed during this phase.
The bulk of the entrance test process is done during the testing phase. a variety of In this stage, automatic equipment can be used. Table 1 lists some of these devices.
This step is included The following steps: collecting information, vulnerability analysis, and vulnerability exploitation.
The stage of collecting information requires that the testers scan the physical and logical areas Identify all relevant information required in the test goal and vulnerability analysis phase.
Based on the information gathered or provided by the organization, the examiner then analyzes The vulnerabilities within the target network, host, and application. Can be tester Choose the option to use the manual method to do this step but there are also automatic tools to help the tester.
The last step allows the examiner to find out the vulnerabilities found in the previous steps.
When exploitation is not intended, for example, root access, then further analysis should be done. It is represented by the loop between vulnerability analysis and vulnerability The phase of exploitation.
The test results are thoroughly tested during the test analysis phase. the outcome The organization is provided so it should be comprehensive and systematic. the preparation of Mitigation planning is important in the entrance test. Therefore it is mandatory to include Mitigation Planning section in the Analysis Report ...
DISCUSSION
Penetrating testing can be an efficient and cost-effective strategy for the organization's safety.
Systems against attacks If done properly, then it helps the organization to identify the internal practices
It gives rise to weaknesses and other sources of weaknesses. Recognized sources Enable the organization to remove vulnerabilities, direct the safety of the system Efforts, pressure vendors to improve their products, to improve its internal business safety Practice and prove clients, shareholders and regulatory agencies that make it a good one Trust the effort to protect important business data.
Selection of a penetration team is an important factor in the success of the penetration testing process.
In evaluating the team, their qualifications should be considered,
Experience and knowledge, reputation, access, and use in the e-business community, state-of-art equipment One rule of thumb are to eliminate a team that provides the system to test.
Can not be expected to identify all the potential security vulnerabilities since the penetration test.
But just one aspect of the test. The organization should develop an overall safety test.
The strategy is in line with its risk model and security policies.
Finally, entrance testing should never be considered as one service. It is organized on one At this time System changes, threats emerge, business strategies advance and hacker tools
to develop.
Correcting or patching the vulnerability identified does not end your security Concerns and nightmare, it's just the beginning of a never-ending cycle. with this The penetration test does not guarantee full security, it is just a measurement Security currency
Related Work
The admission test procedure described by Newman includes four steps:
(1)Understanding the system,
(2) the hypothesis of the loopholes,
(3) to confirm or reject the test Hypothesis,
(4) Expansion of successful tests to achieve other hypotheses.
Are consistent with these steps The method described in this tutorial Stage (1) corresponds to the stage of collecting information,
Phases (2) and (3) vulnerability are analogous to the analysis phase and correspond to the step (4) Vulnerability is the exploitation step. Pfleeger et al. Described as an organized method for planning
A suite of entrance tests, including three steps:
(1) Identifying sensitive items,
(2) Determination of the points of vulnerability for those items,
(3) to determine the vulnerabilities to be tested
Adequacy of controls In this method a systematic approach has been provided for the hypothesis The fault in Newman's model and the vulnerability in us can be used in the analysis phase. modus operandi.
The vulnerability analysis step illustrated in this letter is based on different Categories of Weaknesses Bishop insists that the entrance test should be considered Target and test range These should be considered during the test preparation phase Our methodology Arkin et al.
The proposal is that penetration testing should be structured
According to the perceived risk, and at convenience, component or unit and system level. This can happen Our methodology was considered during the testing phase.
Conclusions
Penetrating testing is a comprehensive way to identify weaknesses in a system.
This Provides benefits such as prevention of financial loss; Compliance for industry regulators, customers And shareholders; Protect corporate image; Active eradication of identified risks.
Examiner can choose black box, white box, and gray box depending on the test.
The amount of information available to the user. Examiners can choose from internal and from External testing depends on the specific objectives to be obtained. There are three types
Entrance Test: Network, Application, and Social Engineering.
This tutorial describes the three-phase methodology, which includes the preparation, testing, and testing of the test.
Analysis phase The test phase is done in three steps: collecting information, Vulnerability Analysis, and vulnerability exploitation.
This step can be done manually or using automated tools.
This penetration test process was featured on web applications, BOG and Tunstore.
The testers should follow a broad format to present the examination results.
The most test analysis is the preparation of monetization in the important part of the phase, in which all are included Corrective measures needed for identified weaknesses.
Need a final report Adequate expansion and substance which allows those people to foment and follow the attack
Pattern and related findings...
Related:


.png)















No comments:
Post a Comment