Monday, 4 February 2019
Labels:
Database,
Programing
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Thursday, 31 January 2019
Labels:
Hacking
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Sunday, 27 January 2019
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Friday, 25 January 2019
Labels:
Networking
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Monday, 21 January 2019
Labels:
Tech
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Saturday, 19 January 2019
Labels:
MAC OS
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Friday, 18 January 2019
Labels:
Computer
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Tuesday, 15 January 2019
Labels:
Programing
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Monday, 14 January 2019
Labels:
Computer
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Sunday, 13 January 2019
Labels:
Computer
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Friday, 11 January 2019
Labels:
Computer
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Thursday, 10 January 2019
What is an Operating System?
A program that acts as an intermediary between computer users and computer hardware
Operating System targets.
- Perform user programs and make user's problems easier to solve
- Facilitate computer systems to use
- Use computer hardware in an efficient way
Computer System Structure
The computer system can be divided into four components
Hardware - Provides Basic Computing Resources CPU, Memory, I / O Device
Operating System - Controls and coordinates the use of hardware between different applications and users
Application Program - Defines the methods in which system resources are used to solve computing
Users problems
Word processor, compiler, web browser, database system, video game
User - People, machines, other computers
Four Components of a Computer system
Operating system Definition
- OS is a resource allocation
- Manages all the resources
- Decisions between conflicting requests for efficient and appropriate resource use
- OS is a control program
- Controls the execution of programs to prevent computer errors and inappropriate use
- No universally accepted definition
- When you order an operating system, everything ships a vendor But changes wildly
- "A program that runs on the computer at all times" is the kernel. Everything else is either System programs (ships with operating systems) or application programs
- The Boot Strap program is loaded on power-up or reboot
- Usually stored in ROM or EPROM, commonly known as firmware
- Starts all aspects of the system
- Load operating system starts kernel and execution
Computer System Organization
- Computer-system operation
- One or more CPUs, device controllers connect via common bus providing access to shared memory
- Concurrent performance of CPUs and devices competing for memory cycle
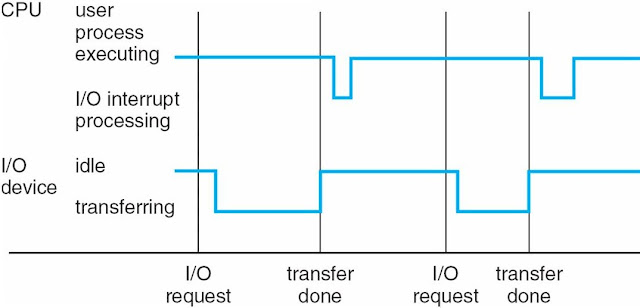
Computer-System Operation
- I / O devices and CPUs can execute concurrently
- Each device controller is in charge of a particular device type
- Each device controller has a local buffer
- Captures CPU data from local memory from main memory / up to
- From the I / O device to the local buffer of the controller
- Device controller notifies the CPU that it has completed its operation because of an interrupt
Common Functions of interrupts
- Interrupt transfer control routine is usually controlled through interrupt vectors, which all service routine addresses include
- The obstructed architecture will save the address of the obstructed instructions
- The incoming blockage is disabled while another blockage is being processed to prevent an interrupted obstruction
- The trap is a software-generated interrupt that is caused by an error or user request
- An operating system is interrupted
- Operating system protects the CPU's status by registering and storing the program counter
- Determines what kind of interference has occurred
- polling
- vectored interrupt system
- Different sections of the code determine what action should be taken for each type of interference
Interrupted Timeline
- System calls - requests the operating system to wait for user I / O to complete
- The device-status table contains an entry for each I / O device that reflects its type, address and status.
- The operating system indexes the I / O device table to determine the state of the device and modify the table entry. Include interruption
Direct Memory Access Structure
- Used for high-speed I / O devices that are capable of transmitting information closer to memory speed
- Device Controller transfers blocks of data from buffer storage directly into the main memory without CPU Interference
- Instead of one per bar, only one block per block is generated
Storage Structure
- Main memory - only large storage media that the CPU can access directly
- Secondary storage - Expansion of main memory which provides large non-volatile storage capacity
- Magnetic discs - Hard metal or glass platters, which are covered with the magnetic recording material
- The surface of the disc is divided logically into tracks, which are divided into sectors
- Disk controller determines logical interaction between device and computer
Storage Hierarchy
- Hierarchy storage system
- Speed
- Cost
- Instability
Caching - copying information in the fast storage system; The main memory can be seen as the final cache
Caching
- Important principles at multiple levels (hardware, operating system, software) in a computer
- Temporarily used in slow storage information temporarily
- If there is information, then fast collection (cache) was checked to determine
- If so, then information directly from the cache (faster)
- If not, the data is copied into the cache and used there
- Cache is smaller than cache storage
- Cash Management Important Design Issues
- Cash size and replacement policy
Computer System Architecture
- Most systems use a single general purpose processor (PDA through mainframe)
- Most systems also have special purpose processors
- Multiprocessor systems are increasing in usage and importance
- Also known as parallel systems, tightly-coupled systems
Clustered System
- Like a multiprocessor system, but many systems are working together
- Commonly sharing storage via the storage-area network (SAN)
- Provides a high-availability service that avoids failures
- There is a machine in the hot-standby mode in asymmetric clustering
- Symmetric clustering has several nodes, which monitor each other
- Some clusters are for high-performance computing (HPC)
- Apps must be written to use parallelization
Operating System Architecture
- Multiprogramming is needed for efficiency
- A single user can not keep CPU and I / O devices busy at all times
- Organizes multiprogramming jobs (code and data), so the CPU always has the same
- A subset of total jobs in the system is kept in memory
- One job is selected and run through job scheduling
- When it has to wait (for example I / O), OS goes to another job
- Timesharing (multitasking) is a logical extension in which CPU users are employed so often
- Interacting with each task, creating interactive computing
- Response time must be <1 second
- Each user has at least one program performed in memory [process
- f many jobs are ready to run at the same time [CPU scheduling
- If the processes do not fit in memory, swapping takes them in and out to run them.
Operating System Operation
- Handheld Powered by Hardware
- Software error or request creates exceptions or traps
- Zero division, request for operating system service
- Other process problems include infinite loops, processes that modify one or the other operating system
- The dual-mode operation allows OS to protect itself and other system components
- User mode and kernel mode
- Provided by mode bit hardware
User Transitions in Kernel Mode
- Timer to prevent endless loop/process hogging resources
- Set interrupt after a specific period
- Operating system reduction counter
- When the counter zero creates an obstacle
- Set prior to the scheduled procedure before getting the prescribed control or eliminating the program that exceeds the allotted time.
Operating System Function
Process Management
- There is a program in process execution. It is a unit of work within the system. A program is a passive unit,
- A process is an active unit.
- The process requires resources to complete its work
- CPU, memory, I / O, files
- Initial data
- The need to recover any reusable resources for the end of the process
- In the single-threaded process, there is a program counter that is to specify the location of the next instruction to execute
- Process sequentially executes instructions until it is completed at one time
- In multi-threaded process per thread is a program counter
- Usually, there are several processes in the system, some users, some operating systems are running concurrently on one or the other
- More CPU
- Consciousness by multiplying the CPU into processes/threads
Process Management Activities
- The operating system is responsible for the following activities in relation to the process Management
- Creating and deleting both user and system processes
- Suspend and resume processes
- Providing mechanisms for process synchronization
- Providing mechanisms for process communication
- Providing mechanisms to combat deadlock
Memory Management
- All data in memory before and after processing
- To perform all the instructions in memory
- Memory management determines what is in memory when
- Optimize CPU usage and computer response for users
- Memory management activities
- Keep in mind, which parts of memory are currently being used and by whom it is being done
- Decide which process (or its parts) and data to move to memory
- Allocating and Dealing Memory Space as needed
- OS provides a similar, logical approach to information storage
- Logical storage unit physical properties - file
- Each medium is controlled by the device (i.e., disk drive, tape drive)
- Different properties include speed, capacity, data transfer rate, access method (sequential or). Random)
- File system management
- Files are usually organized in directories
- Access control on most systems to determine who can access
- OS activities are included
- Creating and deleting files and directories
- Primitives to manipulate files and diaries
- Mapping files on secondary storage
- Backup files on static (non-volatile) storage media
Mass Storage Management
- Usually, the disk is used to store data that does not fit in main memory or data that should be kept for "long" The period of time
- Proper management is of central importance
- The full speed of computer operation lies on the disk subsystem and its algorithm
- MASS STORAGE ACTIVITIES
- Free space management
- Storage allocation
- Disk scheduling
- Some storage is not fast enough
- Tertiary storage includes optical storage, magnetic tape
- Still needs to be managed
- The change between WORM (writing-once, read multiple times) and RW (read-write)
Performance of Various Stages of Storage
Migration in the Register from the Disk of Integer A
- The multitasking environment should be careful to use the most recent value, no matter where it is stored in Storage hierarchy
- Multiprocessor environment should provide cache compatibility in hardware such as all CPUs The most recent value in their cache
- The situation of a distributed environment is even more complex
- Many copies of datum may be present
I / O Subsystem
- One purpose of the OS is to hide the specificity of hardware devices from the user
- The I / O subsystem is responsible for
- Memory management of I / O including buffering (data is being temporarily stored while it is being transferred), Caching (storing parts of data in fast storage for display), spooling (overlapping of output) A job with the input of other jobs)
- Common Device-Driver Interface
- Drivers for specific hardware devices
Labels:
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Monday, 7 January 2019
What is Database(DBMS)?
The Database is a collection of related data and the data is a collection of facts and figures that can be processed to generate information.
Mostly data represents recordable facts. Data aids in production information, which is based on facts. For example, if we have data about the points obtained by all students, then we can conclude about the tops and the average points.
What is Database Management System?
A Database Management System (DBMS) stores the data in such a way that it is easy to retrieve, manipulate and produce information.
A Database Management System (DBMS) is a collection of programs that enables users to create
And maintain a database. According to the ANSI / SPARC DBMS Report (1977), a DBMS should be visualized as a multi-layered system.
Characteristics of Database Management System
Traditionally, data was organized in file formats. DBMS was then a new concept, and all research was done to overcome the shortcomings in the traditional style of data management. A modern DBMS has the following features:
Real-World Entity: A modern DBMS is more realistic and uses real-world organizations to design its architecture. It also uses behaviors and specialties. For example, a school database can be used as an attribute for students as a unit and their age.
Relationship-Based Tables: DBMS allows organizations and relationships to create tables. A user can understand the architecture of the database only by looking at the names of the table.
Isolation of Data and Applications: A database system is completely different from its data. A database is an active unit, whereas the data is called inactive, on which the database works and organizes. DBMS also stores metadata about data to make its process easier.
Less Redundancy: DBMS adheres to the rules of generalization, which divides a relationship when its attribute values are redundant. Generalization is a mathematically rich and scientific process that reduces data redundancy.
Consistency: Consistency is a state where each relationship is consistent in a database. There are methods and techniques that can detect an effort to leave the database in an inconsistent state.
A DBMS can provide more stability than the older forms of data storage Applications like file-processing systems
Query Language: Equipped with the DBMS query language, which makes the data more efficient to retrieve and manipulate Can apply as a user.
Many more different filtering options as needed to retrieve a set of data. Traditionally, this was not possible where the file-processing system was used.
ACID Properties: DBMS follows the concepts of atomicity, consistency, isolation, and durability. These concepts Applicable to transactions, which manipulate data in a database.
ACID properties help the database to be healthy in multi-transaction environments and in case of failure.
Multi-user and Concurrent Access: DBMS supports multi-user environments and allows them to access and manipulate data in parallel.
However, when users try to handle the same data items, transactions are banned, but users are always unaware of them.
Many Ideas: DBMS presents many ideas for different users. A user who is in the sales department will have a different view of the database compared to the person working in the production department. This feature enables users to have a focused perspective of the database
Requirements.
Security: Features like many ideas provide some degree of security, where users are unable to access data from other users and departments.
DBMS provides ways to apply the barriers to data entering and later retrieving data in a single stage. DBMS offers many Different levels of security features, which enable many users to think differently with different attributes.
For example, a user of the sales department cannot see the data that the purchasing department has. In addition, it can also be handled that how much data is sold
The department should be displayed to the user. Since DBMS has not been saved on the disk as a traditional file system, it is very difficult to break the code for miscreants.
Multi-user and Concurrent Access: DBMS supports multi-user environments and allows them to access and manipulate data in parallel.
However, when users try to handle the same data items, transactions are banned, but users are always unaware of them.
Many Ideas: DBMS presents many ideas for different users. A user who is in the sales department will have a different view of the database compared to the person working in the production department. This feature enables users to have a focused perspective of the database
Requirements.
Security: Features like many ideas provide some degree of security, where users are unable to access data from other users and departments.
DBMS provides ways to apply the barriers to data entering and later retrieving data in a single stage. DBMS offers many Different levels of security features, which enable many users to think differently with different attributes.
For example, a user of the sales department cannot see the data that the purchasing department has. In addition, it can also be handled that how much data is sold
The department should be displayed to the user. Since DBMS has not been saved on the disk as a traditional file system, it is very difficult to break the code for miscreants.
Uses of Database
A specific DBMS has users with different rights and permissions that use it for different purposes. Some user retrieves data and some do it back. Users of DBMS can be broadly classified as follows:
Administrator: Administrators: Administrators maintain DBMS and are responsible for the management of the database. They are responsible for taking care of it.
Use and by whom it should be used. They create an access profile for users and apply limitations to maintain isolation and security.
Administrators also keep track of system licenses, essential equipment, and other software and hardware related maintenance such as DBMS resources.
Designers: Designers are a group of people who actually work on the designing part of the database. What data do they keep an eye on And in what format should be kept? They identify and design the entire set of institutions, relationships, obstacles, and ideas.
End User: The end users are those who actually receive the benefits of being DBMS. End users can take from simple viewers who pay attention.
Logs or market rates for sophisticated users, such as business analysts.
Architecture of Database
DBMS's design depends on its architecture. It can be centralized or decentralized or categorized. The architecture of DBMS can be seen as a single-level or multi-level. The N-Tier architecture divides the entire system into related but independent N modules, which can be freely modified, modified, modified, or replaced.
In 1-Level Architecture, DBMS is the only unit where the user sits directly on DBMS and uses it. Any changes made here will be done directly on DBMS. It does not provide useful tools for end-users. Database designers and programmers generally prefer to use single-tier architecture.
If the architecture of DBMS is 2-Level Architecture, then he should have an app through which DBMS can be accessed. Programmers use a 2-level architecture where they reach DBMS through an application. In the case of operation, design, and programming, the application is completely free from the tier database.
3-Level Architecture
3-level architecture separates their levels from each other based on the complexity of users and how they use the data contained in the database. This is the most widely used architecture for designing a DBMS.
Database (Data) Tier: At this stage, the database stays with its query processing languages. We also have relationships that define
At this level the data and their obstacles
Application (Middle) Tier: At this level, the application resides to the server and databases. For a user, this app presents an abstract view of the tier database. The end-users are unaware of any existence of the database beyond the application. At the other end, the database tier is not aware of any other user beyond the application tier. Therefore, the application layer sits in the middle and acts as an intermediary between the end-user and the database.
User Tier: End-users work on this tier and they do not know anything about any existence of the database beyond this layer. on this Layer, many views of the database can be provided by the application. All ideas are generated by application-oriented applications.
The multi-tier database architecture is highly variable because almost all of its components are free and can be changed independently.
Database Moduls
Data models define how the logical structure of a database is prepared. Data models are the basic institutions for implementing abstraction in a DBMS. Data models define how the data is connected to each other and how they are processed and stored inside the system.
Long ago data models could be flat data-models, where all the data used to be kept in the same plane. Earlier, the data models were not so scientific, so they were at risk of introducing many duplication and discrepancies.
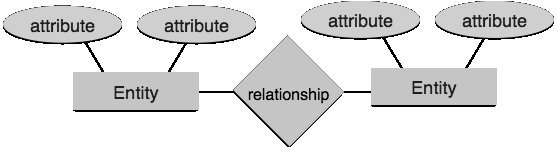
Entity-Relationship Modul
The entity-relationship (ER) model is based on the real world institutions and the perception of the relationship between them. While preparing the real-world scenario in the database model, the ER model creates unit sets, connection sets, general characteristics, and constraints.
The ER model is best used for the conceptual design of a database.
ER Model is based on:
- Institutions and their properties.
- Relations between institutions.
These concepts are explained below.
Entity
In the ER model, a unit is a real-world unit, which has properties. Each attribute is defined by a group of values named domain.
For example, in a school database, a student is considered to be a unit. A student has different characteristics such as name, age, class etc.
Relationship
A logical connection between institutions is called relationship. Relationships are mapped to institutions in various ways. Mapping Cardinalities define the number of engagement between the two entities.
Mapping Cardinality:
- O one to one
- O multiple
- O many
- Many O
Relational Modul
The most popular data model in DBMS is the Relational Model. This is a more scientific model than others. This model is based on first-order logic and defines a table as N-Aryan connection.
The main attractions of this model are:
- Data is stored in tables, which are called relationships.
- Relations can be normalized.
- In generalized relationships, the value of the value being atomic value.
- In a relationship, each line has a unique value.
- In a relationship, the domain each column contains values for the same domain.
Database Schema
A database schema is a skeleton structure that represents the logical approach of the entire database. It defines how the data is systematic and how the relationship is related to them. It prepares all the obstacles that have to be applied to the data.
A database schema defines the relationships between your entities and theirs. It has a descriptive description of the database, which can be represented through schema diagrams. This is a database designer that designs schemas to help programmers understand the databases and make it useful.
A database schema can be broadly divided into two categories:
Physical Database Schema: This schema relates to the actual storage of data and its storage such as files, indexes etc. It defines how the data will be stored in secondary storage.
Logical Database Schema: This schema defines all logical constraints that need to be applied to stored data. It defines tables, ideas and integrity barriers.
Database Instance
It is important that we define these two words differently. The database schema is the skeleton of the database. It is prepared when the database does not exist at all. Once the database is turned on, it is very difficult to make any changes in it. There is no data or information in a database schema.
A database example is a position of operating database with data at any time. It includes a snapshot of the database. Examples of database change over time. A DBMS ensures that every instance (status) of it is in a valid state, which is followed by database designers following all assumptions, constraints, and conditions.
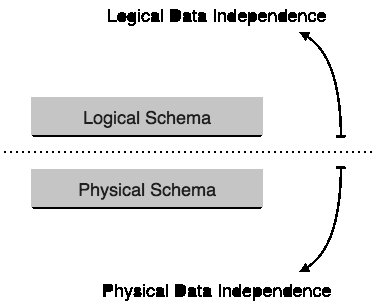
Database Independence
Database systems typically have a lot of data in addition to users' data. For example, it stores data about data, known as metadata, to easily detect and retrieve data. It is difficult to modify or update a set of metadata after it is stored in the database. But as DBMS is expanding, it needs to be changed over time to meet the needs of users. If the whole data is dependent, then it will become a tedious and highly complex task.
Metadata itself follows a layered architecture so that when we change the data on one layer, it does not affect the data at the other level. This data is free but is mapped to each other.
Logical Database Independence
The data about the logical data database, i.e., stores information about how the data is managed in. For example, a table (relation) stored in the database and all its relation is applicable to that relationship.
Logical data freedom is a kind of mechanism, which makes itself generous with the actual data stored on disk. If we make some changes to the table format, then it should not change the data on the disk.
Physical Database Independence
All schemas are logical, and actual data is stored in disk format on a bit. Physical data is the power to change physical data without affecting the independence schema or logical data.
For example, if we want to change or upgrade the storage system ourselves - then suppose we want to replace the hard disk with the SSD - its logical data or schema should not have any effect. can provide more stability than the older forms of data storage Applications like file-processing systems
Labels:
Database
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Thursday, 3 January 2019
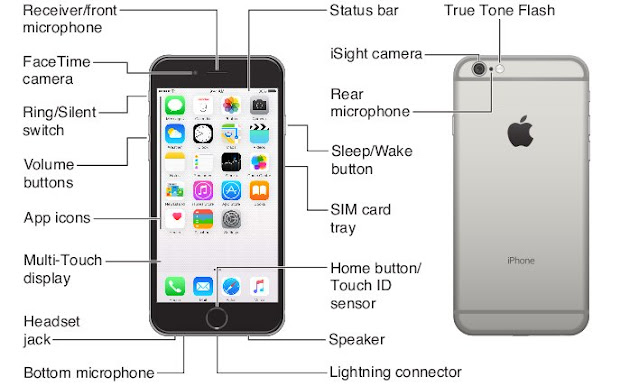
iPhone Tips and Tricks
iPhone OverviewThis guide describes iOS 8.4:
- iPhone 6
- iPhone 6 Plus
- iPhone 5s
- iPhone 5C
- iPhone 5
- iPhone 4S
iPhone Tips and Tricks for Beginners
Your location, language, and carrier To find out what features are supported in your area see
iPhone Accessories
The following items are included with theApple Headset
Connecting Cable
Apple USB Power Adapter
SIM Eject Tool
Multi-Touch Screen
Some simple gestures - Tap, Drag, Swipe, and Pinch - all you need to use the
Most of the buttons you use with the
When you are not using an
Displaying for sleep saves battery, and prevents you from doing anything if you touch Screen. You can still get
In
On the previous
If you do not touch the screen for a minute or so, the
Go to
Turn on
Close the
Slider.
For added security, you may need a passcode to unlock the iPhone. Go to
And
Home Button
The Home button takes you to the Home screen and offers other convenient shortcuts. On Home screen, tap on any app to open it.
See apps you opened. Double-click the Home button when the
Use Siri or Voice Control. Press and hold the Home button.
On the
Fingerprint instead of using your passcode or Apple ID password to unlock or create iPhone
Shopping in the iTunes Store, App Store, and iBook Store.
if you have
Apple payments are made to shop in one store or from within the app.
Control the Volume
When you're on a phone or listening to songs, movies, or other media, the button Adjust the audio volume of the iPhone. Otherwise, buttons control the volume for the ringer, Alerts, and other sound effects.
Lock the ringer and alert volume. Go to
To limit the volume for music and video, go to
Use the Control Center to adjust the volume. When the
Swipe up from the bottom edge of the screen to open the application, Control Center.
You can either use the volume button to take a picture or record a video.
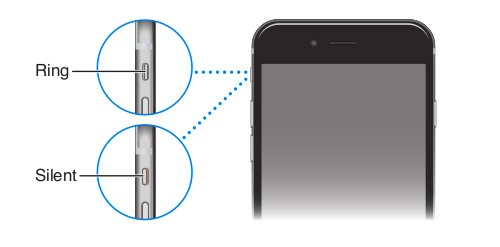
Ring/silent switch
Flip the ring / silent switch to insert the iPhone into ring mode or silent mode.
In-ring mode, the
Use do not disturb. You can also silence calls, alerts, and notifications using Do Not Disturb.
Swipe up from the bottom edge of the screen to open the Control Center,
Sim Card
If you have been given a SIM card to install, install it before installing the
How to Set Up iPhone
You can set up an
Set up iPhone:
The Setup Assistant passes through this process, which includes:
- Connecting to Wi-Fi networks
- Signing in with a free apple id or making (Required for many features including Icloud, FaceTime, iTunes Store, App Store, and more)
- Enter passcode
- Establishment of Icloud and Icloud Keychain
- Turn on Recommended Features like Location Services
- Adding a credit or debit card to the passbook for use with Apple Pay (iPhone 6 or iPhone 6 Plus)
- Activating the iPhone with your career
How to Connect to Wi-Fi on iPhone
It appears at the top of the screen, then you are connected to a Wi-Fi network. Whenever you return to the same place, the iPhone then reunites
Configure Wi-Fi:
- Select a network: Tap one of the listed networks, then enter the password if asked.
- Ask to join the network: On the Wi-Fi network when available, turn on Ask to Join Network. Otherwise, you should be manually involved in a network if the network you are already using is not available.
- Join a closed Wi-Fi network: Tap another, then enter the name of the closed network. You need to know the network name, security type, and password.
- Adjust settings for Wi-Fi networks: Tap next to the network. You can set up an HTTP proxy, define the static network settings, turn on the bootup, or renew the settings provided by the DHCP server.
- Forget a network: Tap next to the network you've already added, then forget this network.
Manage an AirPort network:
Connect to the Internet on iPhone
iPhone
When an app needs to use the Internet, then the
- Uses the most recently available Wi-Fi network
- Shows a list of Wi-Fi networks in range, and adds by using the one you've chosen
- Adds cellular data to the network if available
If you already have an Apple ID, then use it when you set up an iPhone for the first time, and whenever you need to sign in to use the Apple service. If you do not have an Apple ID already, you can create one whenever you ask to sign in. You only need an Apple ID for whatever you have to do with Apple.
For more information, see
What is iCloud in iPhone
iCloud offers free mail, contacts, calendars, and other features, which you can set up only by signing in to iCloud with your Apple ID, then make sure the features you want to use are turned on.
Set up iCloud. Go to
iCloud stores your photos and videos, documents, music, calendars, contacts, and more. The contents stored in iCloud are pushed wirelessly in the iCloud signed on your other iOS devices and computers with the same Apple ID.
iCloud is available on PC with iOS 5 or later on OS X Lion v10.7.5 or later on Mac computers and with Windows 4.0 (iCloud for Windows 7 or Windows 8). You can sign in to iCloud.com from any Mac or PC to access your iCloud information and features like Photos, Find My iPhone, Mail, Calendar, Contacts, iWork for iCloud, and more.
iCloud Features Include:
- Automatically purchase iTunes on all your devices installed with iCloud, or download the purchase of past iTunes music and TV shows for free: music, movies, TV shows, apps, and books. With the membership of iTunes Match, all your music, in which you are imported from CD or purchased somewhere other than iTunes Store, can also be stored in iCloud and played on demand. Download Previous App Store And iBooks Store for shopping free, anytime for iPhone
- Photo: Use iCloud Photo Library to store all your photos and videos in iCloud, and use them from any iOS 8.1 or later devices, Mac OS X Yosemite v10.10.3 or later and using the same Apple ID Access iCloud.com Use iCloud photo-sharing to share photos and videos with just those people, and let them add photos, videos, and comments.
- Family sharing: Six family members can share their shopping with the iTunes Store, App Store, and iBooks Store. Pay for a family purchase with a single credit card and consider the expenses of children from parents' devices right. Plus, share photos, a family calendar, and more.
- iCloud Drive: Securely store your presentations, spreadsheets, PDFs, images, and other documents in iCloud, and access them on your iPhone, iPad, iPod Touch, Mac, or PC. iCloud Drive is available on any iOS 8 or later device and OS X Yosemite v10.10.0 or later on any Mac. if
- You are using the old version of iOS
- Mail, Contacts, Calendar: Keep your mail, contacts, calendar, notes, and reminders on all your devices.
- Safari Tabs: View tabs you've opened on your other iOS devices and OS X computers. Browse the Web on page 64.
- Backup: When connecting to power and Wi-Fi, the iPhone automatically backs up from iCloud. The iCloud data and backups sent over the Internet are encrypted.
- Find my iPhone: Find your iPhone on a map, display a message, play a sound, lock the screen, temporarily suspend or remove your credit or debit card in the passbook used for Apple Pay or give your iPhone data to Remotely erase. Find My iPhone includes an activation lock, which
- Your Apple ID and password are required to close Find My iPhone or erase your device.
- Your Apple ID and Password are also required before you can reactivate your iPhone.
- Find My Friends: Share your location with those who are important to you. Download the free app from the App Store.
- iCloud Keychain: Keep your password and credit card information on all your named devices. You must have an iCloud account and sign in to iCloud to use Apple Pay.
How to Connect iPhone to Computer
By connecting your iPhone to your computer, you can sync content from your computer using iTunes
To use the iPhone with your computer, you need:
- An Internet connection to your computer (Broadband is recommended)
- A Mac or a PC with a USB 2.0 or 3.0 port, and one of the following operating systems:
- OS X version 10.6.8 or later
- Service Pack 3 or later Windows 8, Windows 7, Windows Vista, or Windows XP Home or Professional
Connect the iPhone to your computer:
Sync with iTunes
Syncing with iTunes copies the information from your computer to the iPhone and vice versa. You can sync by connecting the iPhone to your computer, or you can set iTunes to sync wirelessly with Wi-Fi. You can set iTunes to sync music, video, apps, photos, and more. To help synchronize the iPhone, open iTunes on your computer, choose Help> iTunes Help, then Sync your iPod, iPhone or iPad. iTunes is available at www.itunes.com/download/.
Set up Wireless Syncing:
If Wi-Fi sync is on, then when the iPhone is connected to a power source, both the iPhone and your computer are connected and connected to the same wireless network, and iTunes is open on your computer.
Tips for syncing with iTunes on your computer
Connect the iPhone to your computer, select it in iTunes, then set the options in the various pan.
- If the iPhone is not visible in iTunes, make sure that you are using the latest version of iTunes, check that the included cable is connected correctly, then try restarting your computer.
- In the summary page, you can set iTunes to automatically sync the iPhone when it is connected to your computer. When you attach the device, hold down Command and Option (Mac) or Shift and Control (PC) until you see the iPhone in the iTunes window, to temporarily stop syncing.
- In the summary pane, select "Encrypt iPhone Backup" if you want to encrypt the information stored on your computer when iTunes creates backups. Encrypted backups are indicated by a lock icon, and a password is required to restore the backup. If you do not select this option, other passwords (such as for mail accounts) are not included in the backup and if you use the backup to restore the iPhone, you will have to re-enter them.
- In the music pane, you can sync music using your playlists.
- In the Photo pane, you can sync photos and videos from a supported app or folder on your computer.
- If you use iCloud to store your contacts, calendars, and bookmarks, do not even sync them on the iPhone using iTunes.
- If you turn on the iCloud Photo Library, you can not use iTunes to sync photos and videos on the iPhone.
The iPhone works with Microsoft Exchange, and many most popular Internet-based emails, contacts and calendar services.
Install an account. Go to
If your company or organization supports it, you can add contacts using an LDAP or CardDAV account.
You can add calendars by using the CalDAV Calendar account, and you can subscribe to iCalendar (.ics) calendars or import them by mail.
For information about setting up a Microsoft Exchange account in a corporate environment,
Manage content on your iOS devices
You can transfer information and files between your iOS devices and computers using iCloud or iTunes.
iCloud stores your photos and videos, documents, music, calendars, contacts and more. All these other iOS devices and computers are pushed wirelessly, keeping everything up to date.
iTunes syncs music, videos, photos, and more between your computer and iPhone. When you sync, the changes you make on one device are copied to the other. You can also use iTunes to sync files and documents.
Depending on your requirements, you can use iCloud or iTunes or both. For example, you can use iCloud to automatically keep your contacts and calendars on all your devices, and iTunes can be used to sync music to your iPhone from your computer.
You can manually manage content from iTunes in the tool pane of the device. This lets you add songs and videos by selecting a song, video, or playlist from your iTunes library and then dragging it into your iPhone in iTunes. This is useful if there is the stuff that fits on your device in your iTunes Library.
Date and Time
Normally you have a date and time based on your location - take a look at the lock screen whether they are correct or not.
Determine whether the iPhone automatically updates the date and time. Go to Settings> General> Date and time, then turn the setting on or off automatically. If you set the iPhone to automatically update the time, it receives the right time on the cellular network and updates it for the time zone.
You are inside Some carriers do not support network time, so in some areas, the iPhone may not be able to automatically set the local time.
Manually set dates and times. Go to Settings> General> Date and Time
Set whether the iPhone shows a 24-hour time or 12-hour time. Go to Settings> General> Date and Time, then turn 24-hour time on or off. (24-hour time may not be available in all areas.)
Apple Watch
Use the Apple Watch app (not available in all areas) to learn more about apple watch, and to pair your Apple Watch with an iPhone. Simply tap on the Apple Watch app, and follow the onscreen instructions.
International Settings
Go to
Your iPhone Name
The name of your
Visit this user guide on iPhone
You can see the User guide in the iPhone user guide and iBook app on iPhone in iPhone. The user guide sees Safari Tap, then tap the iPhone User Guidebook. (If you do not see any bookmarks, go to help.apple.com/iphone/)
Tips for using iOS
If your company or organization supports it, you can add contacts using an LDAP or CardDAV account.
You can add calendars by using the CalDAV Calendar account, and you can subscribe to iCalendar (.ics) calendars or import them by mail.
For information about setting up a Microsoft Exchange account in a corporate environment,
Manage content on your iOS devices
You can transfer information and files between your iOS devices and computers using iCloud or iTunes.
iCloud stores your photos and videos, documents, music, calendars, contacts and more. All these other iOS devices and computers are pushed wirelessly, keeping everything up to date.
iTunes syncs music, videos, photos, and more between your computer and iPhone. When you sync, the changes you make on one device are copied to the other. You can also use iTunes to sync files and documents.
Depending on your requirements, you can use iCloud or iTunes or both. For example, you can use iCloud to automatically keep your contacts and calendars on all your devices, and iTunes can be used to sync music to your iPhone from your computer.
You can manually manage content from iTunes in the tool pane of the device. This lets you add songs and videos by selecting a song, video, or playlist from your iTunes library and then dragging it into your iPhone in iTunes. This is useful if there is the stuff that fits on your device in your iTunes Library.
Date and Time
Normally you have a date and time based on your location - take a look at the lock screen whether they are correct or not.
Determine whether the iPhone automatically updates the date and time. Go to Settings> General> Date and time, then turn the setting on or off automatically. If you set the iPhone to automatically update the time, it receives the right time on the cellular network and updates it for the time zone.
You are inside Some carriers do not support network time, so in some areas, the iPhone may not be able to automatically set the local time.
Manually set dates and times. Go to Settings> General> Date and Time
Set whether the iPhone shows a 24-hour time or 12-hour time. Go to Settings> General> Date and Time, then turn 24-hour time on or off. (24-hour time may not be available in all areas.)
Apple Watch
Use the Apple Watch app (not available in all areas) to learn more about apple watch, and to pair your Apple Watch with an iPhone. Simply tap on the Apple Watch app, and follow the onscreen instructions.
International Settings
Go to
- Language for iPhone
- Preferred language order for apps and websites
- region format
- Calendar formats
- Advanced settings for date, time and numbers
Your iPhone Name
The name of your
Visit this user guide on iPhone
You can see the User guide in the iPhone user guide and iBook app on iPhone in iPhone. The user guide sees Safari Tap, then tap the iPhone User Guidebook. (If you do not see any bookmarks, go to help.apple.com/iphone/)
- Add an icon for the User Guide on Home Screen: Tap, then tap Add to Home Screen.
- See User Guide in a Different Language: Tap Change Language at the bottom of the home page.
Tips for using iOS
- The Tips app helps you get the most from the iPhone.
- Get tips. Open the Tips app. New tips are added weekly.
- Notify when new suggestions arrive. Go to
Labels:
iPhone
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Wednesday, 2 January 2019
How to Protect Your Computer from Viruses, Malware, and Hackers
Today, more and more people are using their computer for everything from communication to online banking and from investment to shopping.
As we do these things on a more regular basis, we open ourselves up to potential hackers, attackers and crackers. While some may see your personal information and identity for resale, others just want to use your computer as a platform, from which to attack other unknowable goals.
Below are some easy, cost-effective steps that you can Protect Your Computer from Viruses safer to start:
1. Always back Up important information and store it at a safe location other than your computer.
2. Update and pour your operating system, web browser and software frequently. If you have a Windows operating system, start by running the Update Wizard by going to https://www.catalog.update.microsoft.com/Home.aspx.
This program will help you find the latest patches for your Windows computer. Also, visit https://www.microsoft.com/en-us/download/office.aspx and locate a potential patch for your office programs.
3. Install a firewall. Without a good firewall, viruses, worms, trojans, malware, and adware can easily access your computer from the Internet. The advantages and disadvantages of hardware and software based firewall programs should be considered.
4. Review your browser and email settings for optimal security. Why should you do this? ActiveX and Javascript are often used by hackers
Root malicious programs into your computer. While cookies are relatively harmless in terms of safety concerns, they still track your movements on the Internet to create your profile. For at least "Internet Zone" set your security setting at high, and your "trusted sites zone" to take the media.
5. Install anti-virus software and set for automatic updates so that you get the most current version.
6. Do not open anonymous email attachments. It's simply not enough that you can identify the address from which it is generated because many viruses can spread from a familiar address.
7. Do not run programs from unknown origin. Also, do not send such programs to friends and colleagues because they contain fun or entertaining stories or jokes. They may have a Trojan horse waiting for the computer to be infected.
8. Disable hidden filename extensions. By default, the Windows operating system is set to "Hide file extensions for known file types". Disable this option so that the file extension appears in Windows. Some file extensions will continue to be hidden, by default, but you are likely to see any unusual file extensions that are not related.
9. Turn off your computer and disconnect it from the network if not using the computer. When you are a hacker can not attack your computer
1. Always back Up important information and store it at a safe location other than your computer.
2. Update and pour your operating system, web browser and software frequently. If you have a Windows operating system, start by running the Update Wizard by going to https://www.catalog.update.microsoft.com/Home.aspx.
This program will help you find the latest patches for your Windows computer. Also, visit https://www.microsoft.com/en-us/download/office.aspx and locate a potential patch for your office programs.
3. Install a firewall. Without a good firewall, viruses, worms, trojans, malware, and adware can easily access your computer from the Internet. The advantages and disadvantages of hardware and software based firewall programs should be considered.
4. Review your browser and email settings for optimal security. Why should you do this? ActiveX and Javascript are often used by hackers
Root malicious programs into your computer. While cookies are relatively harmless in terms of safety concerns, they still track your movements on the Internet to create your profile. For at least "Internet Zone" set your security setting at high, and your "trusted sites zone" to take the media.
5. Install anti-virus software and set for automatic updates so that you get the most current version.
6. Do not open anonymous email attachments. It's simply not enough that you can identify the address from which it is generated because many viruses can spread from a familiar address.
7. Do not run programs from unknown origin. Also, do not send such programs to friends and colleagues because they contain fun or entertaining stories or jokes. They may have a Trojan horse waiting for the computer to be infected.
8. Disable hidden filename extensions. By default, the Windows operating system is set to "Hide file extensions for known file types". Disable this option so that the file extension appears in Windows. Some file extensions will continue to be hidden, by default, but you are likely to see any unusual file extensions that are not related.
9. Turn off your computer and disconnect it from the network if not using the computer. When you are a hacker can not attack your computer
Disconnected from the network or computer.
10. Consider making boot disks on floppy disks if your computer is compromised by malfunctioning or malicious programs. Obviously, you need to take this step before experiencing the hostile violation of your system.
Spam
A key point that needs to be discussed: Spam is now getting more and more numbers from other countries. These emails are hard to fight because they come from outside our country's laws and regulations. Because the Internet opens borders and thinks globally, these laws are fine and good but do not stop the problem.
Number 1: What you can do to avoid having your email address on the Internet.
There are products called "Spam Spider" which send emails to search the email on an email address. If you are interested, do a search on "Spam Spider" and be amazed at what you get. Interestingly, WebPoison.org, a site that is open source, is ready to fight Internet "Spambots" and "Spam Spider", which gives them a bogus HTML web page, which contains fake email addresses. Are there.
Some suggestions for you:
Number 2: Get a spam blocking software.
There are several programs for this. (For example, visit https://www.cloudmark.com/en or https://www.mailwasher.net ). You can also buy a professional version. Whatever you do, get the software. This will save you time. The software is not silly, but they really help. You'll usually have to set up some manual to block certain types of emails.
Number 3: Use multiple email address approaches.
There should be a lot of free email addresses. If you want to subscribe to newsletters, then there should be a "backup" email address. It will be like giving your phone number to your best friends and all else to get a business number.
Number 4: Attachments to people you do not know, BAD, BAD, BAD
A common problem with spam is that they have attachments and there may be viruses in the attachment. Corporations often have filters that do not let such things happen to you. There is far more "open country" for individual email spammers. A general rule of thumb: If you do not know who is sending you, then ignore this topic. Secondly, look for services offering to filter. Firewall vendors also offer this type of service.
Number 5: Email services now have "bulk-mail" baskets.
If you currently use, it does not support it, then think about going to a new gender. The concept is simple. If you know someone, they can send you an email. If you do not know them, then put them in bulk email piles and then "select" to allow them in your circle. This is a concept in spam blocking software, but additional layers seem important these days, so it is worth seeing.
Spyware and Adware
Spyware and adware are not only a growing nuisance for computer users everywhere but also a fast-growing industry.
Where does it come from?
Generally, spyware is produced in three ways. The first and most common method is when the user installs it. In this scenario, spyware is embedded, attached or bundled with freeware or shareware programs without user knowledge. The user downloads the program to his computer.
10. Consider making boot disks on floppy disks if your computer is compromised by malfunctioning or malicious programs. Obviously, you need to take this step before experiencing the hostile violation of your system.
Spam
A key point that needs to be discussed: Spam is now getting more and more numbers from other countries. These emails are hard to fight because they come from outside our country's laws and regulations. Because the Internet opens borders and thinks globally, these laws are fine and good but do not stop the problem.
Here are the Top 5 Rules to Protect Against Spam:
Number 1: What you can do to avoid having your email address on the Internet.
There are products called "Spam Spider" which send emails to search the email on an email address. If you are interested, do a search on "Spam Spider" and be amazed at what you get. Interestingly, WebPoison.org, a site that is open source, is ready to fight Internet "Spambots" and "Spam Spider", which gives them a bogus HTML web page, which contains fake email addresses. Are there.
Some suggestions for you:
- Use the form email, which can hide the addresses or even
- To help fight the problem, use addresses like sales@company.com instead of your full address.
- There are programs that encode your emails, such as jsGuard, that encode your email address on web pages so that spam spiders find it difficult or impossible to read your email address.
Number 2: Get a spam blocking software.
There are several programs for this. (For example, visit https://www.cloudmark.com/en or https://www.mailwasher.net ). You can also buy a professional version. Whatever you do, get the software. This will save you time. The software is not silly, but they really help. You'll usually have to set up some manual to block certain types of emails.
Number 3: Use multiple email address approaches.
There should be a lot of free email addresses. If you want to subscribe to newsletters, then there should be a "backup" email address. It will be like giving your phone number to your best friends and all else to get a business number.
Number 4: Attachments to people you do not know, BAD, BAD, BAD
A common problem with spam is that they have attachments and there may be viruses in the attachment. Corporations often have filters that do not let such things happen to you. There is far more "open country" for individual email spammers. A general rule of thumb: If you do not know who is sending you, then ignore this topic. Secondly, look for services offering to filter. Firewall vendors also offer this type of service.
Number 5: Email services now have "bulk-mail" baskets.
If you currently use, it does not support it, then think about going to a new gender. The concept is simple. If you know someone, they can send you an email. If you do not know them, then put them in bulk email piles and then "select" to allow them in your circle. This is a concept in spam blocking software, but additional layers seem important these days, so it is worth seeing.
Spyware and Adware
Spyware and adware are not only a growing nuisance for computer users everywhere but also a fast-growing industry.
Where does it come from?
Generally, spyware is produced in three ways. The first and most common method is when the user installs it. In this scenario, spyware is embedded, attached or bundled with freeware or shareware programs without user knowledge. The user downloads the program to his computer.
Once downloaded, the spyware program goes to collect data for the personal use of spyware authors or to sell it to a third party. Beware of several P2P file-sharing programs. They are notorious for downloads that keep spyware programs.
The user of a downloadable program should pay extra attention to the licensing agreement. Often the software publisher will warn the user that a spyware program will be installed along with the requested program.
Some agreements can provide special "opt-out" boxes that users can click to prevent spyware from being included in the download. Be sure to review the document before signing the download.
Another way is that spyware can access your computer, which can deceive you by manipulating the security features designed to stop any unwanted installation. The Internet Explorer web browser was designed to not allow websites to launch any unwanted downloads. This is the reason that the user has to start the download by clicking on a link. These links can prove confusing.
The user of a downloadable program should pay extra attention to the licensing agreement. Often the software publisher will warn the user that a spyware program will be installed along with the requested program.
Some agreements can provide special "opt-out" boxes that users can click to prevent spyware from being included in the download. Be sure to review the document before signing the download.
Another way is that spyware can access your computer, which can deceive you by manipulating the security features designed to stop any unwanted installation. The Internet Explorer web browser was designed to not allow websites to launch any unwanted downloads. This is the reason that the user has to start the download by clicking on a link. These links can prove confusing.
For example, pop-ups created after a standard Windows dialog box can appear on your screen. The message can ask if you want to optimize your internet access. It provides yes or no reply button, but, no matter what push you to push, a download containing a spyware program will begin. New versions of Internet Explorer are making this spyware route a bit more difficult now.
Finally, some spyware applications infect a system by attacking security holes in web browsers or other software. When a user navigates to a webpage controlled by a spyware author, the page contains a code designed to attack the browser and forces the installation of spyware programs.
What can spyware programs do?
Spyware programs can cater to a multitude of malicious tasks. Some of his work is annoying for the user; Others may be quite aggressive in nature.
Spyware can:
Finally, some spyware applications infect a system by attacking security holes in web browsers or other software. When a user navigates to a webpage controlled by a spyware author, the page contains a code designed to attack the browser and forces the installation of spyware programs.
What can spyware programs do?
Spyware programs can cater to a multitude of malicious tasks. Some of his work is annoying for the user; Others may be quite aggressive in nature.
Spyware can:
- Monitor your keystrokes for reporting purposes.
- Scan the files located on your hard drive.
- Snoop through the app on our desktop.
- Install other spyware programs in your computer.
- Read your cookies.
- Steal credit card numbers, passwords, and other personal information
- Change the default settings on your home page web browser.
Labels:
Computer Tricks
 Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.
Hi'i'm Rahim Ansari ,from India, I Love to Blogging, Desing Website, Web Developing and Desiging I Like to Learn and share Technical Hacking/Security tips with you,I Love my Friends.